Auth0 for Agents: Alternatives for B2B AI platforms
Modern B2B AI products are no longer centered on a single human logging into a single application. They are distributed systems where users, organizations, services, APIs, and autonomous agents all operate within shared trust boundaries.
That shift exposes a mismatch between how most authentication platforms were designed and how AI platforms now behave in production.
Auth0 and similar tools solved login, user authentication, and enterprise SSO extremely well. As agents move from experiments to core infrastructure, authentication stops being a UI concern and becomes part of the system architecture itself.
This post looks at why agent authentication is now foundational for B2B AI platforms, where traditional auth models break down, how teams evaluate both general and agent-focused alternatives, and where full-stack identity approaches fit.
Why agent authentication is now unavoidable
In AI platforms, agents are not background jobs. They call APIs, invoke tools, coordinate workflows, and act on behalf of users or entire organizations. They often do this continuously and without human interaction.
From an architectural standpoint, this creates requirements that human-centric authentication never had to solve:
- Non-interactive credentials that can be scoped, rotated, and revoked
- Clear organization boundaries for agent actions
- Delegation models that reflect real authority
- Audit trails that explain who acted and why
When agent identity is treated as an afterthought, these guarantees are difficult to provide consistently.
What breaks when identity is not foundational
Most teams start with a familiar setup. Human users authenticate through a standard auth provider. Agents use API keys or long-lived tokens. Organization context is injected through claims or middleware.
This approach works initially but degrades as systems grow. Common failure modes include:
- Agents bypassing org-level access controls
- Credentials that cannot be safely rotated or revoked
- Authorization logic duplicated across services
- Audit logs that lack clear attribution
At that point, authentication is no longer a layer. It is implicit system behavior that only a few people fully understand.
Why Auth0 struggles in agent-driven systems
Auth0 is a powerful and flexible platform. It excels at user authentication, social login, and enterprise SSO. Its core model, however, is application-centric and human-first.
In agent-heavy systems, this shows up in several ways. Machine to machine tokens exist but are not modeled alongside users and organizations. Delegation and impersonation require custom logic. Organization context must often be encoded manually and enforced outside the platform.
Teams can and do build agent systems on Auth0. However, the trade-off of using auth0 for agents is ongoing ownership of identity behavior that lives outside the auth layer.
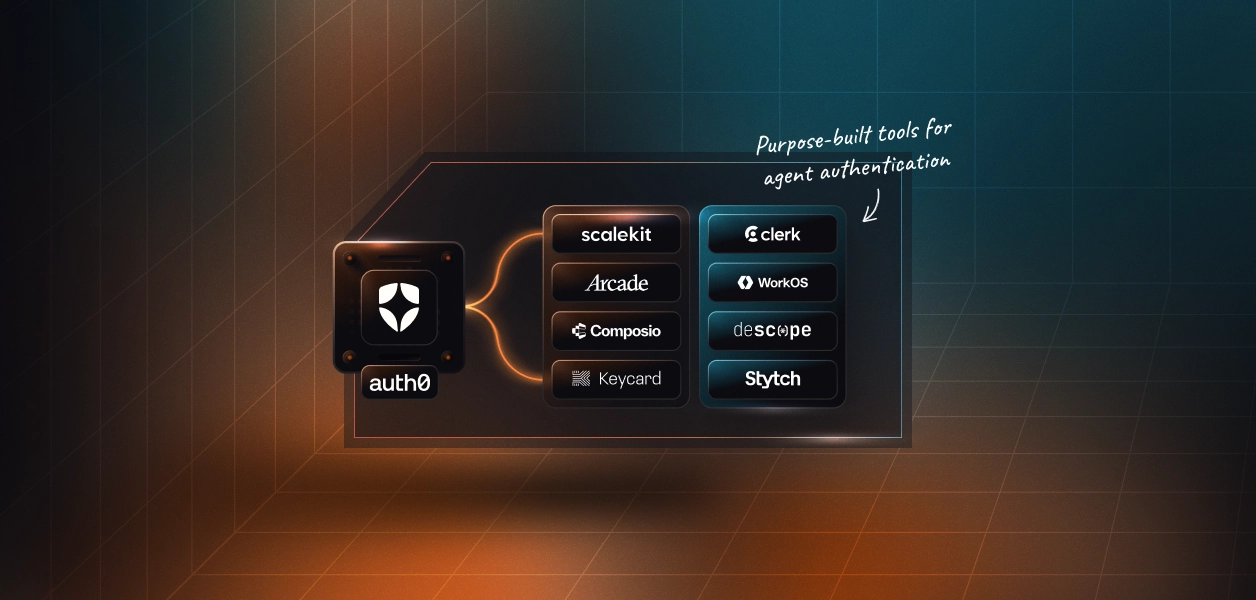
Purpose-built tools for agent authentication
A growing set of vendors are explicitly trying to address the gap between traditional authentication and agent-driven systems. These tools start from the assumption that software, not just humans, acts autonomously and needs security primitives that reflect that reality.
Auth0 for Agents
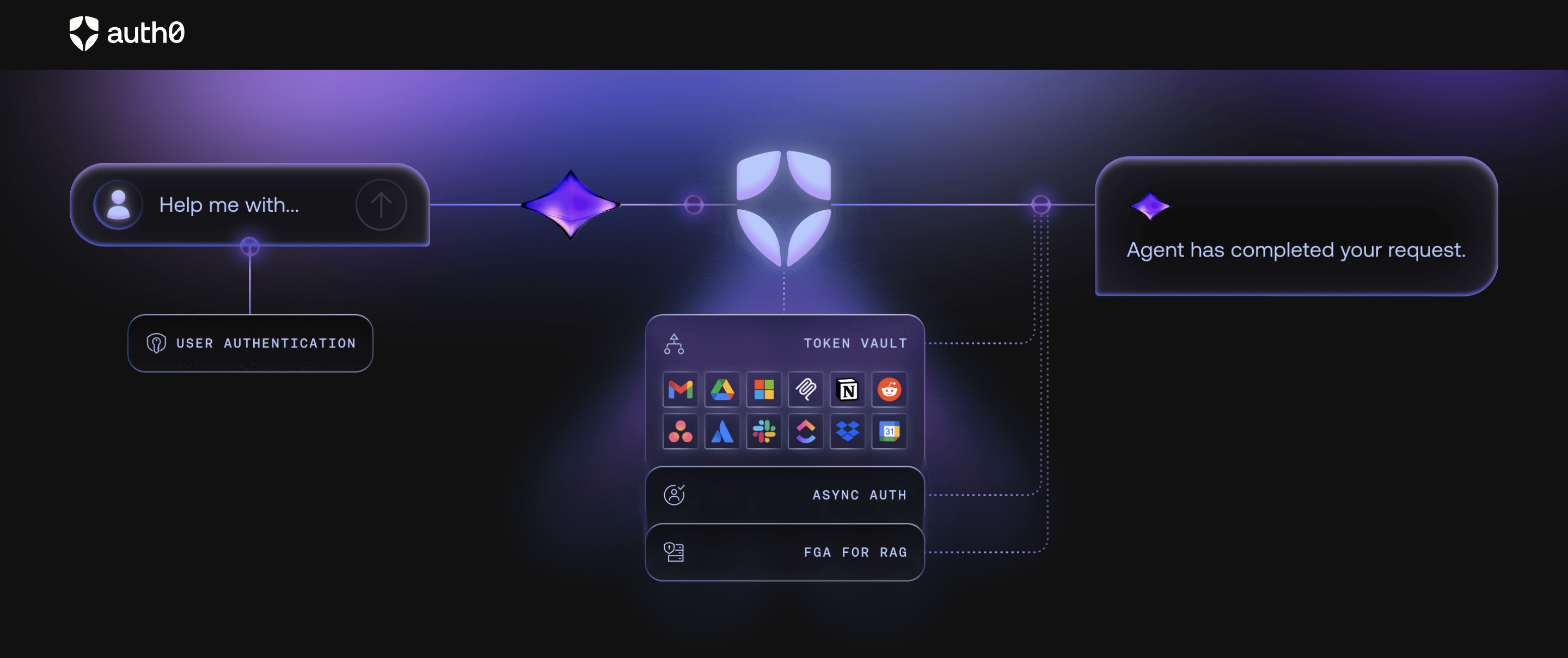
Auth0 for Agents is an attempt to extend Auth0’s existing OAuth and machine to machine capabilities to better support agent access patterns. It builds on familiar constructs such as clients, scopes, and tokens, which makes it approachable for teams already invested in the Auth0 ecosystem.
From an architectural perspective, it works best when:
- Agents are closely tied to specific applications
- Organization context can be derived externally
- Delegation rules are simple
What to keep in mind is that agent identity remains an extension of an app-centric model rather than a first-class concept.
Keycard.sh
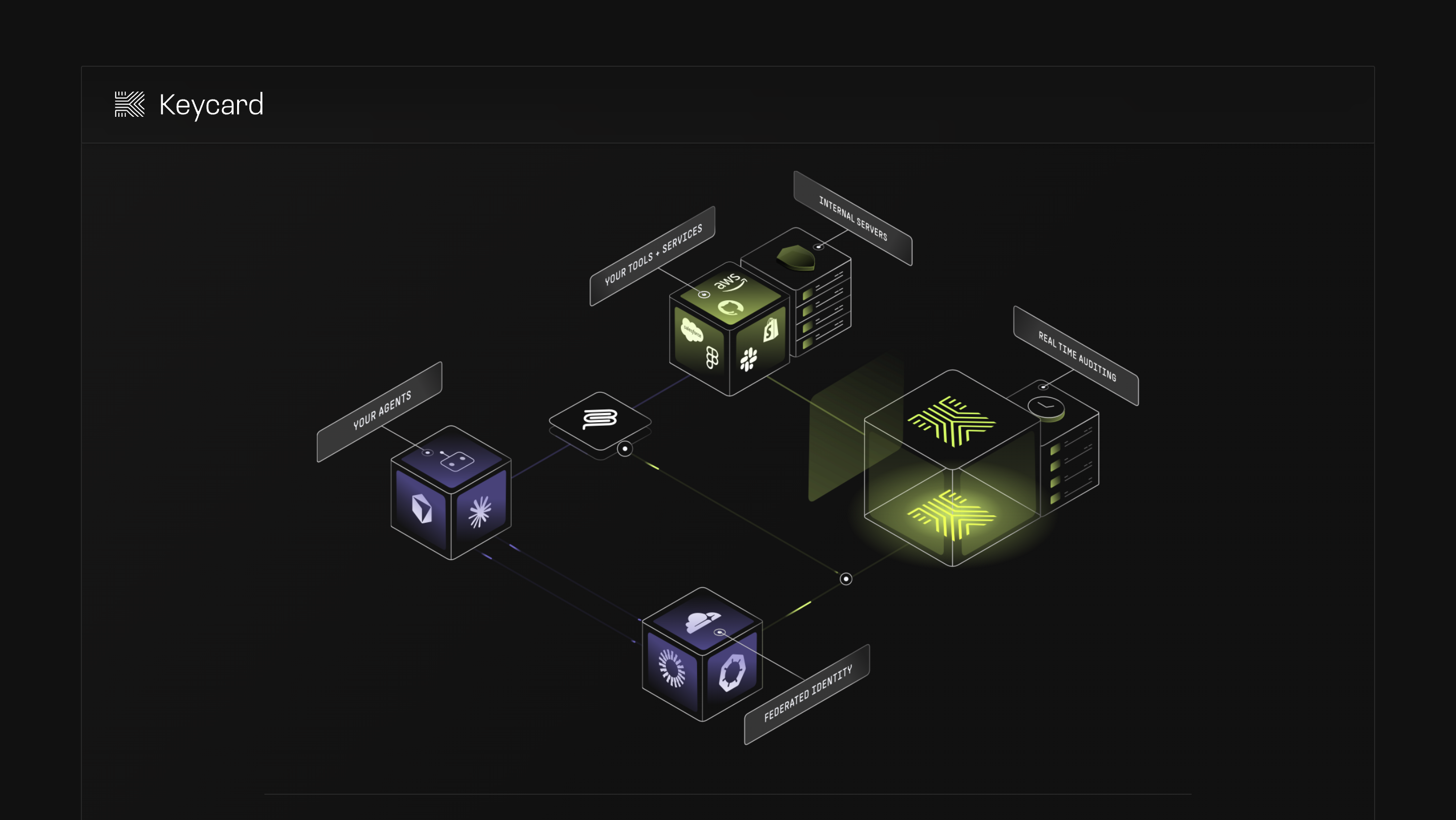
Keycard.sh focuses narrowly on secure credentials for agents and APIs. It is designed for teams that need to issue, rotate, and revoke agent credentials with minimal overhead.
Architecturally, Keycard.sh treats agents as credentialed entities rather than participants in a broader identity graph. This makes it a good fit for infrastructure teams that want strong control over service access without introducing user or organization semantics.
Common considerations include simplicity, clear credential lifecycle, and limited surface area.
What to keep in mind is that user identity, organization boundaries, and delegation typically need to be handled elsewhere.
Arcade
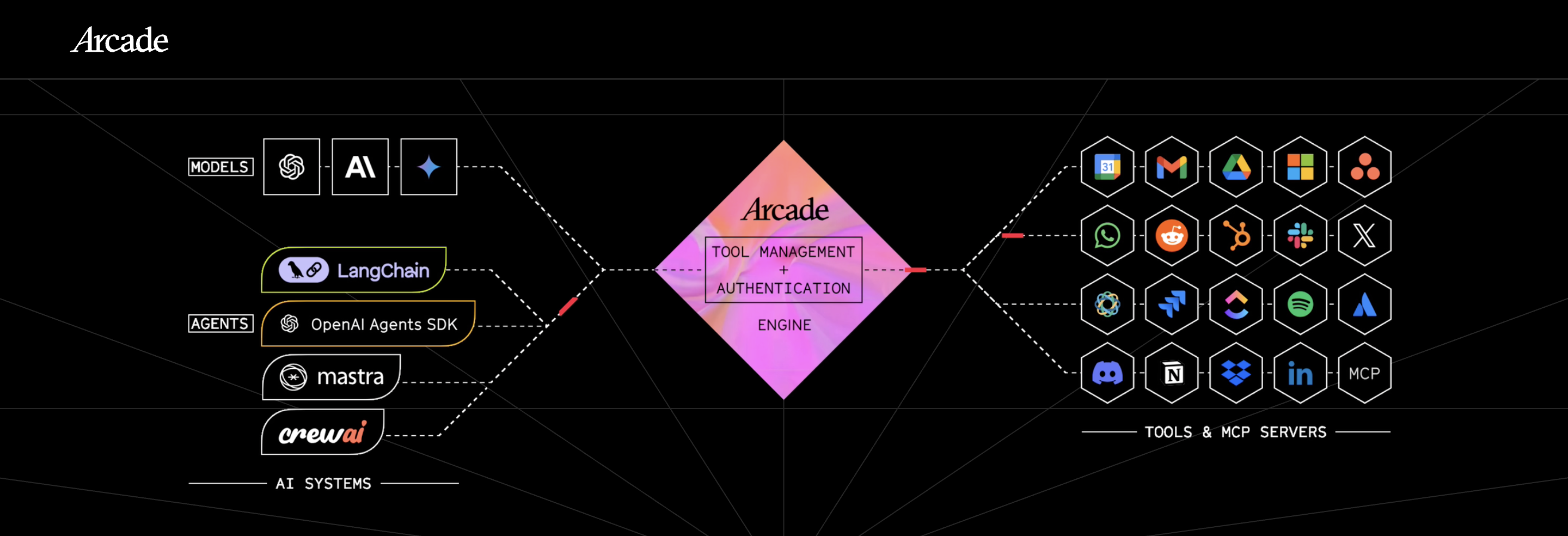
Arcade focuses on securing tool execution for AI agents. Its primary concern is ensuring that agents can only invoke approved tools with appropriate permissions.
In practice, Arcade often sits alongside an existing identity system. It enforces constraints at the tool layer rather than defining who an agent is within the broader system.
Common considerations include strong controls around execution and safety.
What to keep in mind is that Arcade does not aim to be a system of record for identity or access across an entire platform.
Composio
Composio positions itself as an integration layer for agents, enabling access to a wide range of third-party tools and services.
From an identity standpoint, Composio assumes that authentication and authorization are handled upstream. Agents inherit access implicitly through configured integrations rather than through explicit identity modeling.
Common considerations include speed of integration and breadth of supported tools.
What to keep in mind is that identity and auditability are indirect and depend heavily on how upstream systems are designed.
Scalekit
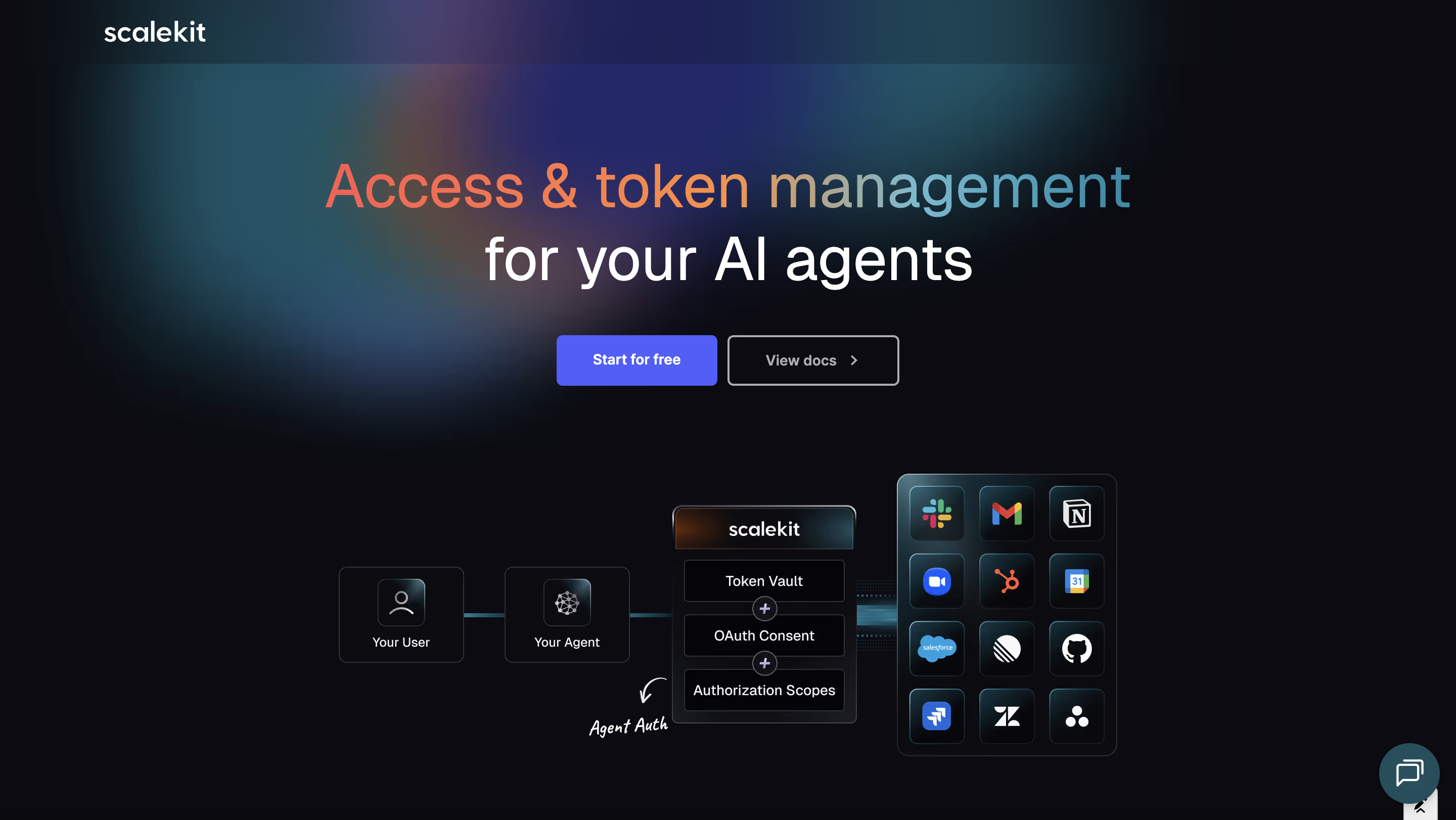
Scalekit treats identity as a system boundary rather than a login feature. It is designed for platforms where users, organizations, agents, APIs, and MCP servers all need to operate under a shared and consistent security model.
The core design choice is an organization-first identity model. Organizations are the primary boundary for authentication, authorization, and policy. Users and agents exist within that boundary rather than alongside it.
In practice, this means:
- Agents are modeled as first-class actors, not service accounts
- OAuth 2.1 is used consistently for humans, agents, and services
- Delegation is explicit and scoped rather than inferred
- Tokens carry organization context by default
- Audit logs span human and non-human actions uniformly
For architects, the benefit is that identity behavior is enforced by the platform rather than reconstructed in application code. For developers, this reduces glue logic, edge cases, and long-term maintenance as agent usage grows.
This approach is opinionated, but it aligns closely with how modern B2B AI platforms behave in production.
General authentication platforms teams try to extend
Most B2B AI teams start with a general-purpose authentication platform. These systems are mature, widely trusted, and well understood by security teams. As agents become more prominent, teams attempt to extend these platforms rather than replace them.
Clerk
Clerk is optimized for fast and polished user authentication. It provides strong primitives for sessions, user management, and frontend integration.
It is commonly used when:
- Agents act as short-lived extensions of user actions
- Identity needs are primarily user-driven
- Frontend experience is a priority
What to keep in mind is that Clerk remains fundamentally user-first, and complex agent scenarios require custom identity logic.
Stytch
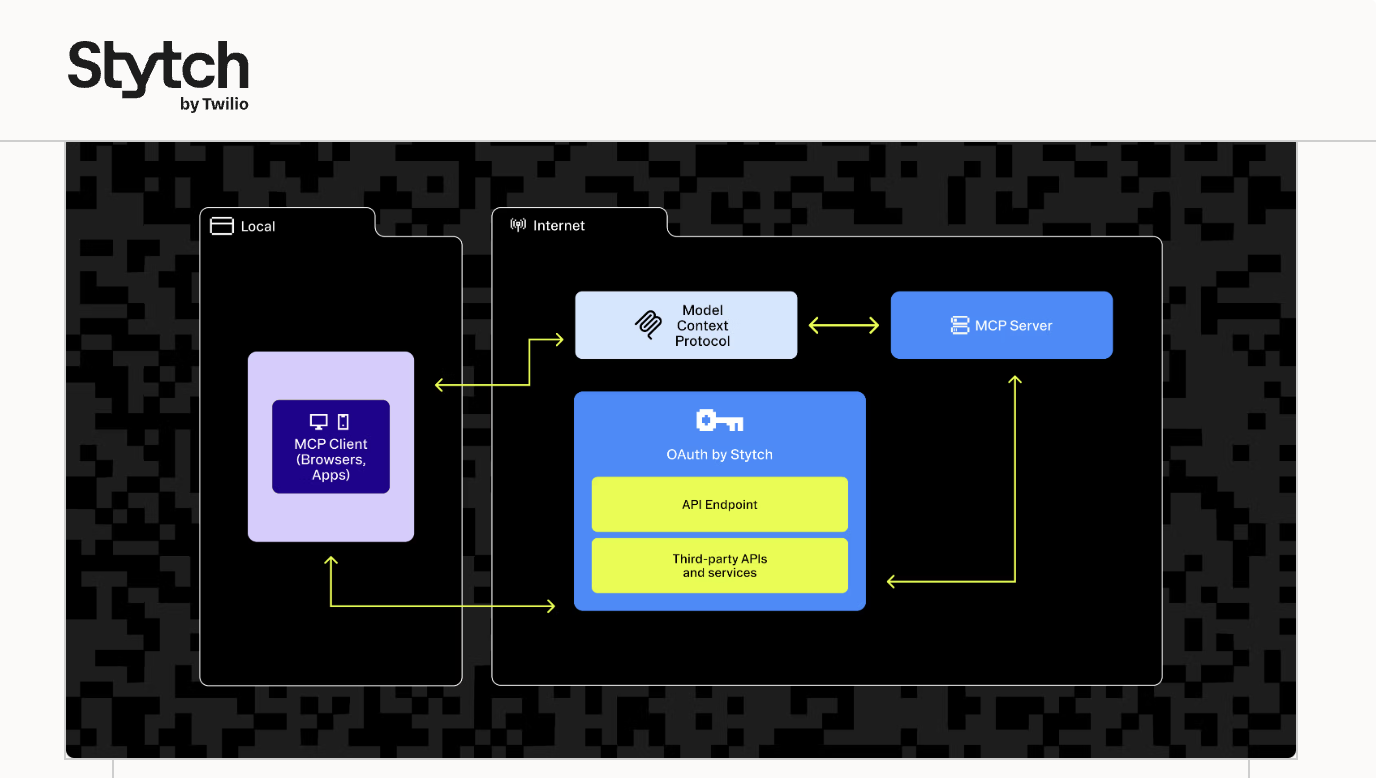
Stytch provides flexible, API-driven authentication with support for both user and machine to machine access. This makes it attractive to teams that want control without heavy abstraction.
Architecturally, Stytch does not impose a specific identity model. Agents, users, and organizations are represented through tokens and metadata defined by the application.
Common considerations include flexibility and low-level control.
What to keep in mind is that long-term consistency and policy enforcement become the responsibility of the application rather than the auth platform.
WorkOS and Pipes

WorkOS is focused on enterprise readiness, with strong support for SSO, directory sync, and admin workflows. Pipes extends this by enabling identity events to be ingested, transformed, and routed to downstream systems.
Pipes is particularly effective for provisioning, deprovisioning, and keeping access state synchronized across services. It treats identity as a source of events rather than a unified model.
In agent-heavy systems, this often results in agents being authenticated separately from users and organizations, with Pipes used to keep systems loosely aligned.
Common considerations include excellent enterprise integrations and clear operational workflows.
What to keep in mind is that agent identity, delegation, and auditability remain external concerns.
Descope

Descope emphasizes configurable authentication flows over a fixed identity schema. This allows teams to experiment with onboarding, authentication, and authorization logic.
For AI platforms, Descope can support agent-related flows, but complex delegation and organization-aware policy typically require additional services or custom code.
Common considerations include flexibility and speed of iteration.
What to keep in mind is that as flows multiply, maintaining a coherent identity model becomes more challenging.
Orchestration versus foundational identity
Across general platforms, a consistent pattern emerges. They provide strong primitives such as tokens, authentication events, enterprise integrations, and workflow triggers. They intentionally avoid enforcing a single identity model across users, organizations, agents, and services.
This leads to two architectural approaches.
An orchestration-first approach typically involves:
- Identity signals flowing between systems
- Authority reconstructed at runtime
- Policy enforced in multiple services
- Agents authenticated but not explicitly modeled
A foundational identity approach typically involves:
- Explicit modeling of all actors
- Authority enforced at the identity layer
- Native delegation and scoping
- Unified auditability across humans and agents
Both approaches can be secure. The difference is where complexity lives.
Fitment overview
Closing thoughts
The question behind Auth0 for agents is not about features. It is about whether identity is treated as an event stream or as a system boundary.
For B2B AI platforms where agents are central to how value is delivered, that distinction becomes architectural. Making it explicit early often determines how fast teams can move later.
Frequently asked questions
Do agents really need first-class identity?
If agents act independently, hold credentials, or operate across organizations, they benefit from being modeled explicitly. Treating them as anonymous services makes auditing and policy enforcement harder over time.
Can API keys work for early-stage agents?
API keys are often sufficient early on. As agents gain scope and autonomy, teams usually need revocation, scoping, delegation, and auditability that API keys do not provide well.
Is OAuth overkill for agents?
OAuth adds structure and lifecycle management. For systems with multiple actors and enterprise requirements, that structure reduces long-term risk.
When should teams move beyond Auth0?
Teams typically reassess when agents become product-critical, security reviews intensify, or identity logic starts spreading across services.
Can orchestration-based approaches scale?
They can, but they place ongoing responsibility for identity semantics on the application. Some teams prefer that control. Others prefer to push it down into the identity layer.











