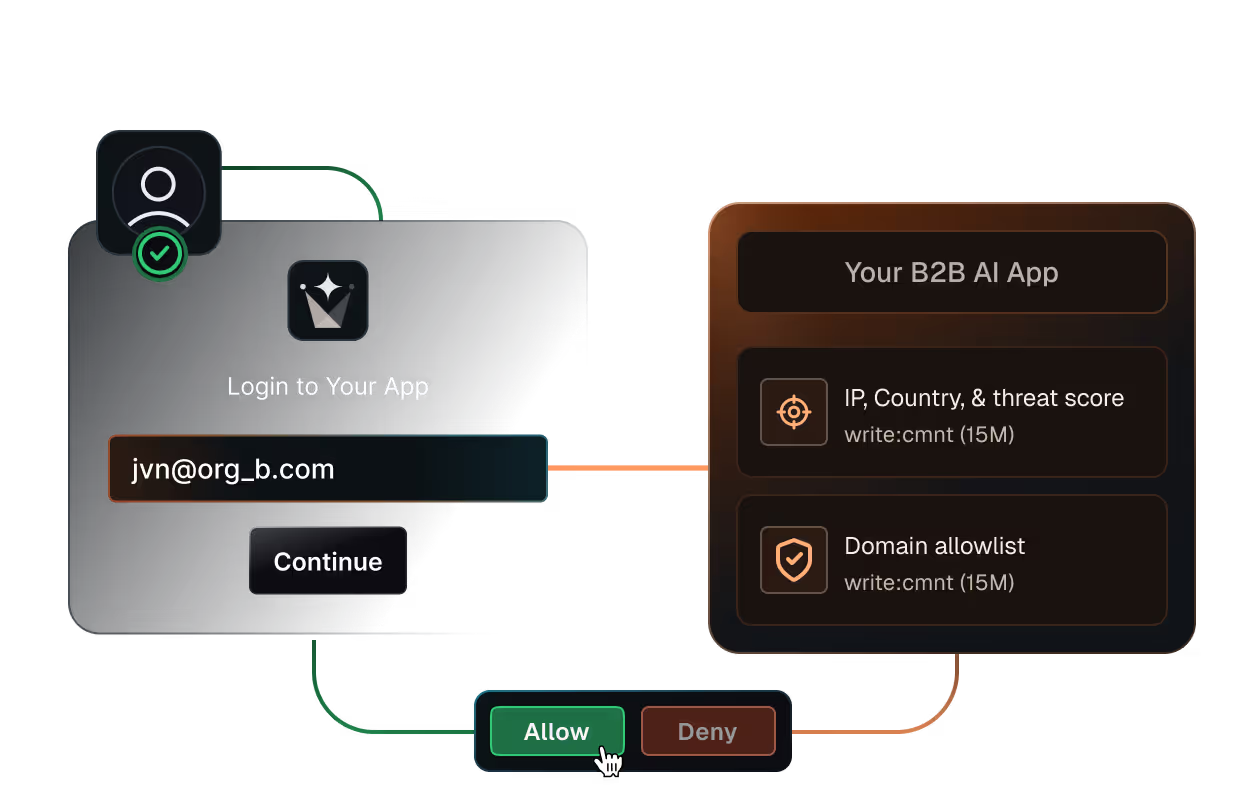
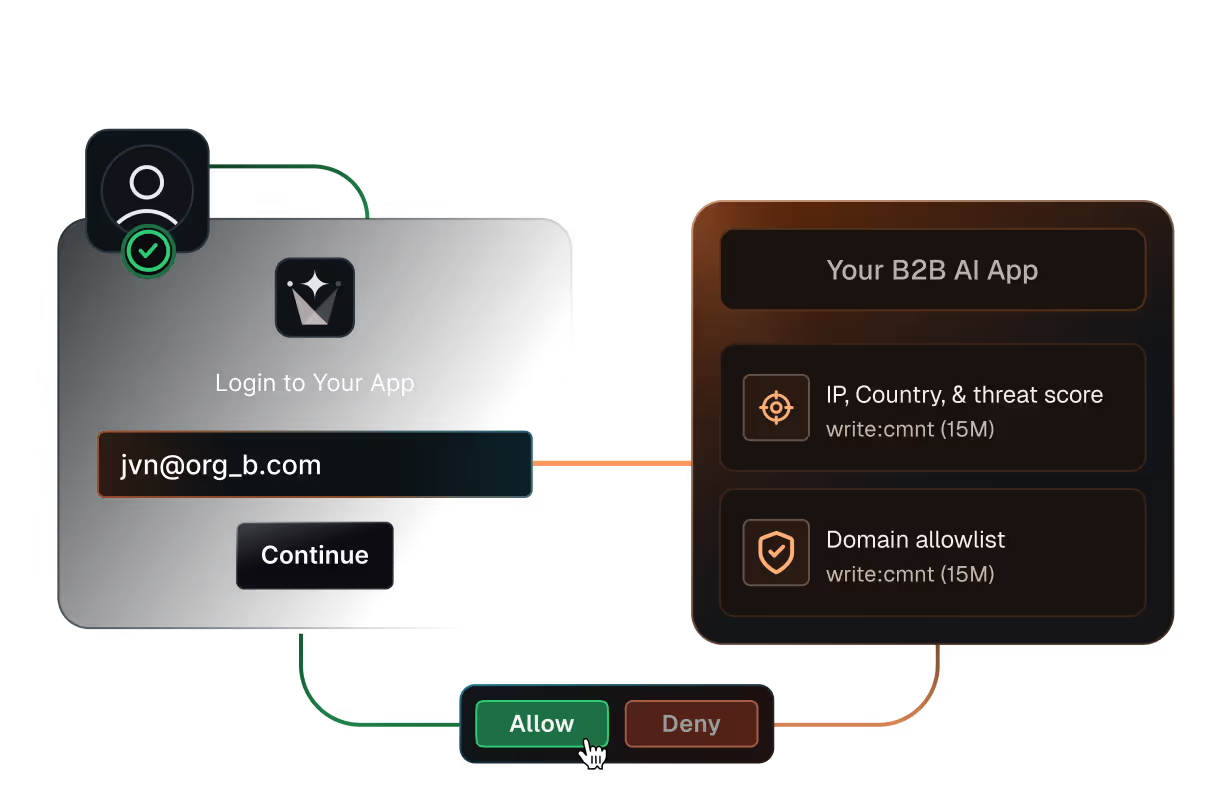
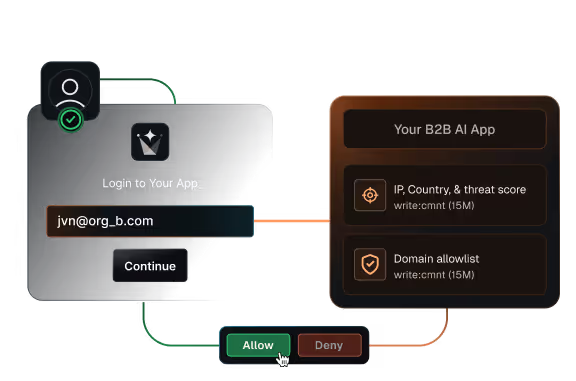
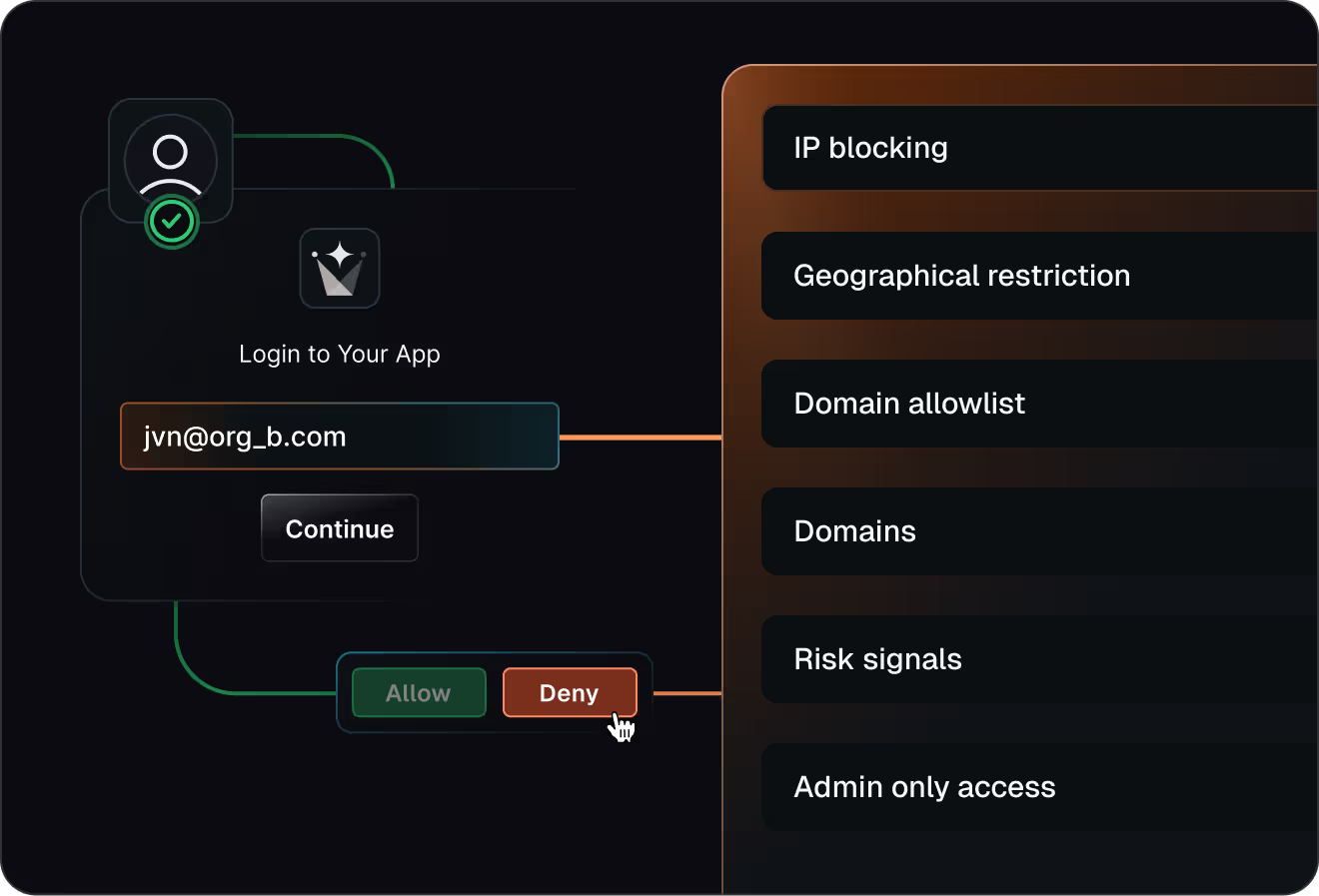
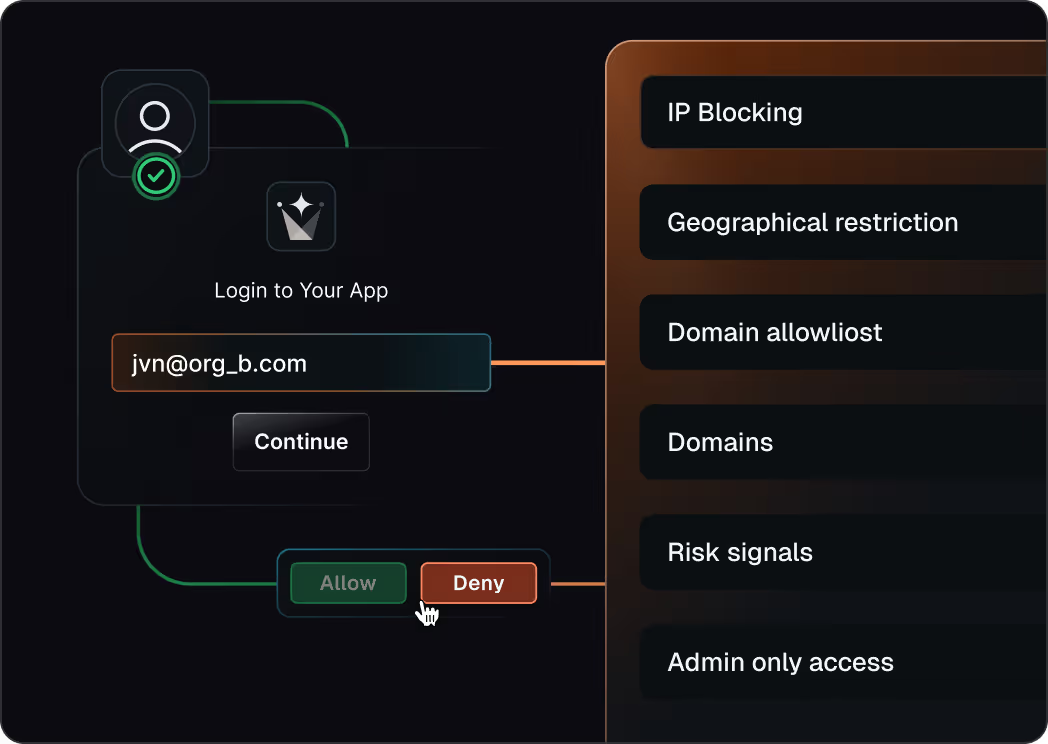
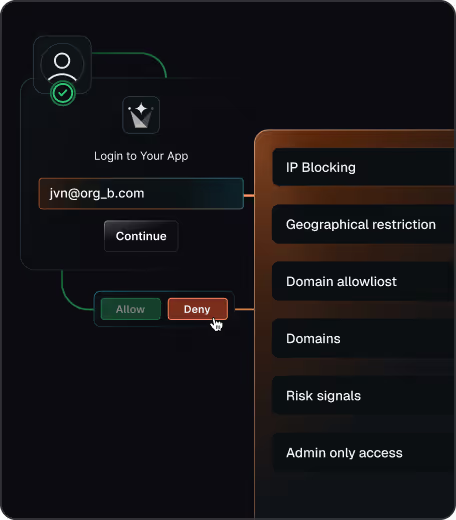
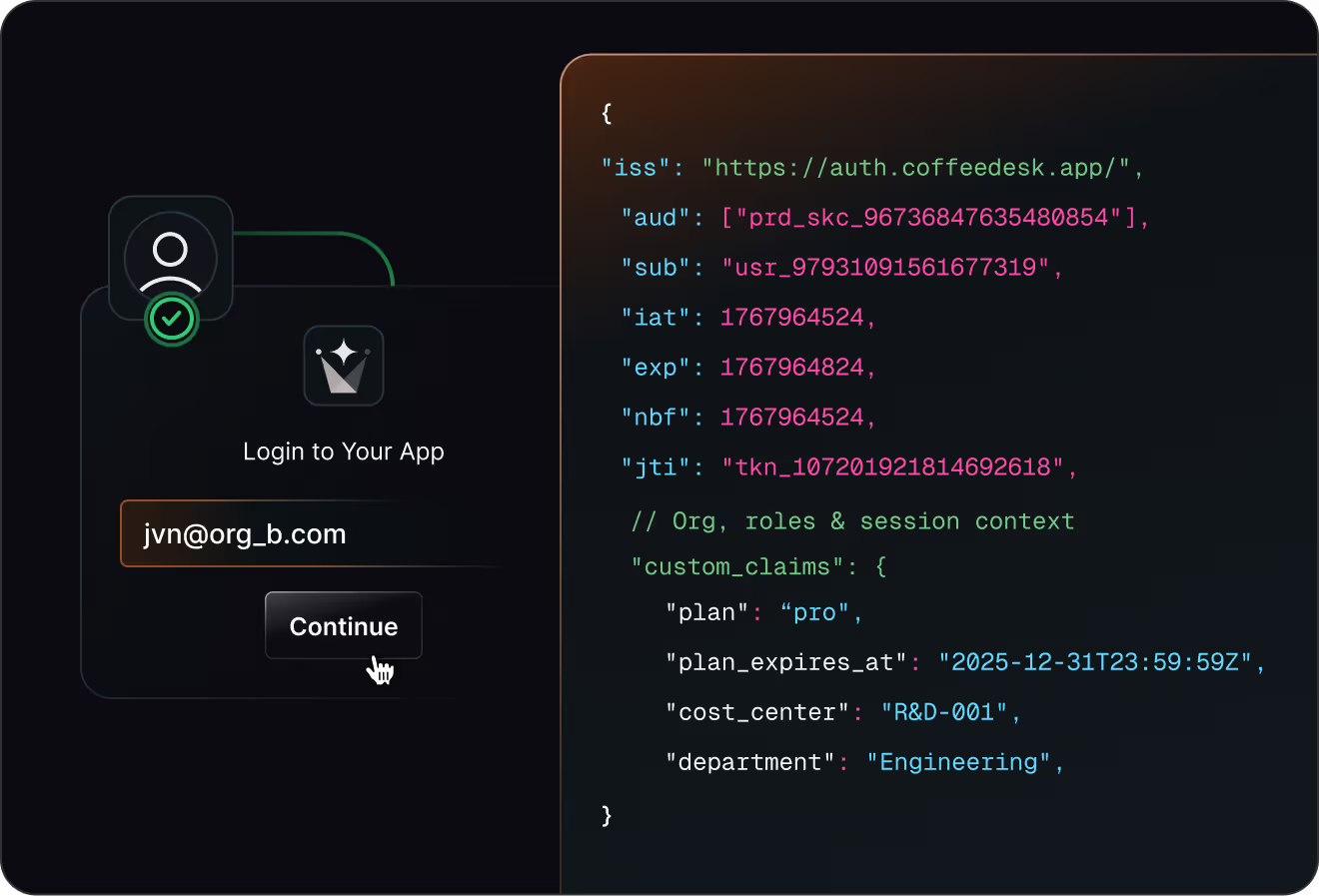
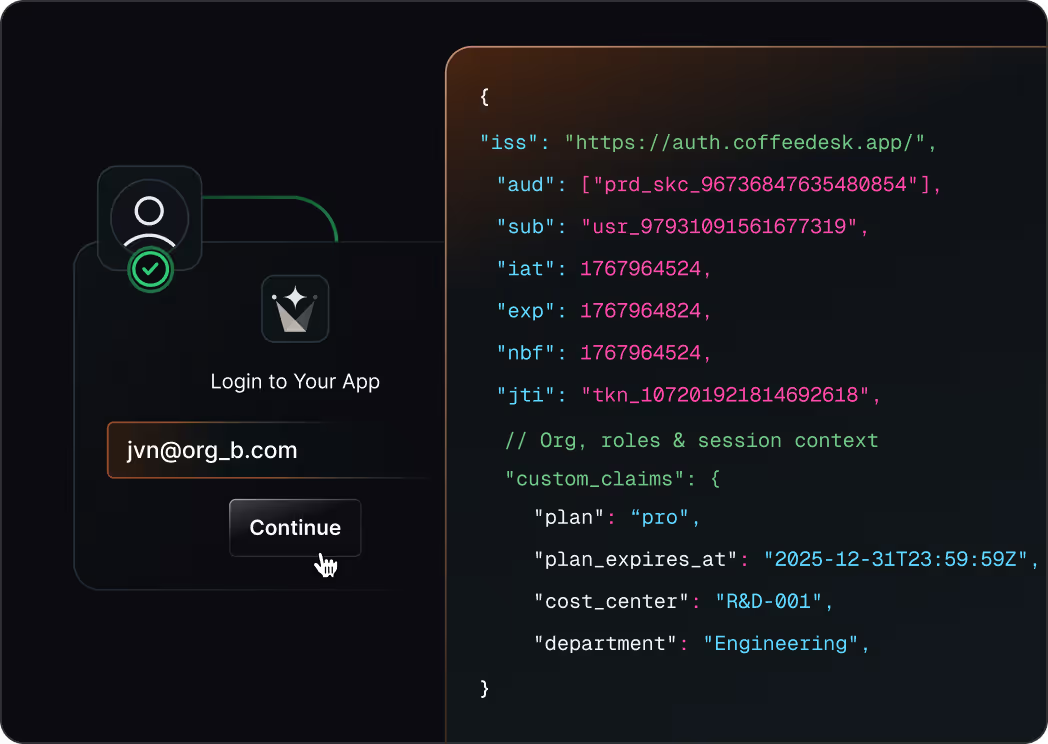
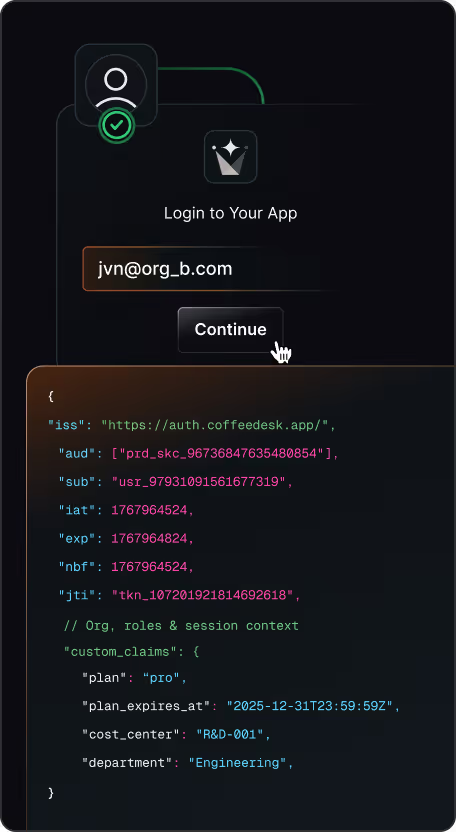
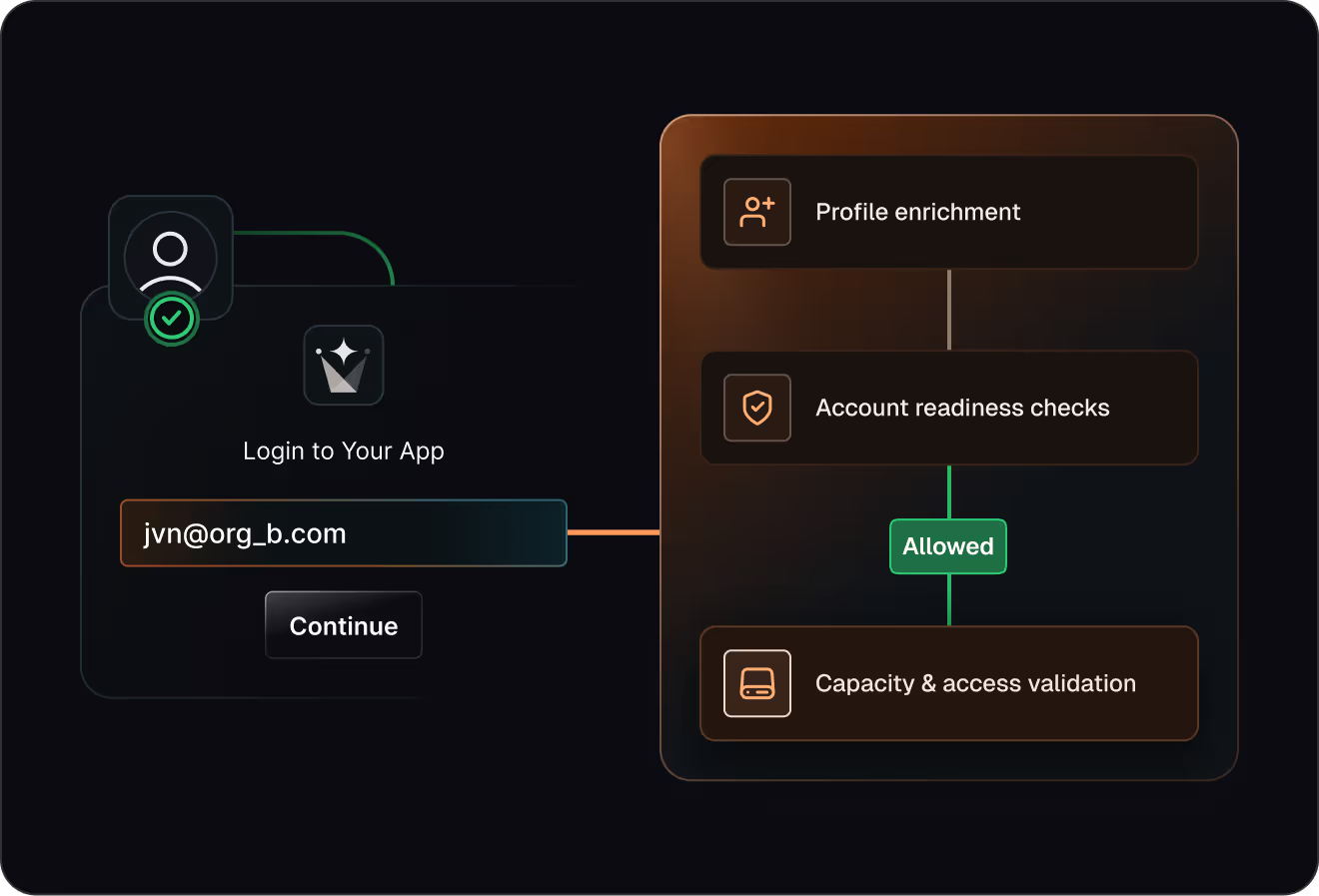
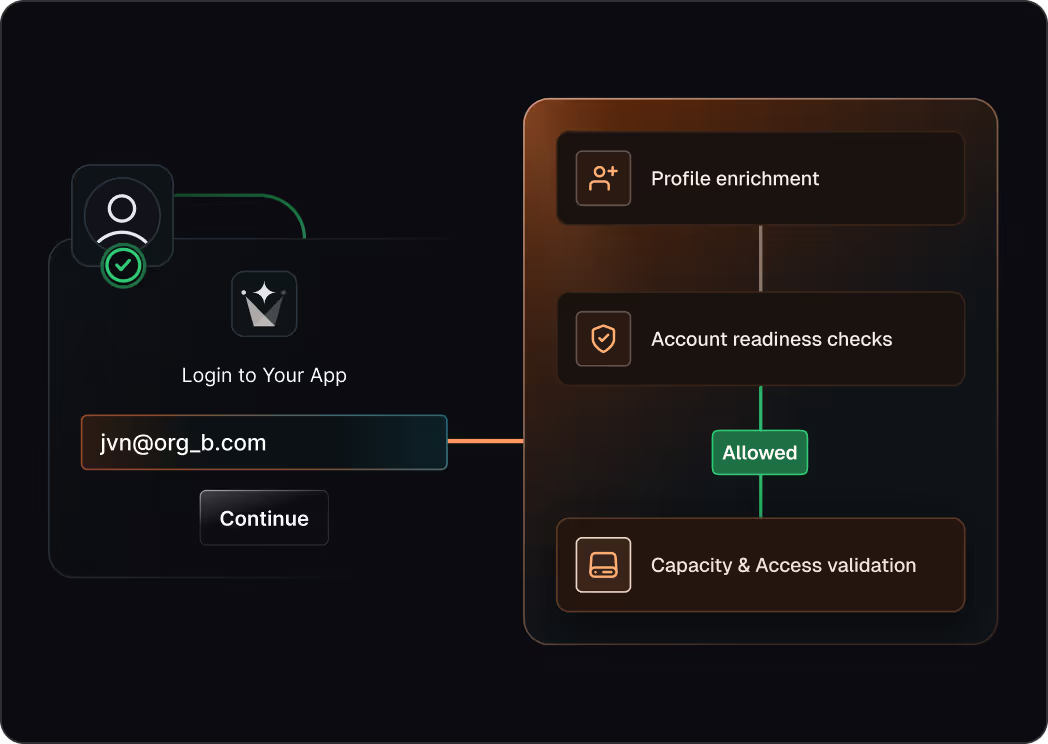
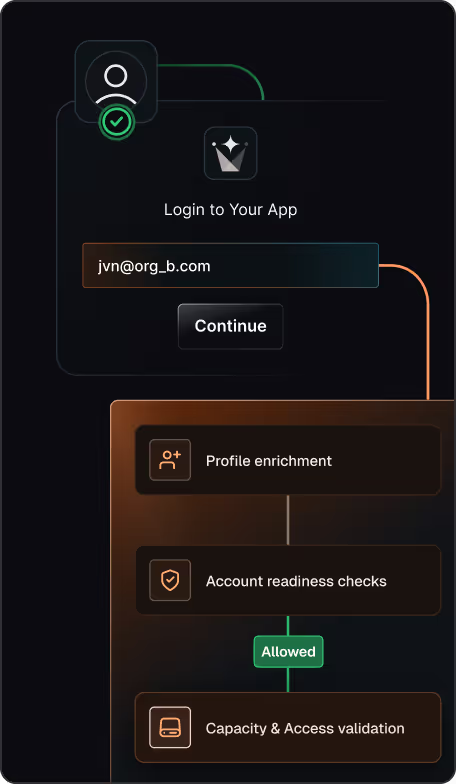
Block risky access early
Stop signups, logins, and tokens that violate your security rules
Block by IP, region, domain, or
risk signals at signup or invite time
Enforce allow lists and enterprise-only rules with fail-closed behavior
Apply the same checks to users, invitations, and
machine-to-machine tokens