Is AWS Cognito a Good Fit for B2B SaaS in 2026?

AWS Cognito is rarely chosen casually. Most B2B SaaS teams using Cognito today made a reasonable, even obvious decision: it was available, AWS-native, and solved authentication early without slowing product delivery.
The tension usually shows up later, not when login breaks, but when identity becomes a scaling constraint. By the time teams start asking whether Cognito is still the right fit, they are usually dealing with:
- Enterprise SSO and SCIM requirements
- Increasingly complex multi-tenant authorization
- APIs, integrations, and machine identities
- AI agents acting as first-class actors inside the product
At that point, authentication is no longer just “auth”.
It’s becoming an identity system, often one the product team is unintentionally building themselves.
This article is written for teams already running AWS Cognito in production and trying to understand whether the friction they’re feeling is accidental or structural.
Why AWS Cognito Works Well at the Start
AWS Cognito is designed around a clear and focused abstraction: user authentication.
At its core, Cognito provides a managed way to:
- Authenticate users
- Issue standards-compliant tokens
- Store credentials securely
- Integrate tightly with AWS infrastructure
For early-stage B2B products, this is often enough. Identity boundaries are simple, roles are limited, and most authorization decisions can live comfortably inside application code.
Cognito works well in this phase because it avoids opinionated product-level identity modeling. It gives teams primitives, not workflows.
That strength becomes a limitation as the product evolves.
How B2B SaaS Identity Changes as Products Scale
B2B SaaS does not scale linearly in users, it scales in organizational complexity.
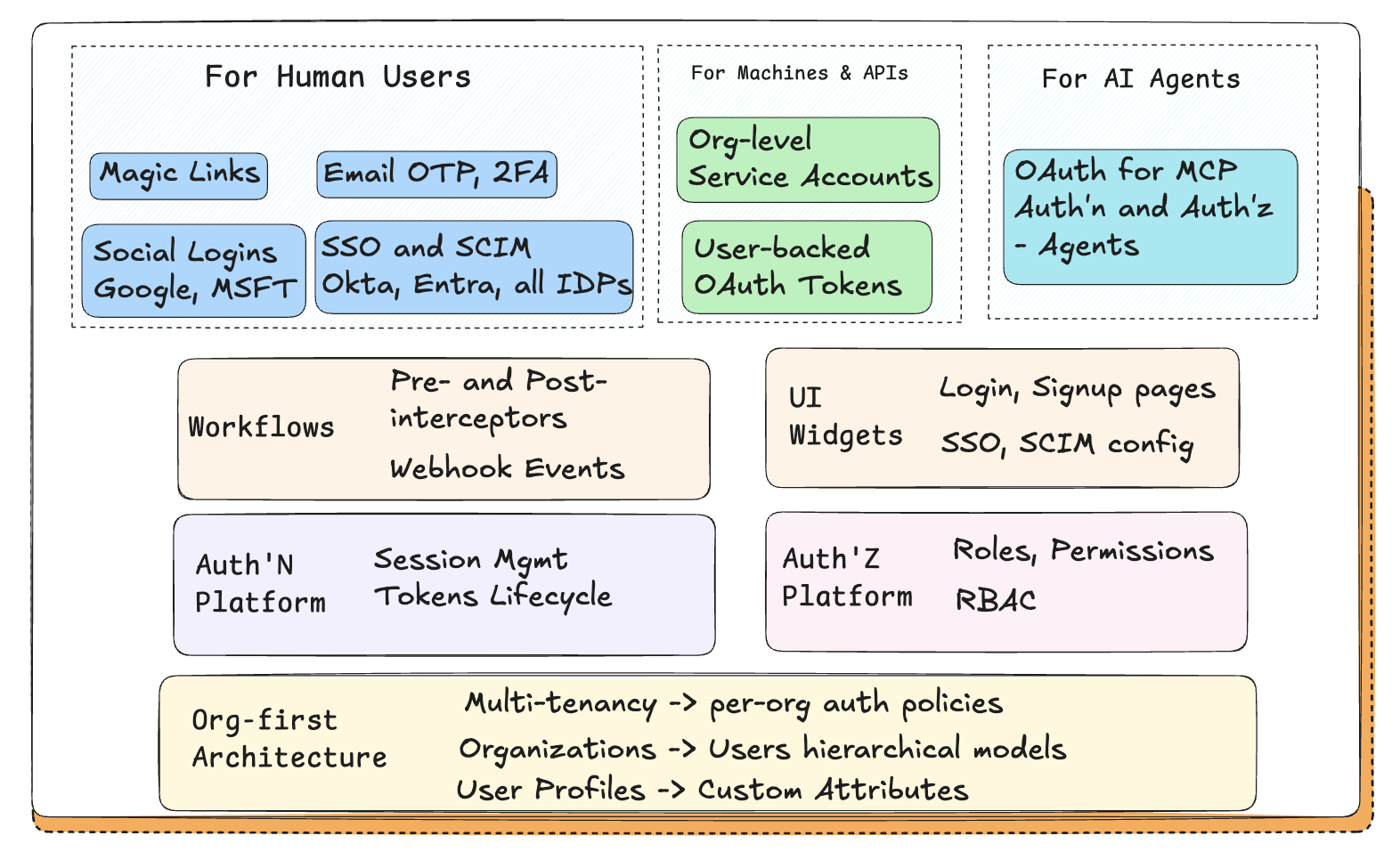
Identity in B2B SaaS is organizational, not individual
Enterprise customers do not think in terms of users.
They think in terms of companies, tenants, and internal boundaries.
That shift introduces identity requirements that are fundamentally different from consumer or SMB products:
- Users belong to organizations
- The same user may belong to multiple organizations
- Roles are defined per organization
- Policies are enforced at the tenant boundary
Once these concepts exist, identity can no longer be treated as “user + token”.
SSO and SCIM expose the limits of a user-first model
SSO and SCIM are often the first inflection point.
Cognito supports SAML and OIDC, but configuration lives at the user pool or app client level. There is no native concept of:
- Org-specific auth configuration
- Tenant-level identity providers
- Customer-managed admin surfaces
As a result, teams begin orchestrating:
- IdP routing logic
- Tenant discovery
- Provisioning flows
- Customer-facing admin experiences
At this stage, auth stops being infrastructure and starts becoming product surface area.
Machine identity and agents introduce a second identity system
Modern B2B products are no longer purely human-driven.
APIs, integrations, background jobs, and AI-powered features introduce non-human actors that still need to be authenticated, authorized, and audited, often within an organizational scope.
AI agents amplify this further. Agents act:
- On behalf of users
- Within the context of organizations
- Across internal and external systems
Cognito has no native concept of delegated or agent identity. Teams typically respond by building parallel mechanisms, effectively a second auth system that lives outside Cognito.
What a Modern B2B + AI Auth Layer Needs to Model
To understand where Cognito starts to strain, it helps to name the actual identity primitives B2B SaaS converges toward.
These are not edge cases. In fact, they are the steady-state architecture of mature B2B SaaS.
Where AWS Cognito Becomes a Bottleneck for B2B SaaS
Cognito does not fail at these requirements.
Instead, it pushes them into application code.
Each individual workaround is reasonable.
Together, they explain why teams feel auth friction without anything “breaking”.
Recommended Reading: Migrate SSO without customer reconfiguration
The Hidden Cost: Auth Becomes Product-Critical Code
In Cognito-based B2B systems, authorization decisions are typically enforced in application code rather than at the identity layer. Because tokens are user-centric and lack tenant context by default, services must resolve organization membership, roles, and policies on each request.
As products evolve, this authorization logic spreads across services and endpoints. Identity changes such as introducing new roles, modifying tenant boundaries, or adding delegated access require coordinated changes across multiple code paths. This increases the risk of regressions and makes identity changes disproportionately expensive compared to other product updates.
At scale, authentication remains stable, but authorization becomes tightly coupled to business logic. Identity shifts from being an infrastructural concern to a product-critical dependency that affects release velocity and system correctness.
Key constraint: When identity context is reconstructed in application code, auth changes scale with product complexity.
Org-first, Agent-native Auth as an Alternative Model
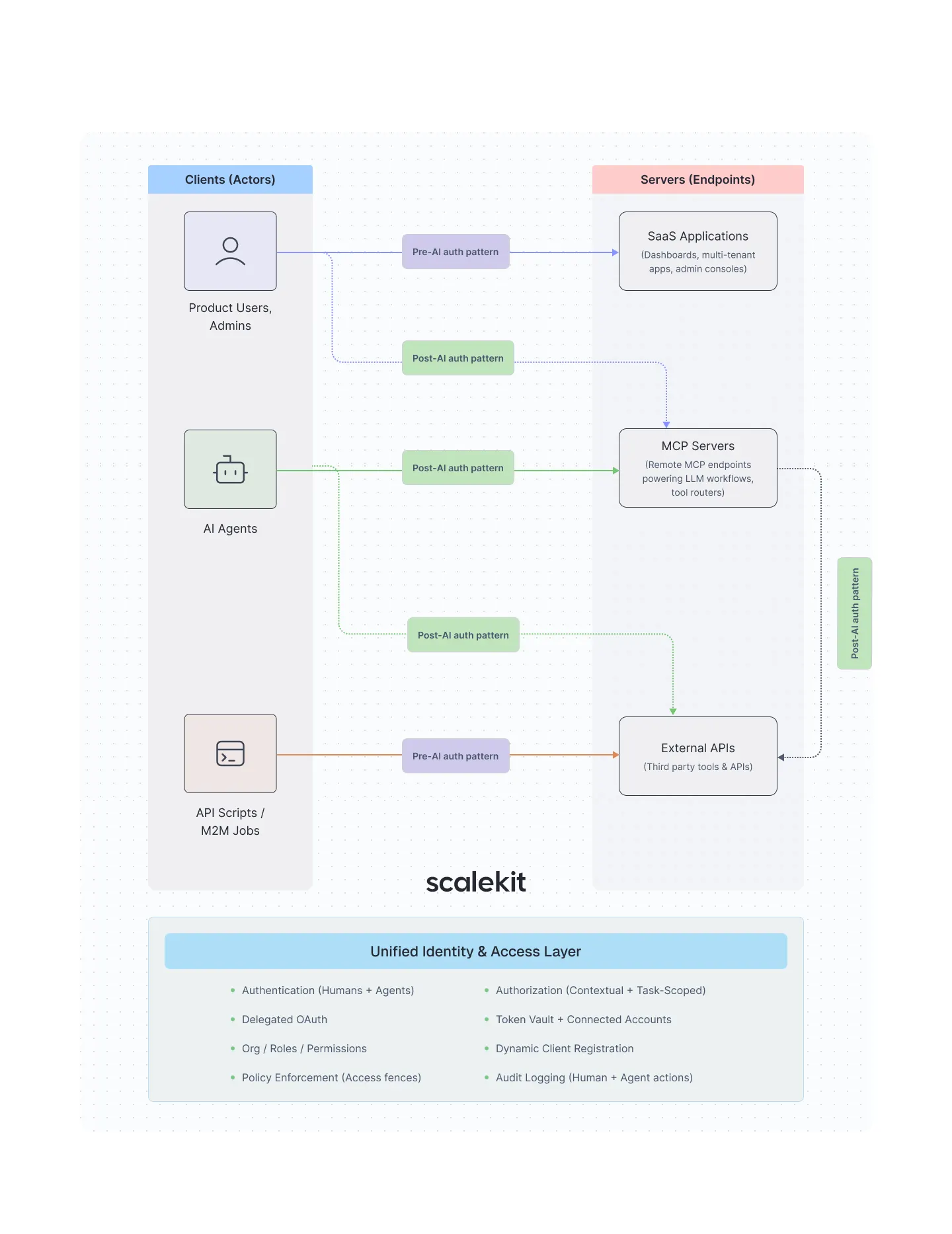
An org-first identity model starts from a different assumption: organizations are the root identity, not users.
In this model:
- Users, machines, and agents are actors within orgs
- Tokens carry tenant and role context by default
- Delegation and acting-on-behalf-of are explicit
- Auditability is tenant-aware by design
This collapses human auth, machine auth, and agent auth into a single, coherent system, instead of parallel layers.
Scalekit as an Auth Stack for B2B AI Applications
Scalekit is designed specifically for B2B SaaS products where identity spans humans, machines, and AI agents.
Key characteristics include:
- Organizations as first-class primitives
- Org-scoped users, roles, machines, and agents
- Org-aware JWTs and sessions
- Native support for Agent Auth and MCP Auth
- Identity designed for AI-native and agentic architectures
Teams typically adopt Scalekit not because Cognito is unreliable, but because the product has outgrown a user-first identity model.
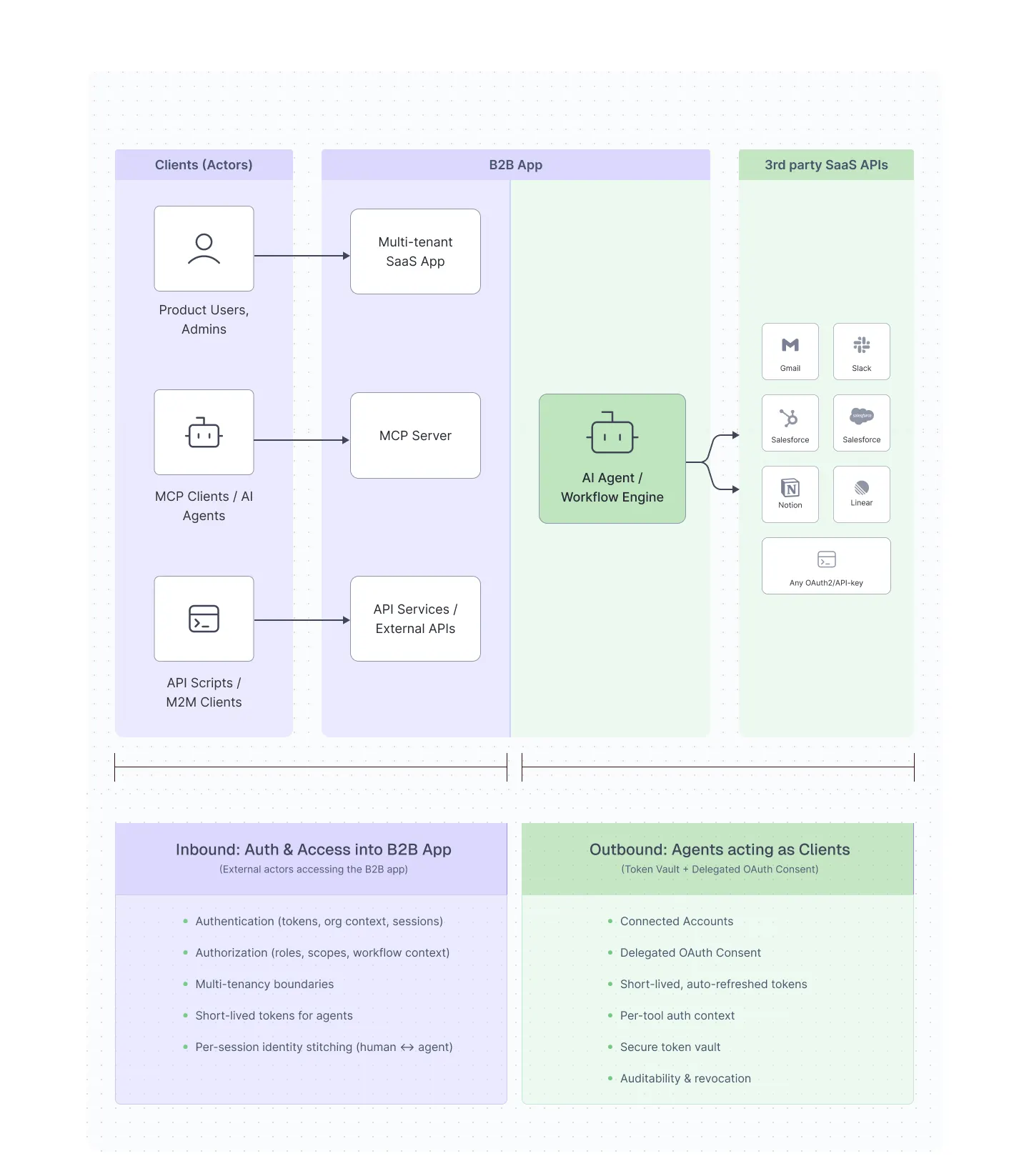
Using Scalekit modularly alongside Cognito
Teams adopting Scalekit do not typically replace Cognito for core user authentication immediately. Cognito often remains responsible for primary user login, while Scalekit is introduced for identity concerns that Cognito does not model natively, such as organization-scoped SSO, SCIM provisioning, or agent authentication.
In these deployments, Scalekit operates as an organizational identity layer that sits alongside existing authentication infrastructure. Enterprise identity configuration, tenant-aware tokens, and non-human actors are managed separately, while user authentication remains unchanged. This allows teams to decouple organizational identity and authorization from application code without a full migration.

Cognito Alternatives for B2B and AI-Native SaaS
As B2B SaaS products mature, teams often evaluate authentication platforms based on their ability to model organizational identity rather than protocol coverage alone. Key differentiators include native support for tenant-scoped roles, organization-aware sessions, delegated authorization, and non-human actors such as services and agents.
Platforms that treat organizations as first-class identity primitives reduce the amount of identity-related logic required in application code. Conversely, user-first systems require additional orchestration layers to support enterprise and AI-driven use cases. A comparative analysis of Cognito alternatives for B2B SaaS is covered in a separate article focused on platform-level trade-offs.
Recommended reading: Add enterprise SSO to AWS Cognito without writing the federation logic.
Final Take: Choosing an Auth Stack That Matches Your Product’s Trajectory
AWS Cognito provides reliable user authentication and integrates well with AWS infrastructure. For early-stage B2B SaaS products with limited tenant complexity, this model is often sufficient.
As products evolve toward organization-centric access control, machine-to-machine integrations, and agent-based workflows, the limitations of a user-first identity model become more pronounced. When authorization, tenant context, and delegation are implemented primarily in application code, identity becomes a scaling bottleneck.
Selecting an authentication platform that models organizational identity natively reduces long-term complexity and aligns the identity layer with how B2B SaaS systems operate in production.
FAQs
1. Can AWS Cognito support a multi-tenant B2B SaaS?
Yes, however, with a very limiting caveat, i.e., you’ve to do significant application-side modeling. This is because Cognito does not have a native concept of organizational or tenant-scoped roles. So, B2B teams using Cognito have to implement multi-tenancy by storing org relationships, roles, and policies in their own database and resolving them on every request. This works early, but shifts identity complexity into application code as the product scales. This becomes a painful overhead with the growth trajectory of your application. You don’t want to be wasting your developer hours on this.
2. What are the main disadvantages of AWS Cognito for B2B SaaS?
Cognito is fundamentally user-first, while Scale-stage B2B SaaS is organization-first.Key limitations of Cognito include the lack of native org objects, global (not tenant-scoped) groups, user-centric tokens, and pool-level SSO configuration. These gaps don’t cause failures, but they create long-term friction as authorization, tenant context, and identity logic spread across services. The issues become more pronounced when you enter AI and agentic ecosystem.
3. Is AWS Cognito scalable for enterprise and large customers?
Cognito scales reliably in terms of infrastructure and throughput. The scalability challenge is architectural, not operational. As enterprise requirements like per-tenant SSO, SCIM provisioning, delegated access, and auditability emerge, the amount of custom logic required outside Cognito grows.
4. Is AWS Cognito an SSO solution?
Cognito supports SAML and OIDC and can participate in SSO flows. However, SSO configuration is scoped to user pools or app clients, not organizations. This makes it difficult to support tenant-specific identity providers without custom routing, discovery, and admin tooling. In B2B SaaS, SSO is often seen as a product feature rather than a simple configuration because it directly influences overall customer experience.
5. Does AWS Cognito support machine identity and AI agents?
Not natively. Cognito is designed around human users. Machine-to-machine access, service accounts, and AI agents acting on behalf of users or organizations are typically handled through separate mechanisms such as IAM roles, API keys, or custom token services. This often results in parallel auth systems that are difficult to unify and audit; typical cognito limitations when using it for B2B SaaS apps.
6. What are common alternatives to AWS Cognito for B2B SaaS authentication?
B2B-focused teams often evaluate platforms that model organizations as first-class identity primitives, not just users. So, your ideal Cognito alternative should typically provide tenant-scoped roles, org-aware tokens, delegated authorization, SCIM provisioning, and native support for non-human actors. The key difference is reducing identity logic in application code rather than expanding protocol support alone. You may want to checkout Scalekit, as we tick all the aforementioned boxes.
7. Should you use AWS Cognito for a B2B SaaS product in 2026?
Cognito is a solid choice for early-stage or user-centric products where identity complexity is limited. For B2B SaaS products evolving toward enterprise customers, multi-tenant authorization, integrations, and agent-driven workflows, Cognito often becomes an identity foundation teams outgrow. At that point, you may want to explore something modular like Scalekit as the decision is less about replacing Cognito and more about introducing an org-first identity layer alongside it.




.png)