SAML SSO in B2B SaaS: The complete guide for developers and enterprise buyers

TL;DR
- SAML lets users sign in using their company’s identity provider (Okta, Entra ID, Ping, Google Workspace) instead of creating new passwords for your SaaS app.
- The IdP authenticates the user and sends your application a signed SAML response, which your app trusts to create a session.
- Enterprises prefer SAML because it centralizes MFA, access policies, and offboarding, all handled in one place.
- For B2B SaaS, SAML SSO is a must-have. Many mid-market and enterprise deals block immediately if SSO isn’t supported.
- Implementing SAML across multiple IdPs is complex (metadata formats, certificates, tenant mappings, assertion differences), and platforms like Scalekit remove this engineering overhead with unified SDKs and automated IdP integrations.
The role of SAML SSO in B2B SaaS architecture
Enterprise companies run dozens, often hundreds, of internal and external applications: CRMs, ERPs, HR systems, data tools, and SaaS platforms that their teams use every day. As usage scales, managing identity across this entire stack becomes unmanageable. To solve this, IT teams standardize on authentication via identity providers (IdPs) such as Okta, Microsoft Entra ID, Ping, or Google Workspace. These systems centralize login, MFA, password resets, and access policies in one place.
For SaaS vendors moving upmarket, this centralization directly shapes customer expectations. During early security reviews, enterprises assume your product will integrate with their existing IdP without requiring separate credentials or manual onboarding. This is where SAML becomes essential. It allows the customer’s IdP to authenticate the user and securely pass identity information to your application, enabling seamless sign-in without storing passwords.
For customers, this provides predictable governance and consistent MFA enforcement. For B2B SaaS teams, a lack of SAML support slows proofs of concept, complicates onboarding, and often becomes a blocker during enterprise procurement.
This guide builds the foundation you need to support enterprise SSO correctly. It explains how SAML differs from SSO, how IdPs and Service Providers (SPs) communicate, and how the complete flow works in practice. From core concepts to attributes, metadata, assertions, and ACS endpoints, you’ll have the background needed to follow the hands-on Okta example later and to design multi-tenant SSO integrations that scale.
SAML vs SSO: What SAML actually is
Many teams assume SAML is SSO, but they solve different problems.
SAML is a protocol. SSO is an experience.
- SAML defines how identity is securely exchanged between an IdP (e.g., Okta) and an SP (e.g., your SaaS app).
- SSO defines what the user experiences: sign in once → access everything without logging in again.
- SAML can power SSO, but SSO can also be implemented using OIDC, Kerberos, or other protocols.
Here’s the relationship in one table:
This understanding prevents common mistakes, like treating SAML as a login method rather than what it actually is, a federation protocol used by IdPs and SPs to establish trust and exchange identity assertions.
SAML vs OIDC: How they differ in modern B2B SaaS
As soon as teams understand that SAML is a protocol and SSO is an experience, the next question becomes: Which standard should a SaaS product support, SAML, OIDC, or both?
Although both enable Single Sign-On, they were built for different environments and technical requirements. Understanding these distinctions helps product and engineering teams make the right decision for their architecture and customer base.
When SAML Is typically used
SAML is the prevailing choice in enterprise workforce identity, especially when integrating with providers such as Okta, Ping Identity, and Microsoft Entra ID. It fits well when:
- Customers already rely on established SSO infrastructure.
- Governance and compliance requirements mandate centralized authentication.
- MFA, conditional access, and group-based policies are enforced at the IdP.
- Onboarding must fit existing enterprise identity workflows.
This is why most B2B SaaS products selling to mid-market and enterprise buyers are expected to support SAML out of the box.
When OIDC is typically used
OIDC (OpenID Connect) is more common in modern web and mobile applications, developer tools, and consumer-facing products. It is preferred when:
- Mobile-first authentication is required.
- Applications depend on the lightweight JSON Web Token (JWT) format.
- APIs and microservices need stateless access tokens.
- Developer-friendly, REST-based flows are important.
- Integrations with modern IdPs (Auth0, AWS Cognito, Google Identity) are needed.
OIDC is generally simpler to configure and integrates naturally with modern architectures.
High-Level comparison of SAML and OIDC
How to decide which standard to support
The decision for SaaS vendors often aligns with customer profile and technical architecture:
- Enterprise-facing SaaS → SAML is expected during onboarding.
- Developer-centric or mobile-first products → OIDC is more natural.
- SaaS platforms aiming to serve both segments → Support both SAML and OIDC.
Most mid-market and enterprise SaaS companies eventually implement both to avoid friction during customer integrations.
SAML SSO architecture: Identity Provider (IdP) and Service Provider (SP)
SAML operates on a simple but powerful architectural model built around two systems: the Identity Provider (IdP) and the Service Provider (SP). Every SAML authentication flow depends on the trust established between these two components through metadata, certificates, and signatures.
IdP and SP responsibilities at a glance
How trust is established between IdP and SP
In web-based SSO flows, the IdP authenticates the user and issues a signed SAML Assertion. The SP validates this assertion using the IdP’s certificate, processes user attributes, and establishes an authenticated session.
This trust relationship is established through metadata exchange, where each side publishes its configuration:
What IdP Metadata typically contains
- Identity Provider EntityID
- SSO (Single Sign-On) endpoints
- SLO (Single Logout) endpoints
- Certificates for verifying signatures
- Supported bindings (Redirect, POST)
What SP Metadata typically contains
- Service Provider EntityID
- ACS (Assertion Consumer Service) URL
- Signing/encryption certificates
- Supported NameID formats
Both systems rely on this metadata to securely route requests, validate signatures, and ensure messages originate from trusted sources.
Why this model works for enterprise SaaS
Enterprise organizations standardize authentication across multiple applications. When your SaaS product integrates with a customer’s IdP:
- Authentication moves out of your application and into their security perimeter.
- The customer enforces MFA, conditional access, and password policies in one place.
- Your application receives a signed assertion without storing user credentials.
- Onboarding and offboarding become easier through centralized identity governance.
This pattern aligns directly with enterprise expectations, reduces support burden, and enables a scalable, secure authentication model for multi-tenant SaaS platforms.
How SAML Fits Into B2B SaaS Multi-Tenancy and User Access Models
B2B SaaS applications almost always operate in a multi-tenant environment, where each platform serves multiple customer organizations with their own users, roles, and policies. SAML fits naturally into this model because every tenant can connect its own Identity Provider (IdP), such as Okta or Entra ID.
Mapping SAML logins to tenants
When a user signs in through SAML, the Service Provider (SP) determines:
- Which tenant the user belongs to
- What role or access level should they receive
- What resources can they access
SaaS apps typically map SAML attributes such as:
- Email domain (e.g., @acme.com)
- Tenant identifier passed by the IdP
- Groups/Roles defined in the enterprise directory
This lets enterprises manage identities and roles centrally while the SaaS product keeps authorization lightweight and consistent.
Advanced Multi-Tenant patterns
More mature B2B setups extend this further by supporting:
- Multiple IdPs per tenant (common for subsidiaries or regional divisions)
- Per-tenant metadata and certificate management
- Dynamic attribute mappings for roles and groups
- Just-in-Time (JIT) provisioning for auto-creating users at first login
- SCIM for automated lifecycle management (provisioning, deactivation, role updates)
These patterns allow SaaS teams to deliver seamless onboarding, strong governance alignment, and scalable multi-tenant authentication, without managing separate passwords for every user.
The core components that power SAML SSO
SAML (Security Assertion Markup Language), finalized in 2005 by OASIS, is an XML-based standard that allows an Identity Provider (IdP) to authenticate a user and securely pass identity information to a Service Provider (SP). It enables Single Sign-On without shared passwords and lets enterprises centralize authentication while SaaS applications focus on authorization and session management.
At a high level, SAML relies on a trust relationship between the IdP and the SP. The IdP authenticates the user and issues a signed SAML assertion; the SP validates this assertion using metadata (certificates, endpoints, identifiers) exchanged between the two parties. This metadata-driven trust ensures secure, interoperable communication across different providers and applications.
Before implementing SAML, let’s review its components and concepts:
- Authentication and Authorization
- Identity Provider and Service Provider
- SAML Request and SAML Response
- SAML Metadata
- SAML Assertions
- SAML Attributes
- SAML Bindings
- SAML Protocols
- SAML Profiles
- Relay State
- XML Signature
Authentication and authorization
Authentication defines how a user is identified and validated using credentials, typically a username and password, during the sign-in process. Authorization, in contrast, defines which resources users have access to. The SAML protocol facilitates this data exchange between an Identity Provider (IdP) and a Service Provider (SP).
Identity Provider (IdP) and Service Provider (SP)
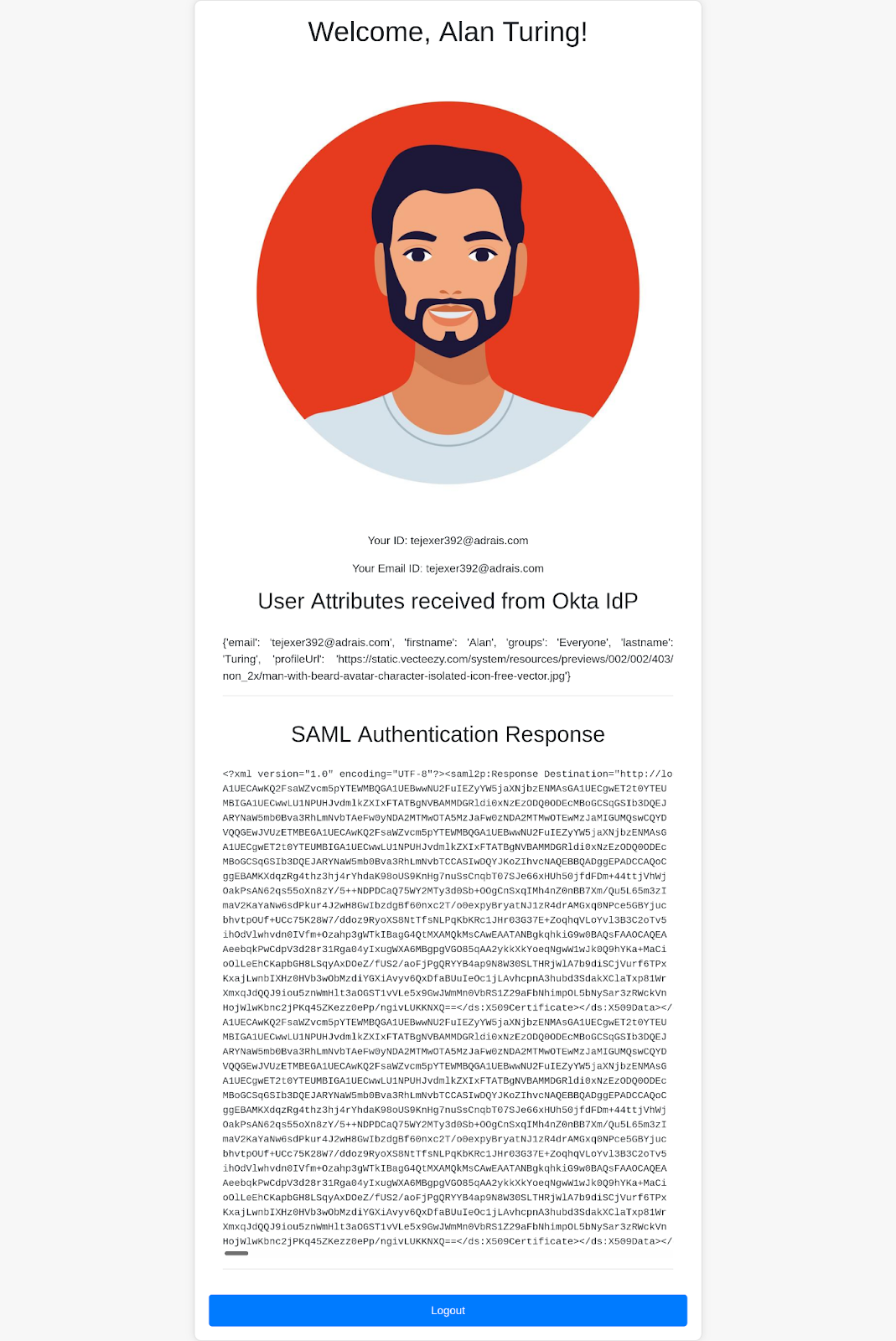
This section uses the same IdP and SP roles described above but shifts focus to their responsibilities within the SAML flow. The SP is the application the user wants to access, while the IdP manages user identities and attributes such as firstName, nickname, profileURL, and more.
A typical SAML authentication workflow involves the following steps:
- The end user (browser) requests the SP to access a protected resource
- The SP initiates the login by sending a SAML request to the IdP
- The IdP authenticates the user, generates the SAML assertion, and sends it back to the SP
- The SP validates the SAML assertion and ascertains the user's identity
- Based on the identity, the SP grants the user access to the resource.
- To plan redirects and user journeys, take a look at IDP-initiated vs. SP-initiated SSO.
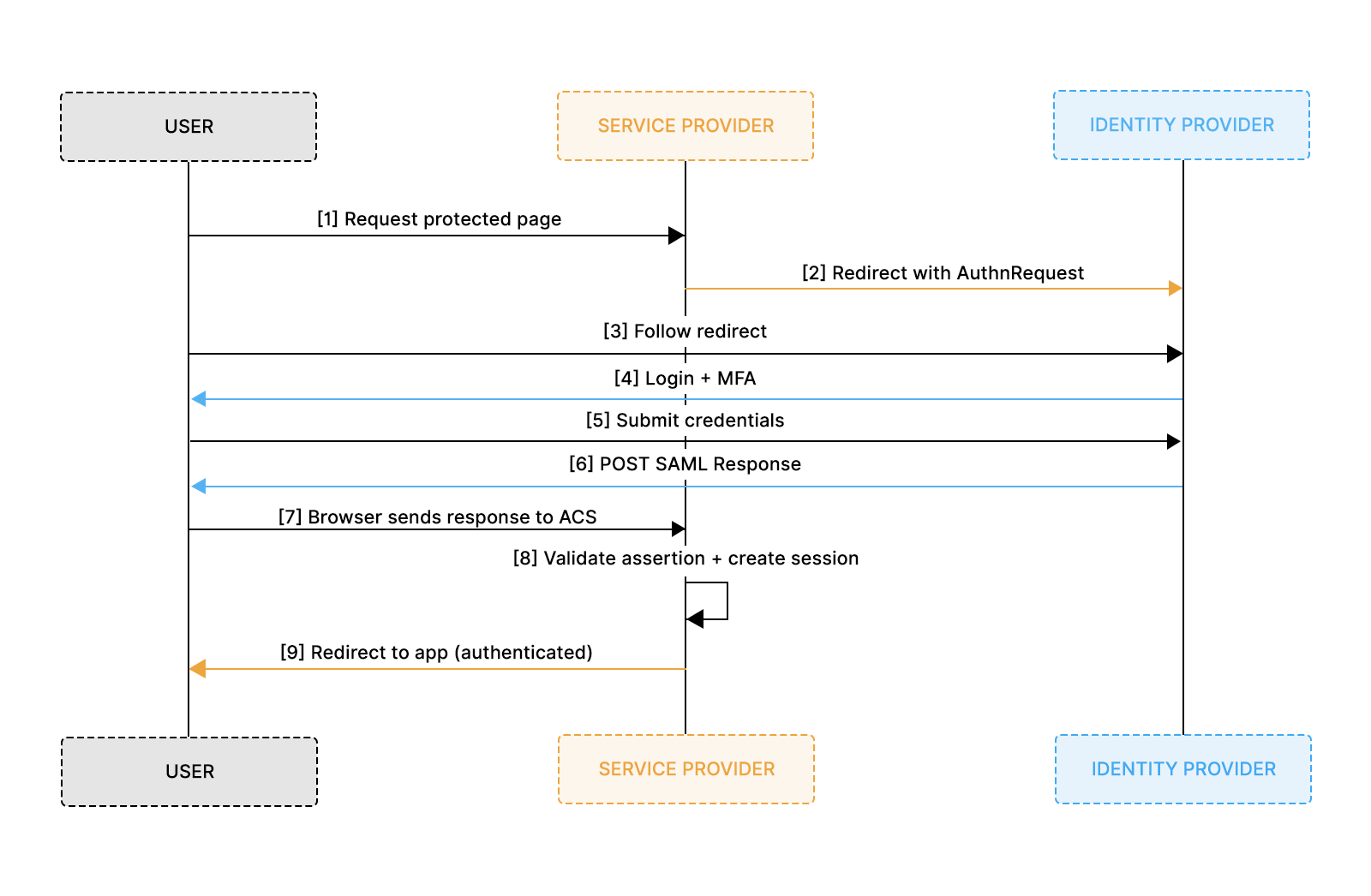
SP accomplishes this using the following three components:
- IdP Certificate: The certificate is stored in the SP application and used to verify the SAML Response signature.
- Assertion Consumer Service (ACS) URL: The endpoint provided by the SP to which SAML responses are sent and processed. The SP shares this URL with the IdP.
- IdP Sign-in URL: The endpoint on the IdP side where SAML requests are submitted. The SP obtains this information from the IdP metadata.
These elements ensure that the SP can securely receive and process SAML assertions, enabling seamless user authentication.
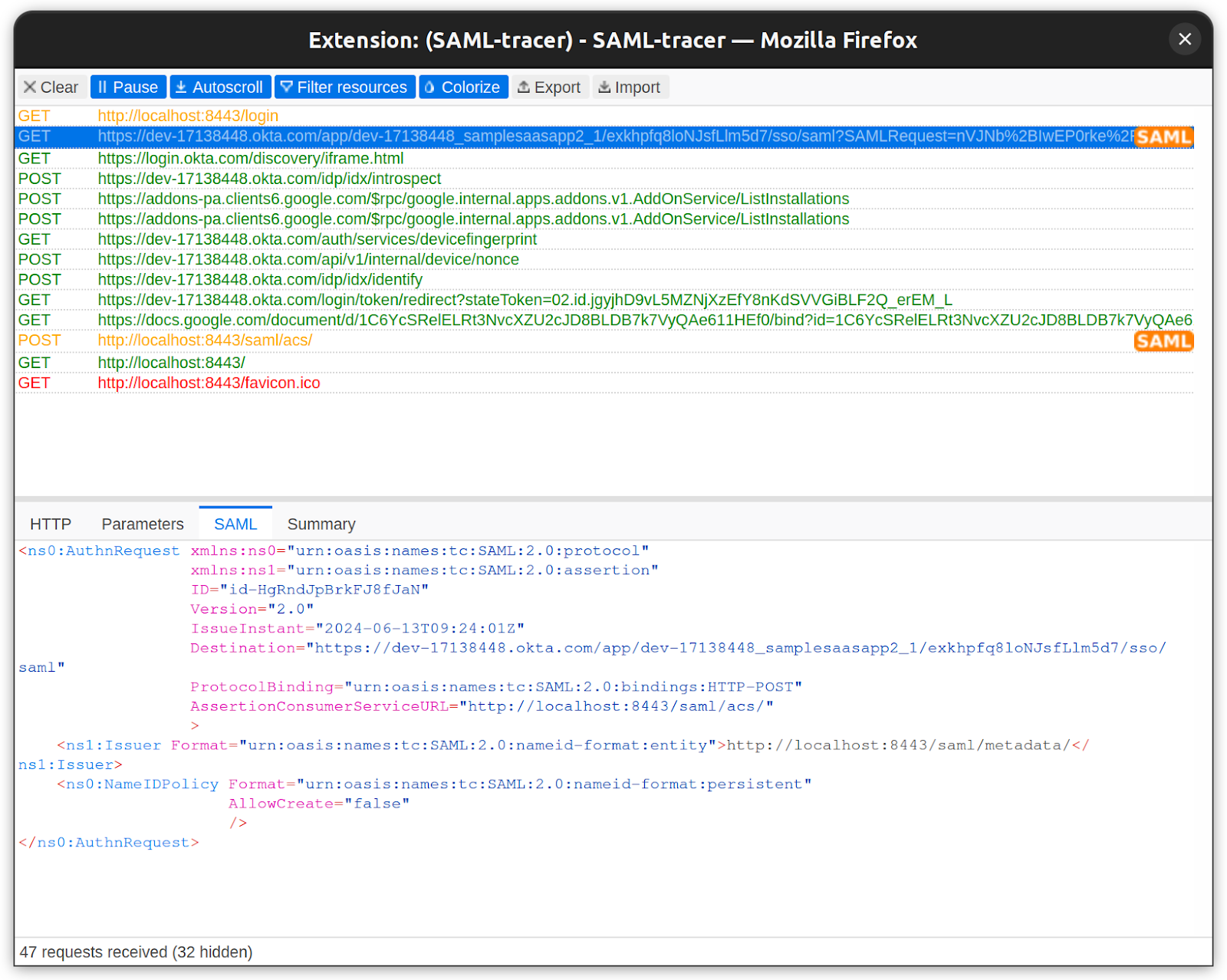
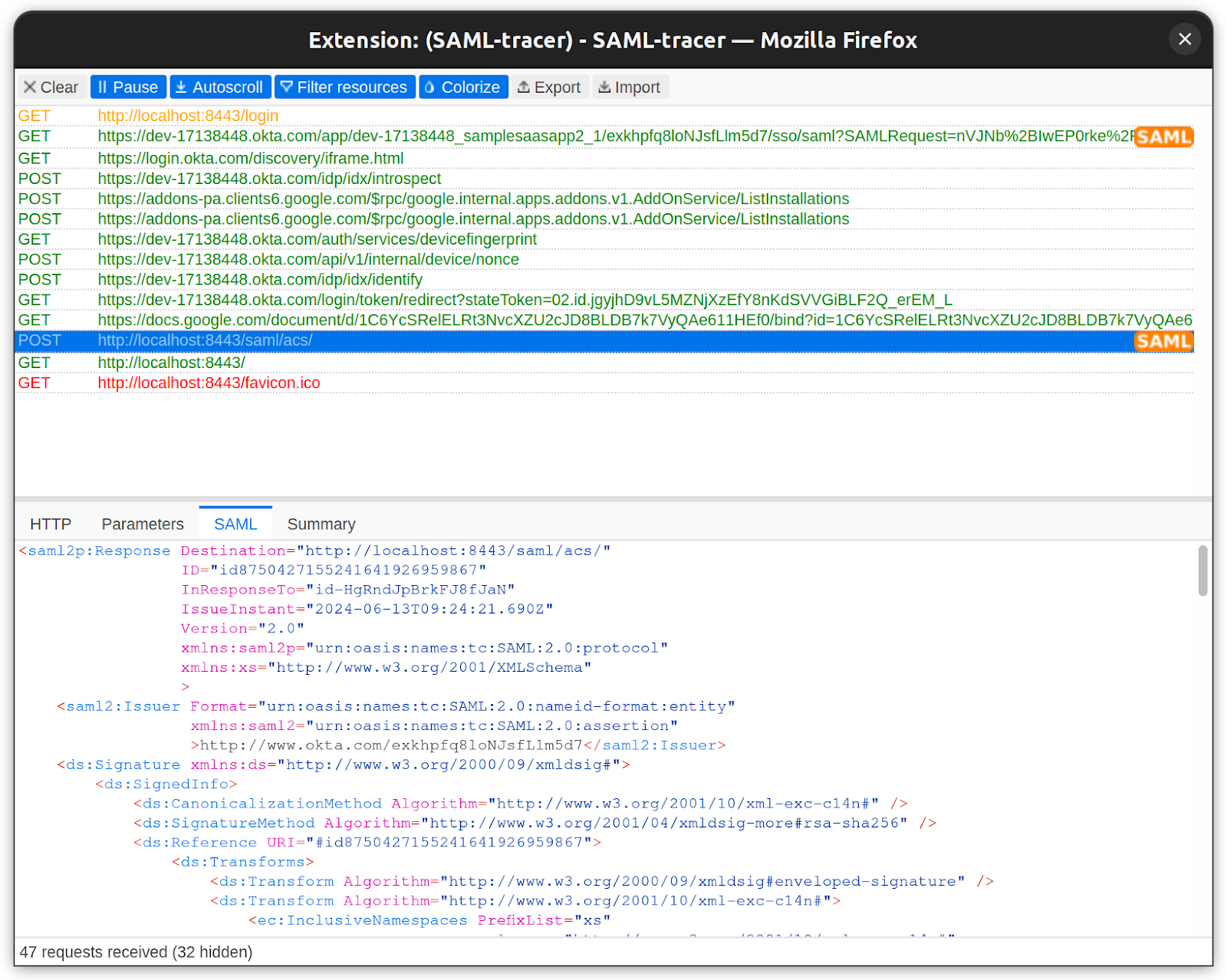
SAML request and response
A SAML Request is generated by the SP to ask the IdP to authenticate the user.
A SAML Response is generated by the IdP and contains the signed SAML Assertion.
Example of a SAML Request
To view the complete request, refer to the sample_request.xml file.
Example of SAML Response from IdP for authentication with additional attributes.
To view the complete request, refer to the sample_response.xml file.
SAML assertions
SAML Assertions are XML documents issued by the IdP that contain statements about a user. The SP uses these assertions to grant or deny access to resources. Assertions consist of:
- Authentication Statements: Confirm that the user has been authenticated.
- Attribute Statements: Provide additional information about the user (e.g., email, roles).
- Authorization Decision Statements: Indicate the user's access rights.
Assertions serve as the core of SAML authentication, enabling the secure transfer of user identity and attributes between IdP and SP, facilitating Single Sign-On.
SAML attributes
SAML Attributes carry additional user information within assertions. Common attributes include
- NameID: A unique identifier for the user.
- Email: The user's email address.
- Roles: User roles or group memberships.
Attributes enable SPs to enforce fine-grained access control and customize user experiences based on identity information.
XML signature (DSig)
XML Signature ensures the integrity and authenticity of SAML messages. It uses digital signatures to verify that the message has not been altered and comes from a trusted source.
SAML metadata
SAML Metadata provides configuration details about the IdP and SP. The IdP metadata includes entity ID, Single Sign On (SSO), and Single Logout (SLO) endpoints. For the SP, it includes details like the Assertion Consumer Service (ACS) endpoints, entity ID, and certificates. It facilitates interoperability by allowing entities to share and understand each other's configuration.
Example SAML Metadata of IdP.
To view the complete request, refer to the sample_idp-metada.xml file.
SAML bindings
Bindings specify how SAML messages are transported between IdP and SP. Common bindings include
- HTTP Redirect: Transports SAML messages via URL query parameters. Used for sending authentication requests.
- HTTP POST: Encodes SAML messages within an HTML form and uses the POST method. It is commonly used to send SAML responses.
In the above example, IdP SAML Metadata, HTTP POST, and Redirect bindings are defined for specific URLs for SingleSignOnService and SingleLogoutService.
SAML profiles
Profiles define specific use cases for SAML, detailing how assertions, protocols, and bindings should be used together. Common profiles include:
- Web Browser SSO Profile: Facilitates SSO for web applications.
- Single Logout Profile: Allows users to log out from all connected services simultaneously.
Relay state
Relay State is an optional parameter that maintains state information between the IdP and SP during authentication. It typically contains a URL or a reference that the SP will redirect to after authentication. This helps users return to the exact page they came from or continue a flow seamlessly after SSO.
Most enterprise IdPs also impose strict size limits on RelayState values (commonly 80–1024 bytes), so it should always be an opaque, short identifier rather than a long encoded URL or user-specific payload. RelayState must also never contain sensitive data, since it is passed through the browser and can be tampered with. Instead, the SP should store any needed information server-side and reference it via a short token in RelayState.
Building a SAML SSO flow with Okta
SAML 2.0, standardized by OASIS in 2005, remains one of the most widely used authentication protocols in enterprise environments. Many organizations run identity systems like Okta, Microsoft Entra ID, OneLogin, or PingFederate, making SAML SSO support essential for B2B SaaS applications.
In this section, we walk through integrating Okta as an Identity Provider (IdP) and building a working SAML SSO flow using a simple sample application. The hands-on example mirrors what typically happens during enterprise onboarding: the customer configures your application inside their IdP, and your application consumes the SAML assertion to authenticate users.
Use case
We’ll build a simple web application with two pages: login and profile. The login page will feature a "Login with SAML SSO" button. The profile page will display user details such as email, name, and photo, as well as the SAML Response Attributes and the SAML Response itself.
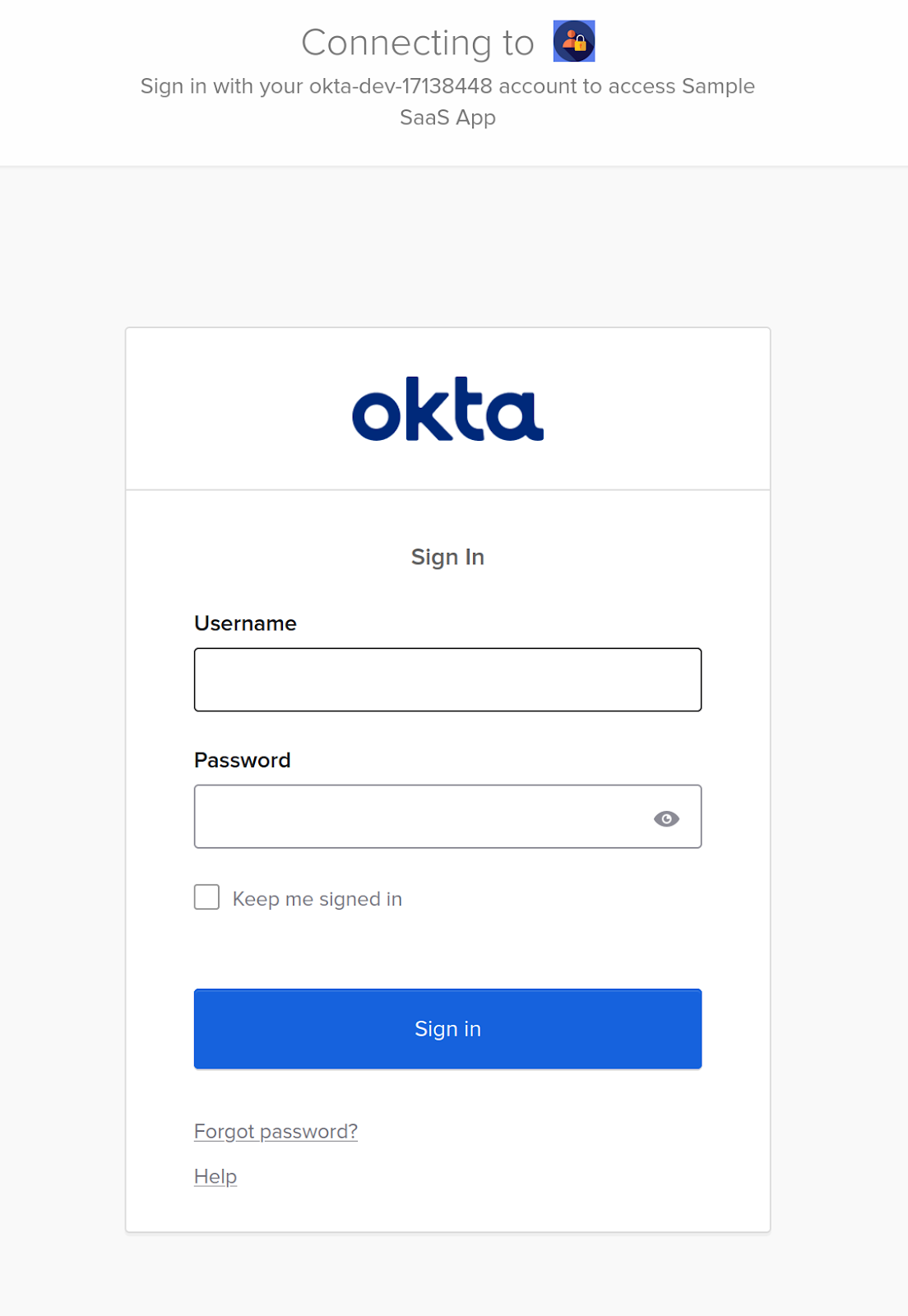
We will use Okta's SAML 2.0 Integration to configure our application for Single Sign-On. In this setup, our application will require a login, and Okta will serve as the IdP, providing authentication details via SAML SSO and our application acts as the Service Provider (SP).
Pre-requisites
Building a SAML SSO Flow using Okta requires the following prerequisites:
- A web application with a login page – We’ve built one using Python and Flask; you can use the same tools to build one. You can find our application in this GitHub repository.
- Okta developer account: Sign up for an Okta developer account if you don’t have one.
Two configurations are needed to build this flow:
- Configure Okta as IdP by creating a new application with SAML 2.0 SSO
- Configure the application with SAML support.
The following sections will describe them.
SAML flow - Configuring Okta as IdP
To integrate SSO with Okta, we must first create a new application from the Okta Dashboard.
This setup establishes the trust relationship between your application (SP) and Okta (IdP), which is required before SAML requests and responses can be exchanged.
1. Log in to your Okta Developer account, go to Applications from the Okta sidebar, click Create New App, select SAML 2.0, and click Next.
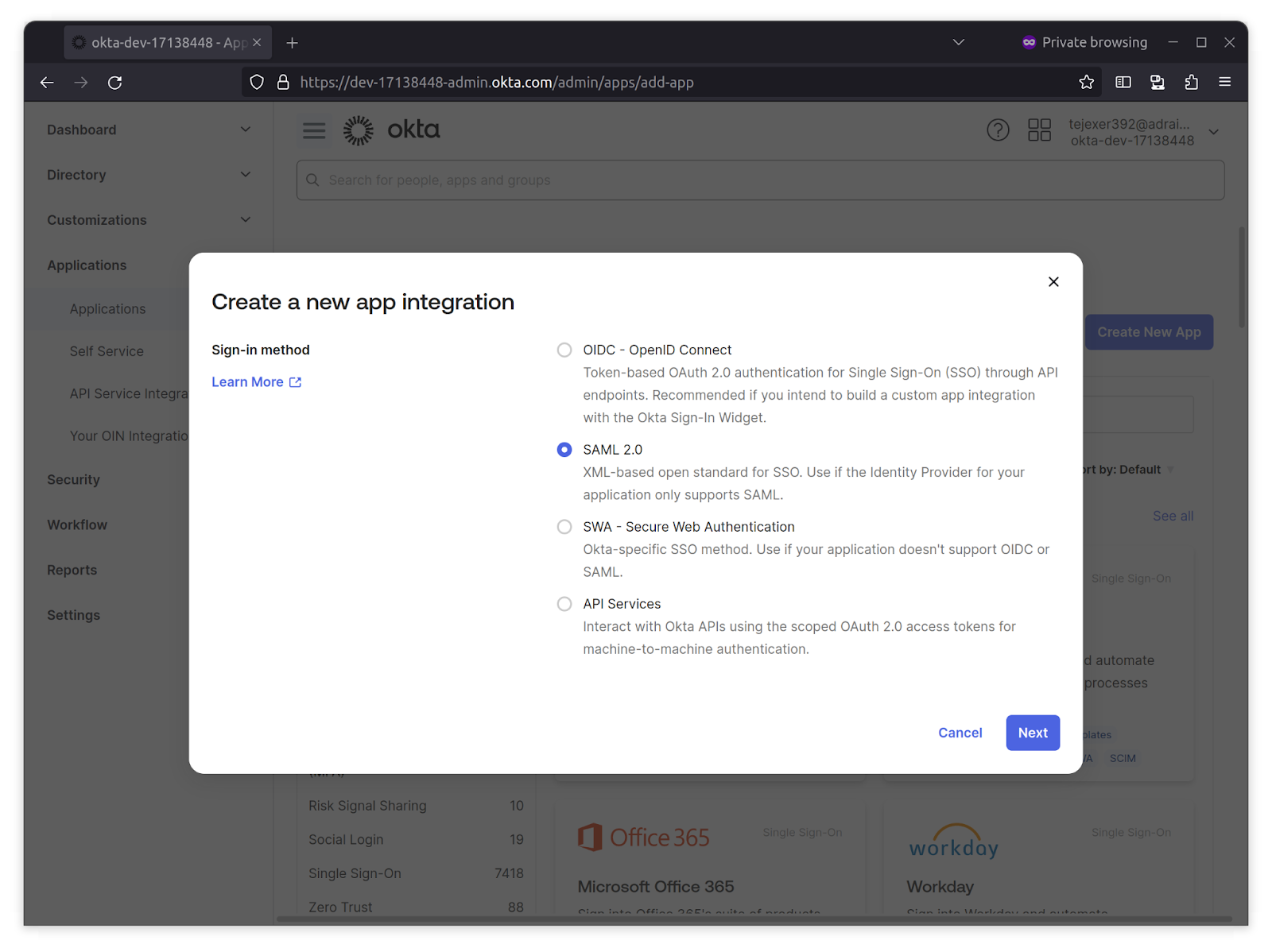
2. On the next screen, provide a name for the application.In this case, we’re adding a Sample SaaS App. You can add a logo to customize the login logo. This step creates the IdP-side representation of your SaaS product.
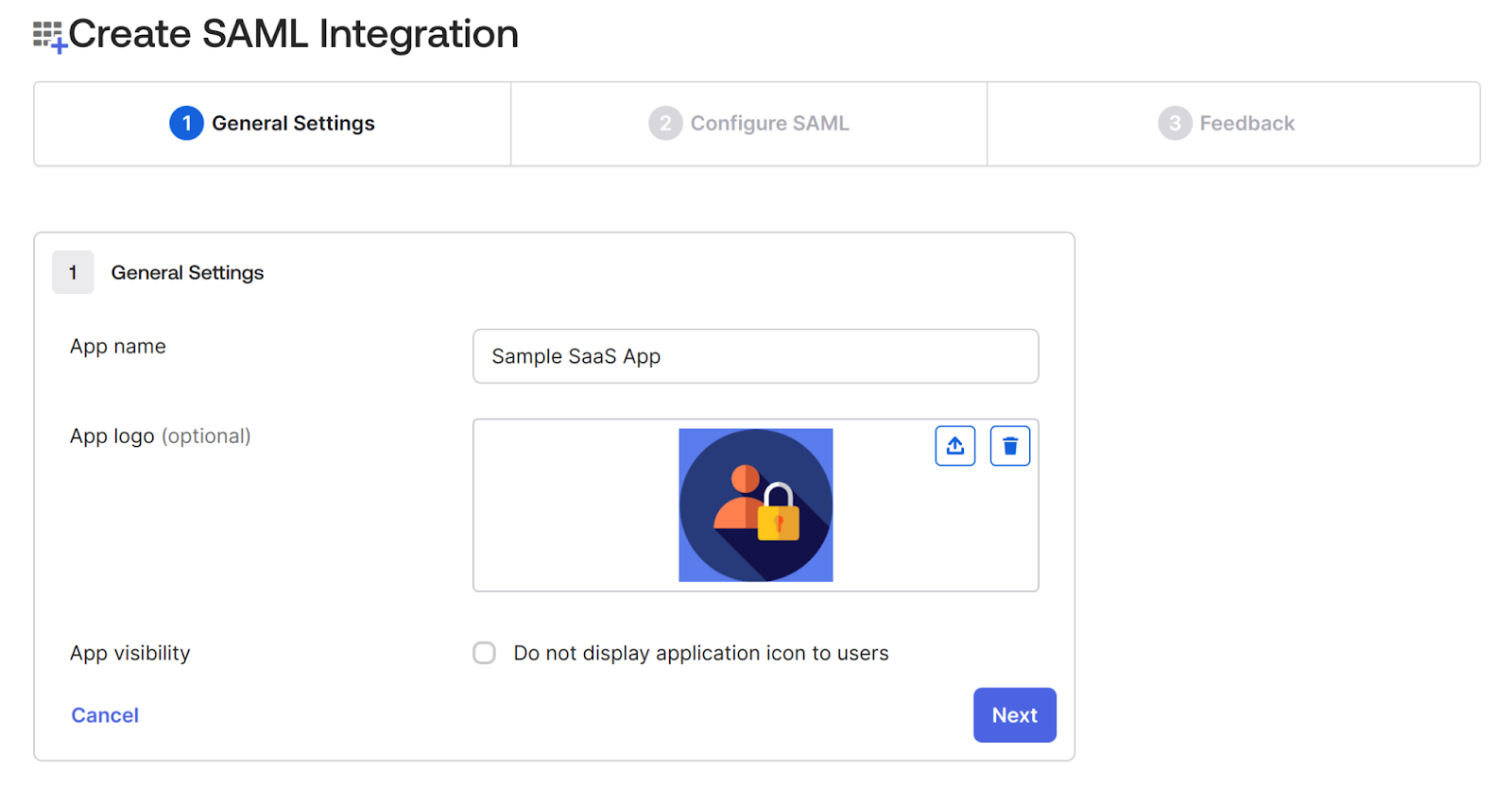
3. In the Configure SAML tab, configure the following:
- Single Sign-On URL (ACS URL):
Enter the Assertion Consumer Service (ACS) URL of your application.
This is the endpoint where the IdP will send the SAML Response (Assertion) using HTTP POST after authentication.
In our sample app, the ACS URL is: /saml/acs/
- NameID Format:
Set this to Persistent, which defines how the IdP identifies the user in the SAML assertion.
These two fields are the core of the trust configuration. The IdP must know where to send the response and in what format user identifiers should be passed.
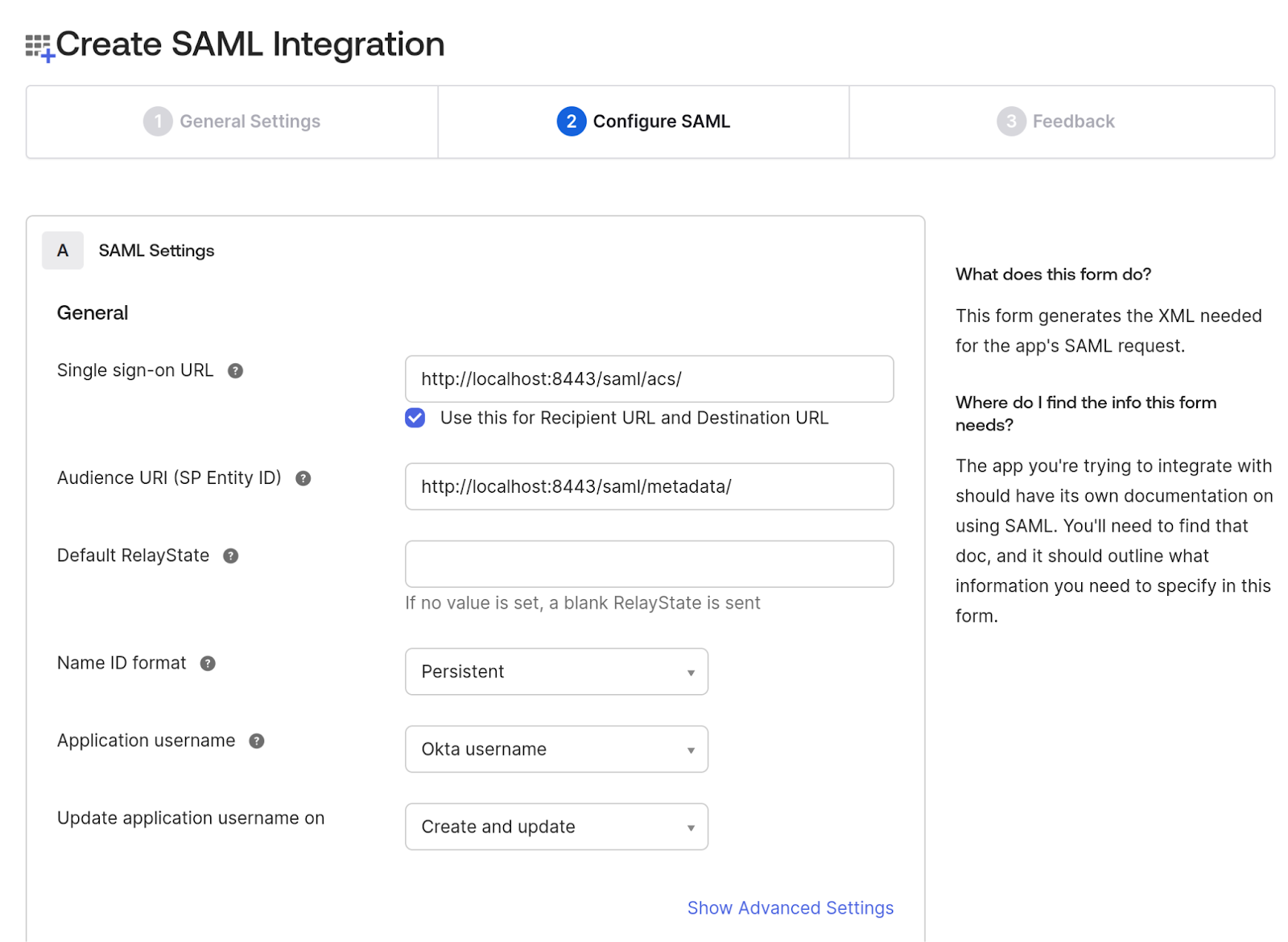
4. On the same page, navigate to the Attributes Statements section to configure the following attributes and group attribute statements to be sent when the authentication is successful. These attributes will later map to user profiles and permissions on the SP side.
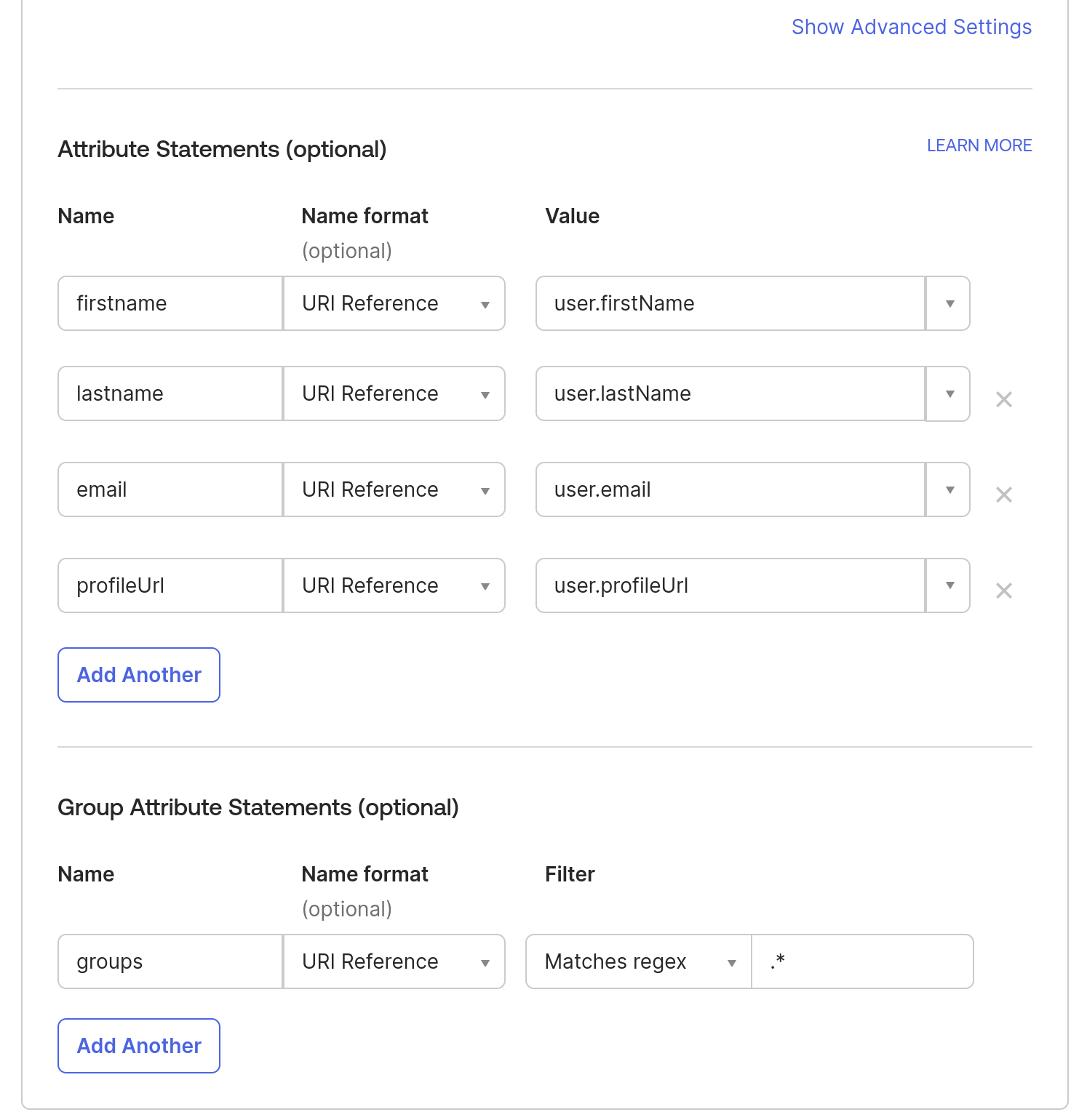
Note: To add more attributes to a User profile, you can go to Directory in the Okta sidebar- > click on Profile Editor -> All User -> Click on Okta User -> Click on Add Attributes.
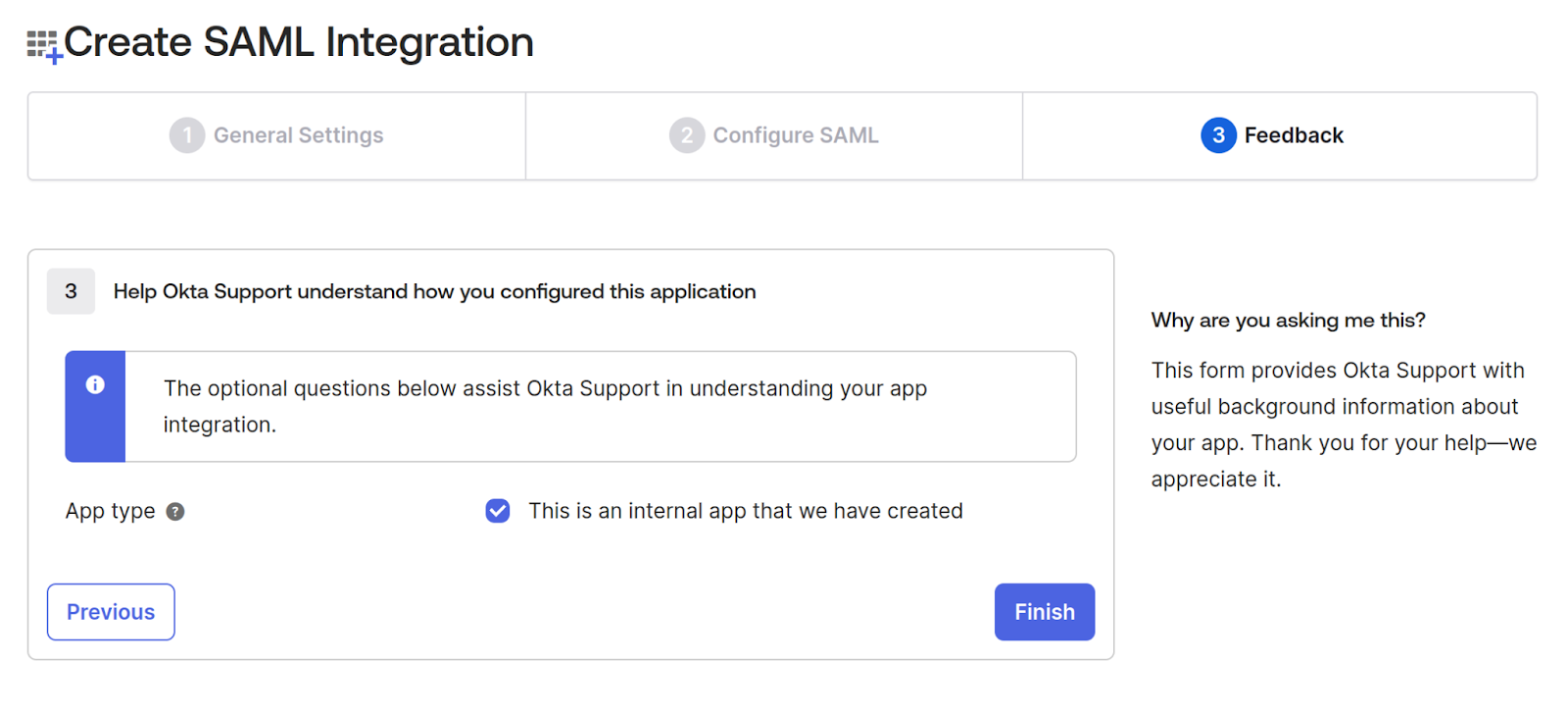
5. In the Feedback tab, check the App type checkbox “This is an internal app that we have created” since we’re testing it and not releasing it publicly. Click Finish.
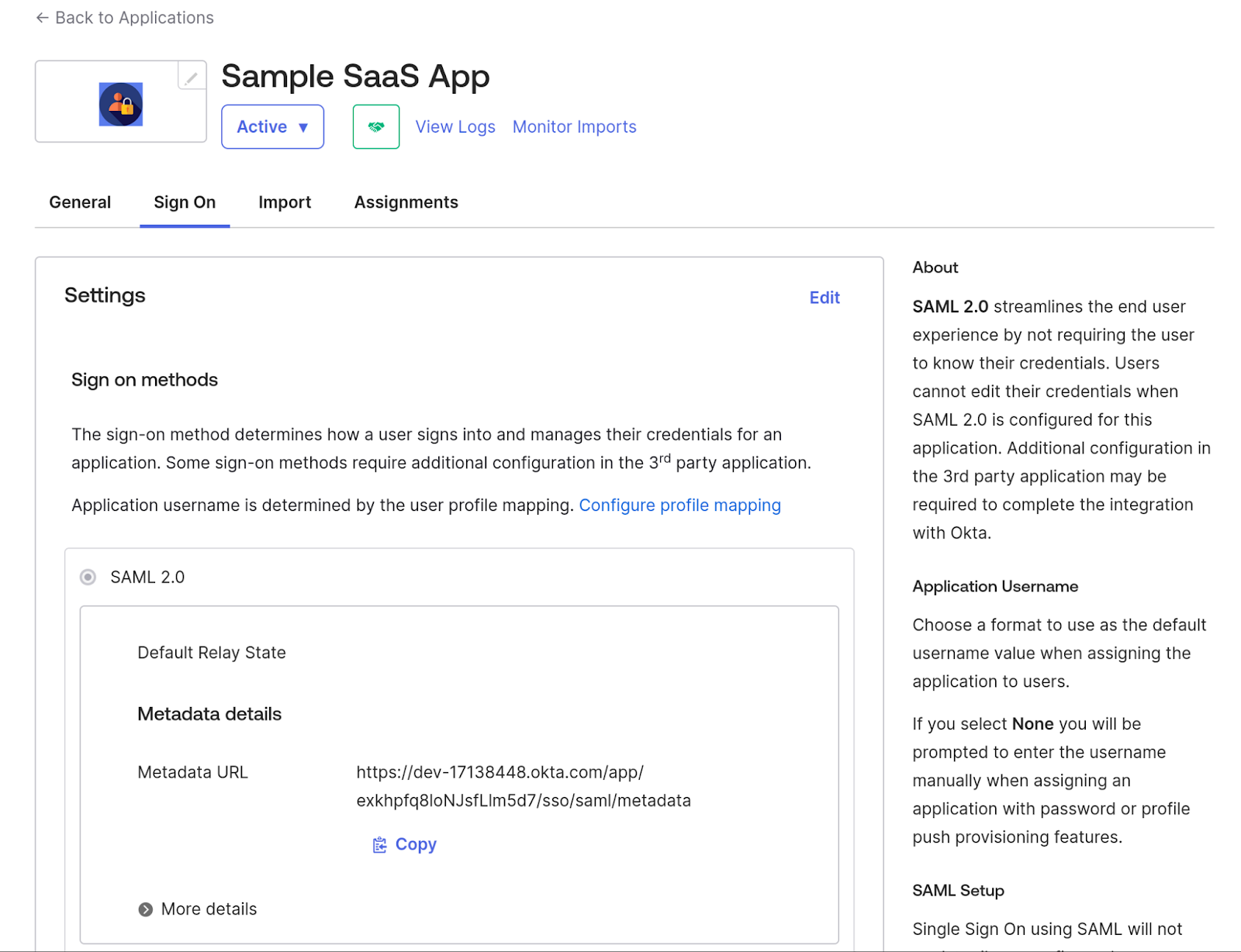
After finishing the application creation, it should show you the Metadata URL, which will have all the details of IdP metadata that we will use in the next step, so download the content from
that link and save that XML as idp-metadata.xml.
This metadata file is essential because it contains certificates and endpoints that your SP uses to validate signatures and route SAML traffic.
Once the application is created, assign users or groups who will use it. In this case, we'll use the same user who created the Okta account.
6. Go to Sample SaaS App -> Assignment -> Assign -> Assign to People -> Select your user -> click on the Assign button next to your user -> Save and go Back. -> Done.
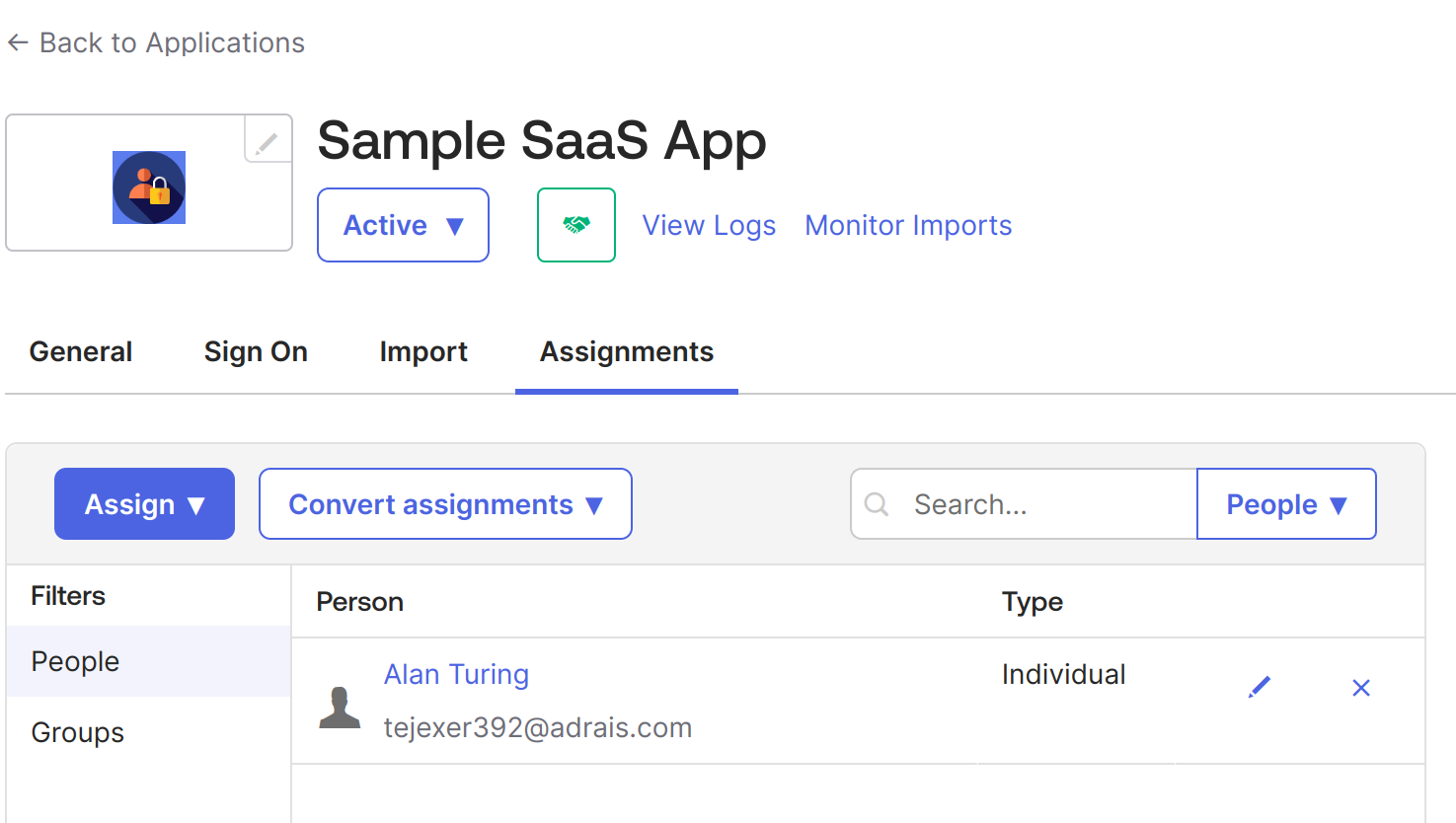
7. Now, do the same for groups. Go to Sample SaaS App -> Assignment -> Assign -> Assign to Groups > click on the Assign button next to your Groups -> Done.
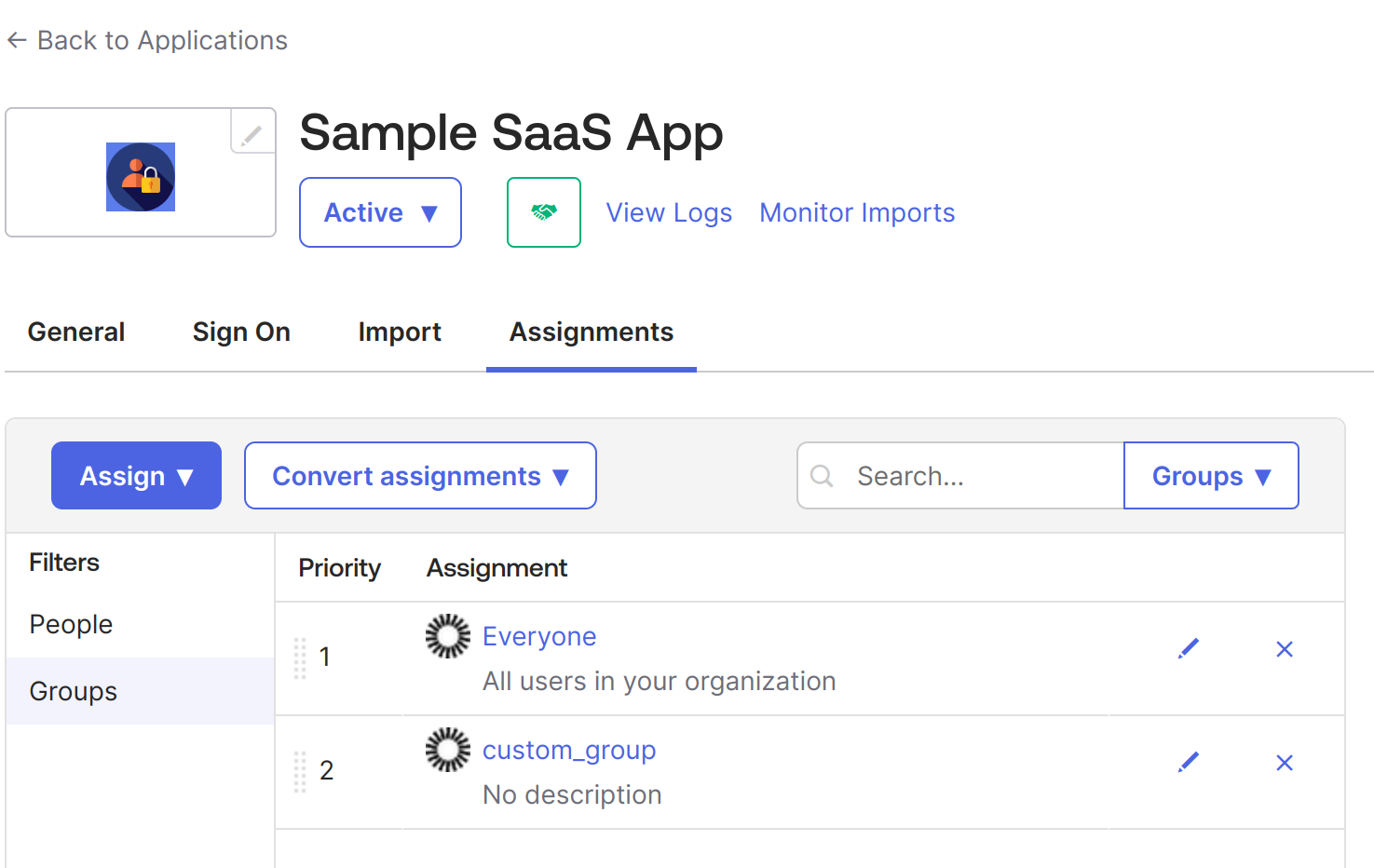
At this point, we have created an application in Okta for SSO configuration using SAML 2.0. It is an internal application, but we can make it public later as required. When public, it can be made available like all other applications in Okta integrations, such as Google Workspace and Salesforce.
This completes the IdP-side setup. The next step is configuring your application (the SP) to accept and validate SAML responses from Okta.
Configuring the sample application with SAML SSO
As mentioned, we have built a simple web application using Python and Flask. The app uses the PySAML2 library, which provides the core SAML 2.0 functionality required for acting as a Service Provider (SP). This section demonstrates how your SP consumes the metadata configured in Okta and completes the authentication flow.
Below is the repository structure
Move the idp-metadata.xml file we downloaded from Okta into the conf directory. After moving the file, the folder should look like this. SP can now automatically fetch IdP metadata from a remote URL and gracefully fall back. This is required for production setups where enterprises rotate certificates or publish dynamic metadata.
Now, we configure the sp_conf.py file, which contains all SAML settings for the SP application. This is where the SP declares its ACS endpoint, metadata URL, certificates, and expected bindings.
Security Note on ‘allow_unsolicited’ = True
Since the sample sets allow_unsolicited = True, the SP accepts IdP-initiated SSO flows (responses without a prior AuthnRequest). This is common in enterprise setups but requires careful handling:
- Enforce strict Audience and Recipient checks.
- Validate RelayState to ensure it hasn’t been tampered with.
- Make sure the ACS endpoint is always served over TLS 1.2+ in production.
- Do not expose the ACS endpoint over plain HTTP outside local development.
If your application does not need IdP-initiated SSO, set: 'allow_unsolicited': False
This restricts the SP to only SP-initiated authentication flows.
In this configuration:
- metadata supports both local and remote IdP metadata.
If a remote metadata URL is provided (IDP_METADATA_URL or METADATA_URL), the application can automatically fetch and cache it. Otherwise, it falls back to the local idp-metadata.xml file inside the conf folder. This makes the setup resilient to IdP certificate rotations and reduces the need for manual file updates. - assertion_consumer_service is the endpoint where the IdP posts the SAML Response (/saml/metadata/).
- entityid defines your SP metadata URL (/saml/metadata).
Note: If you change your port, domain, or metadata file location, update both your SP configuration and your Okta application settings accordingly.
The automated metadata handling ensures your application remains stable even when IdPs rotate certificates, issue new metadata, or require dynamic updates.
Automated metadata handling
In addition to supporting local metadata files, the sample application includes optional automatic metadata retrieval. If an environment variable such as IDP_METADATA_URL is provided, the app will fetch and cache the IdP’s metadata at startup. This makes the integration more resilient to IdP certificate rotations and configuration changes, removing the need to manually download or replace idp-metadata.xml. If a local file exists, it is used by default unless FORCE_REMOTE is set.








.png)




