Machine-to-machine authentication in B2B SaaS
Machine to machine authentication in B2B SaaS
In today's AI-driven ecosystem, machines are talking to each other more than ever. Imagine AI agents autonomously pulling data from your platform, two enterprise apps syncing in real-time, or a CI/CD pipeline deploying code without a single human login.
With the rise of AI-driven integrations and protocols like the emerging Model Context Protocol (MCP: an open standard for connecting AI assistants to tools and data) means even more automated agents need access to your SaaS APIs.
Ensuring that these non-human interactions are secure and trusted is now crucial. This is where machine-to-Machine (M2M) authentication comes in.
In this guide, we'll explore M2M authentication in depth.
What is M2M authentication in B2B SaaS?
Machine-to-machine (M2M) authentication is the process of verifying the identity of a machine or software agent when it connects to another system, without a human directly logging in.
In a B2B SaaS context, "machine" usually means a server, microservice, script, or application – anything that calls your SaaS product’s API or services autonomously.
M2M authentication provides a secure handshake between these services, so that only authorized machines (or programs) can access data or perform actions. It answers the question: “Is this request coming from a legitimate, trusted machine client?”
This is analogous to user authentication (where a person enters credentials to prove who they are), but here a piece of software presents credentials instead.
Traditional username/password logins don't fit this scenario; instead, we use keys, tokens, certificates, or other credentials that a machine can present automatically.
M2M authentication vs. authorization
Before we delve into methods, let's clarify authentication vs. authorization in the machine-to-machine world – and how it parallels human login scenarios:
- Authentication answers “Who are you?” – It verifies identity. For a human, this might be a username/password or SSO login that proves you are Richard Hendricks (You wish!) and not an imposter.
- For a machine, authentication might involve presenting an API key or certificate to prove it’s the right service. M2M authentication is all about a client machine proving its identity to a server. For example, a microservice will authenticate by sending its client ID and secret to an auth server, or by using a signed certificate.
- Authorization answers “What are you allowed to do?” – It determines access rights after identity is confirmed. In a human context, authorization might involve checking the user’s roles/permissions to decide what data they can see.
- In an M2M context, authorization usually comes in the form of an access token that encodes what the machine can access or do. A machine proves who it is (authN) and then gets back a token that says “this machine can read invoices and create payments, but not delete accounts” (authZ).
In M2M flows, authentication and authorization are tightly linked. Typically, a machine authenticates (for instance, using a client certificate or secret) and receives an authorization token (often a JWT) in return, which it then presents to the resource it wants to use. The token encapsulates what it’s allowed to do. Importantly, authorization is always dependent on successful authentication: a service must prove its identity first, then it gets permissions.
Key concepts and components of M2M authentication
Before we explore how M2M auth works, let’s define a few key concepts that will come up repeatedly:
M2M credentials/tokens
These are the digital keys or tickets used in machine authentication. Examples include API keys, OAuth access tokens, JSON Web Tokens (JWTs), client certificates, etc. They come in different forms (strings, signed tokens, etc.) but serve the same purpose: proving the calling program is legitimate and conveying its access rights.
In OAuth flows, the credentials often include a client ID and client secret (like a username/password for the machine) which are used to obtain an access token. The access token (typically a JWT) is then presented to APIs as proof of authorization.
OAuth 2.0 authorization framework
OAuth 2.0 is the industry-standard protocol for delegating authorization, and it's heavily used for M2M scenarios. In simple terms, OAuth provides a standardized way for one service to securely access another service on behalf of an identity. For M2M, the relevant OAuth flow is typically Client Credentials Grant, where a service uses its own credentials to get an access token (no human user involved).
OAuth 2.1 builds upon OAuth 2.0, consolidating security best practices. In M2M contexts, OAuth 2.1 mandates stricter defaults, enforces HTTPS, removes insecure flows (like implicit and password grants), and enhances token handling security.
JSON Web Tokens (JWTs)
JWTs are a standardized format for tokens (a compact, URL-safe JSON-based token format) that can securely carry information (claims) about a user or machine identity. In M2M auth, JWTs often serve as access tokens issued by your auth server.
They are cryptographically signed, so the receiving API can verify they’re legitimate. A JWT might contain claims like the client’s identity, what it’s allowed to access (scopes), and an expiration time. Because JWTs are self-contained and verifiable, they’re very useful for distributed systems – the resource server can trust the token without needing to call back to the auth server every time.
Unified auth layer
This is more of an architectural concept: it means having a single, cohesive approach to authentication and authorization for both users and machines. It’s best to move toward a unified identity platform where the same identity provider (IdP) or auth service issues tokens for human users (interactive logins) and for machine clients. For example, instead of having separate systems (one for user SSO, another for API keys, another for internal service auth), you unify them. Why? It simplifies management, improves security (one central place to enforce policies like token expiration, scopes, audits), and makes it easier to plug into standards like OIDC/OAuth for everything.
How does M2M authentication work in B2B SaaS?
There are several common methods and protocols for implementing M2M auth. In practice, many SaaS platforms use a combination of these, often migrating from simpler approaches (like static API keys) to more robust ones (like OAuth tokens). Here we’ll cover the key methods:
API keys
API keys are one of the simplest forms of machine authentication. An API key is typically a long, random string (like abc123xyz456...) that a client includes with API calls (often in an HTTP header or as a query parameter) to identify itself. If the key is valid, the request is allowed.

Using an API key is like having a single password that gives access to the API. Some characteristics of API keys in M2M auth:
- Simplicity: API keys are straightforward to implement – generate a random key, give it to the client, and on each request the server checks if the key matches. They are not usually signed or encrypted; security relies entirely on keeping the key secret. There’s no complex protocol involved, which makes API keys popular for simple integrations.
- Limited authorization capabilities: Out of the box, an API key is just an identifier – it doesn’t inherently carry scopes or permissions. All it says to the server is “this request is from client X.” Any permissions or limits have to be looked up server-side (for example, the server might store that client X is read-only). API keys cannot carry rich claims like a JWT can.
- Security concerns: API keys can be very powerful but also risky if mishandled. They often don’t expire (unless manually revoked), so a leaked key could provide indefinite access. API keys in code or config files have a habit of accidentally leaking – e.g. getting committed to a public repo or exposed in logs. There's no cryptographic binding – if an attacker copies the key, the server can’t tell the difference.
- Use cases: Many older APIs and internal tools still use static API keys, and for simple use cases they can suffice (e.g. a low-risk integration that only pulls non-sensitive data). But for modern SaaS with multi-tenant data and higher security needs, API keys alone are seen as insufficient and are often augmented or replaced by OAuth 2.0 methods.
In short, API keys are the most rudimentary form of M2M auth – easy to set up but with limited flexibility and potential security downsides. If you do use them, they should be treated like passwords: transmitted over TLS, rotated periodically, and ideally scoped to minimal access.
Certificate-based authentication (Mutual TLS)
Another method for M2M authentication is using digital certificates to establish identity. This is commonly implemented as mutual TLS (mTLS), where both the client and server present X.509 certificates during the TLS handshake.
In effect, the TLS connection itself does the authentication: the client proves its identity by presenting a certificate signed by a trusted authority, and the server does the same. If both sides trust each other’s certificates, the connection is established and considered authenticated.
Key points about certificate-based M2M auth:
- Strong security: mTLS provides a very high level of assurance. It’s the backbone of many zero-trust networks, ensuring that both sides are exactly who they claim to be at the network layer. Certificates are hard to forge if properly managed, and the use of TLS means the traffic is encrypted and protected in transit.
- No additional tokens needed: With mTLS, the authentication is baked into the transport. Once the handshake is done, the server already knows the client's identity (from the certificate subject or fingerprint), so API calls can trust the connection. This can simplify certain scenarios (no separate auth call to an OAuth server), but...
- Operational complexity: Managing certificates is non-trivial. You need a Public Key Infrastructure (PKI) to issue and revoke certs, handle expiration, rotation, etc. In a dynamic SaaS environment with many customers and services, distributing and trusting the right certificates can become a headache. If a certificate expires or a client’s certificate needs to be revoked, you need processes to update them. This overhead often makes pure mTLS less attractive for large-scale external integrations.
- Limited granularity: A certificate typically authenticates the machine or client organization, but it doesn't inherently carry fine-grained scopes or permissions (beyond maybe embedding some roles in certificate attributes, which is clunky). So mTLS answers "who is calling," but for "what can they do," you often still need to overlay an authorization system.
To summarize, certificate-based auth (mTLS) is secure and well-suited for internal or highly regulated environments where you control all the clients (like internal microservice calls or connections in a zero-trust corporate network). B2B SaaS providers often choose OAuth2-based token auth as a more flexible approach for external use cases.
OAuth 2.0 Client Credentials Flow
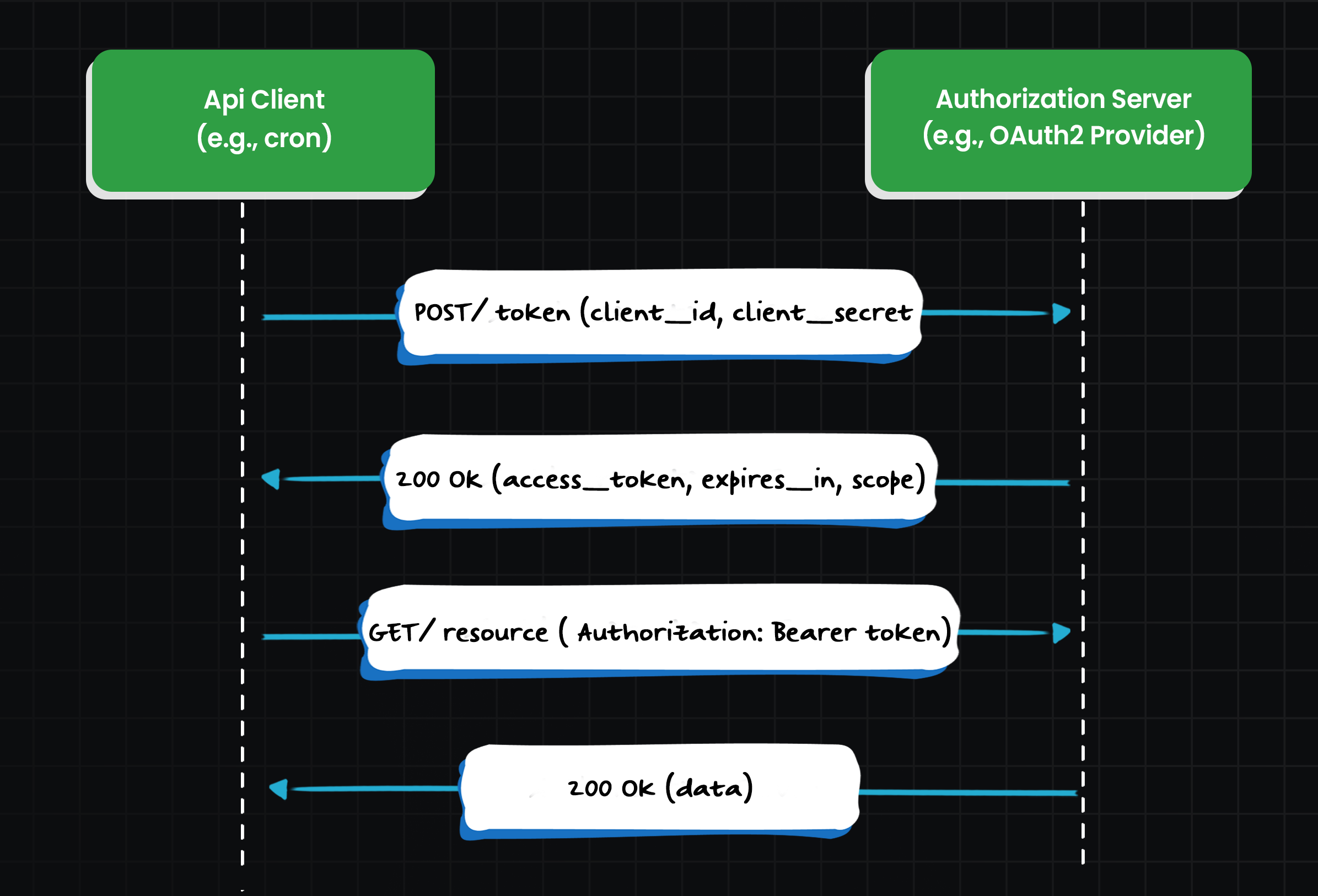
OAuth 2.0 is the go-to framework for modern API authentication and authorization, and the Client Credentials grant is OAuth’s solution for machine-to-machine auth. In this flow, a service (the client) uses its own credentials to obtain an access token from an authorization server, and then uses that token to call the target API (the resource server).
This OAuth flow is the backbone of most secure M2M authentication in modern SaaS. It externalizes auth to a dedicated service (the authorization server), which issues tokens that the API trusts.
Here's a step-by-step of how the OAuth2 Client Credentials flow works in a B2B SaaS scenario:
- Registration: First, the machine client is registered with the authorization server. You (the SaaS provider) might create a
client_idandclient_secretfor customer XYZ's data sync service or for an internal microservice. Theclient_idis public (identifier), and theclient_secretis like a password. This is often done via a developer portal or admin console beforehand. - Token request: When the client (machine) wants to authenticate, it sends a token request to the OAuth authorization server’s token endpoint. This is a secure POST request that includes the client’s ID and secret, and specifies it wants to use the
client_credentialsgrant. It can also request specific scopes at this time – basically asking for certain levels of access. For example, it might request the scopeinvoices:read or payments:writeif those are defined. - Authentication and token issuance: The authorization server verifies the client ID and secret. If valid and the client is allowed to have the requested scopes, the server issues an access token back to the client. This access token is typically a JWT (JSON Web Token) signed by the server. The token will include claims like the client’s identity, the granted scopes, and an expiration timestamp.
- Accessing the resource: The client now includes this access token in the Authorization header (as a Bearer token) on requests to the resource server (your API). For example, it might call
GET /api/v1/customerswith headerAuthorization: Bearer <token>. - Token validation: The resource server (your API) validates the token. Because it's a JWT, the API can check the signature (using the auth server’s public key) and ensure the token is not expired and has the right scopes for the endpoint. If everything checks out, the request is authorized and processed. If the token is missing/invalid, the API returns a 401/403 error.
- Expiration and refresh: Typically, access tokens in this flow are short-lived (e.g. 5-60 minutes) and not automatically refreshed. When the token expires, the machine can simply repeat step 2 to get a fresh token using its client credentials. (Unlike user-centric flows, no user interaction needed, so refresh tokens are often unnecessary – the machine can just get a new token as needed)

Benefits of using OAuth client credentials flow include:
- Granular access control: Tokens can be scoped. Your client might get a token that’s only valid for certain APIs or actions, embodying the principle of least privilege. For instance, you could issue one token that only permits read-only access to a particular dataset.
- Short-lived tokens: Unlike static API keys, OAuth access tokens usually expire quickly. This limits the window of misuse if a token gets compromised. It also means you aren't stuck with long-lived credentials; rotation is built-in (just issue a new token). Long-lived credentials are a known risk — they “silently allow access indefinitely” if not rotated, so moving to short-lived tokens mitigates that.
- Strong security and standards: The OAuth process and tokens carry signatures, use HTTPS, and follow well-vetted standards. It's harder to forge a token (you'd need the signing key), and widespread adoption means a lot of community knowledge and tooling exist to get it right.
- Auditing and revocation: Since an auth server issues tokens, you can centrally log and monitor token issuance. If a problem is detected, you can revoke credentials (e.g., disable the client or change its secret to prevent new tokens) and have a good view of which clients are requesting what.
More recently, OAuth 2.1 strengthens this flow by enforcing clearer requirements around token handling, mandatory use of HTTPS, and removing ambiguity, making integrations more secure by default.
For B2B SaaS providers, implementing OAuth 2.0 (Or OAuth 2.1) for your APIs adds some up-front complexity (you need an authorization server, or to integrate with one, and your APIs need to handle token validation). But it greatly enhances security and scalability for integrations. Many SaaS companies expose an OAuth client-credentials based API for customers/partners instead of (or alongside) older API key mechanisms.
JSON Web Tokens (JWTs) in M2M auth
A JWT is not a separate auth method – rather, it’s the format often used by the methods (especially OAuth) to encode the authorization information. When we say “OAuth access token”, in many implementations it’s a JWT under the hood. However, JWTs can also be used in non-OAuth contexts as a custom auth solution (e.g., a proprietary token system that issues JWTs).
Key things about JWTs in machine authentication:
- Self-contained tokens: A JWT carries information (claims) about the identity and authorization. For example, a JWT payload might look like:
The above token tells us:
- Who issued it (
iss) - For whom (
sub) - What it allows (
scopeof invoices:read) - And an expiry (
exp)
Because it’s signed by the issuer, the resource server can verify it’s legitimate and not tampered with, using a public key.
- Stateless AuthZ: With JWTs, the resource server doesn’t need to call the auth server every time to check a token. It can validate the JWT locally (check signature and claims). This makes things efficient and decoupled – a big plus in distributed systems or multi-region setups.
- Better than API keys for many APIs: JWTs are generally considered more secure and flexible than API keys for managing API access. They support granular permissions via claims/scopes, can enforce expiration, and are cryptographically signed. API keys, by contrast, often require custom logic to impose any limits and rely on secrecy rather than cryptography. The trade-off is that JWTs are a bit more complex to implement (you need the whole signing and validation mechanism).
- Keep them safe: Even though JWTs are more secure, they are still bearer tokens – meaning whoever holds the token can use it. So all the standard security must be in place: transmit only over HTTPS, store them securely (don’t log them in plaintext), and ideally make them short-lived and scope-limited. Also, because JWTs are structured, one must ensure to validate them properly (signature and claims) to avoid certain known JWT attacks (like token replay or misuse if an algorithm is improperly handled).
Types of M2M tokens
Not all machine tokens are equal – they can represent different kinds of identities or access scopes. In a B2B SaaS context, it's useful to distinguish between a few types of non-human tokens that might exist:
Organization-level tokens
These tokens represent an entire customer or account in your system. For example, your SaaS might allow each customer organization to generate a token (or a set of credentials) that grants access to that org’s data via API.
This is common in B2B scenarios: a customer wants to integrate their instance of your app with something else, so they use an org-scoped API key or service account. Organization-level tokens are not tied to any single end-user; they effectively say "this request is coming from ACME Corp’s system, accessing ACME’s data."
They are convenient for wide integration access – e.g., syncing data for the whole company. The downside is that such a token may be too powerful (all-access) and it violates least privilege. The solution is to allow multiple tokens per org, each scoped to specific resources (instead of one master key)
User-level tokens
Sometimes, API access is done on behalf of a specific user even without that user actively clicking anything. A classic example is a personal access token that a user generates to use in scripts. Or an OAuth refresh token that a backend uses to act as a user.
These are user-scoped in the sense that the actions performed with the token are limited by that user’s permissions. For instance, a personal access token might allow a developer to access their own data via API without logging in each time.
In B2B SaaS, user-level tokens are often used for integrations that need to respect user-level permissions and auditing. However, they can be misused for machine auth (some integrations historically just had an "integration user account" and used its API token – essentially a dummy user to represent a machine).
Service-level tokens
This category refers to tokens that represent a distinct service or application (not tied to a customer org or a human user, but to a software service).
For example, your internal microservice “InventoryService” might have its own credentials to call “OrderService”. Or a third-party app developer registers their integration (client ID) and gets tokens that identify that app (like "Salesforce Integration App #123") when calling your API.
Service accounts (in the sense of non-human accounts in your system) often issue service-level tokens. These are useful for clarity and security: you know exactly which service is calling. Many cloud platforms use this concept (e.g., Google Cloud’s service accounts for GCP resources).
Having covered the mechanisms of M2M auth in detail, let's look at how these apply in real-world SaaS scenarios.
Real-world use cases for M2M authentication
One interesting challenge with AI agents is they are often public clients (no secure storage, like a mobile or single-page app, or an LLM that can't safely keep secrets). This raises security issues – you wouldn't give an AI agent a raw client secret.
Instead, flows like device code or a user-scoped token with limited lifetime might be used.
Another aspect: AI agents may need delegated authorization. For example, a human might approve the AI to take certain actions on their behalf (like “Yes, AI assistant, you can create tasks in my Asana account”). This is often implemented with the OAuth Authorization Code flow (user approves, agent gets a token for that user’s scope).
As AI-driven assistants become part of enterprise toolchains, they need M2M authentication when calling your SaaS APIs. Let’s look at some B2B-specific scenarios:
1. AI-powered CRM assistant
- Scenario: A sales team uses an AI assistant that, each morning, fetches that day’s pipeline data, automatically drafts follow-up emails, and logs next-step tasks in their CRM.
- Auth flow: The AI agent is registered as a service client in the CRM’s auth server. It uses the Client Credentials flow to obtain a short-lived JWT scoped to
deals:read, emails:write, and tasks:create. - Benefit: No human needs to copy/paste data—every API call (e.g.,
GET /deals,POST /tasks) is authenticated via a machine token, ensuring that the assistant touches only sales-related endpoints and nothing else.
2. AI-driven support
- Scenario: Your help-desk platform plugs in a conversational AI that reads new support tickets, suggests solutions, and can escalate or close tickets automatically.
- Auth flow: Upon deployment, an admin creates a service account “Support AI agent.” The agent uses mTLS for its token exchange endpoint, then retrieves a JWT with scopes like
tickets:read, comments:write, and status:update. - Benefit: The AI can’t modify billing or user-management APIs—its token is strictly scoped to ticket operations. And because it uses mTLS to fetch tokens, the certificate assures the help-desk API that only the genuine agent app can obtain those credentials.
3. Automated financial reporting agent
- Scenario: A B2B invoicing SaaS offers an AI tool that each quarter gathers transaction data, generates customized financial reports, and uploads them to a customer’s shared drive.
- Auth flow: The AI module uses OAuth 2.1 with PKCE to get user-consented tokens for
transactions:read and reports:write. For unattended batch runs, it switches to a service-level token obtained via client credentials scoped toreports:generate. - Benefit: User consent (via OAuth code flow + PKCE) covers on-demand report creation, while scheduled batch jobs use a separate machine identity. Both flows keep credentials short-lived and narrowly scoped.
Challenges of M2M authentication
Implementing M2M authentication in B2B SaaS is not just a one-time setup – it requires ongoing management and vigilance.
- Misconfiguration risks: Even a small oversight—like not validating a JWT’s audience claim, or leaving the token endpoint unprotected—can let an attacker slip through.
- Onboarding/offboarding friction: Creating, configuring, and later revoking machine credentials often involves manual steps or ticket-based support.
- More visibility required: Comprehensive logging and monitoring of M2M authentication events are required to detect suspicious activity, audit access, and meet compliance requirements. Lack of visibility increases the risk of undetected breaches.
- Regular rotation required: Regular credential rotation and the use of short-lived tokens help minimize exposure windows, but require automation and fast token generation capabilities.
- OAuth token/certificate sprawl: Without centralized tracking, it becomes difficult to know which tokens are in use, who owns them, and what permissions they grant. Also, as the number of services grows, so does the number of certificates-each requiring secure storage, distribution, and renewal.
Best practices for M2M authentication in B2B SaaS
- Short-lived and scoped
- Mint tokens with minimal permissions (“just:read invoices” or “only:create tickets”)
- Let them expire in minutes, not months—automated refresh is painless for machines
- Stand on modern standards
- Use OAuth 2.1 everywhere and require PKCE on any code‐based flow
- Ditch legacy grants (no implicit or password grants) and enforce HTTPS by default
- Automate discovery and onboarding
- Publish a
/.well-known/openid-configurationfor clients to self-discover your endpoints - Consider dynamic client registration (especially for large partner ecosystems or AI agents)
- Publish a
- Rotate and monitor
- Rotate client secrets and signing keys regularly (and support overlapping keys during roll-over)
- Audit token issuance and usage logs regularly—catch odd patterns early
- Zero-trust by default
- Treat every service call as untrusted until it shows a valid token (or mTLS cert)
- Apply least-privilege and segment networks so a compromised credential can’t roam freely
Make the secure path the easy path—automate these steps in your CI/CD pipelines and SDKs so developers don’t have to choose between convenience and safety.
Frequently Asked Questions (FAQs)
How is M2M authentication different from user authentication?
The core concepts are similar – proving identity (authenticating) and checking permissions (authorizing) – but M2M auth is designed for software agents instead of interactive users. There’s no login form or MFA prompt; instead, machines use pre-issued credentials like API keys or certificates. Also, M2M auth typically uses tokens or keys that don’t involve human memory or biometrics. For example, a user might log in with email/password (something they know) and a one-time code (something they have), whereas a service will authenticate with a client secret or private key stored in its environment (something it has been provisioned). M2M tokens are often short-lived and scoped for security, whereas user sessions might last longer but tie into user-specific context. Another difference: user authentication often involves consent (user granting an app access via OAuth), while M2M is often pre-configured by admins.
Our product currently uses API keys for integrations. Why should we switch to OAuth or JWT-based auth?
API keys are simple and have served well for basic use cases, but they have limitations that become serious as your platform and ecosystem grow.
API keys don’t natively support expiration or scopes. If a key is leaked, an attacker could have broad, long-term access. OAuth tokens can be scoped (limiting damage) and are short-lived by default.
With a robust auth layer, you can centrally monitor and revoke access. OAuth flows let you easily disable a client or token. API keys require you to track down where that key is stored and used.
How do I implement client credentials OAuth flow in my application?
At a high level, you need two components: an authorization server (which could be a service you run or a managed service/feature of an IdP) and modifications to your resource server (API) to require and validate tokens.
How is OAuth 2.0 different from OAuth 2.1?
OAuth 2.1 isn’t a complete overhaul but rather a consolidation of OAuth 2.0's security best practices. Key differences include mandatory PKCE for all authorization code flows, removal of insecure flows (like implicit and password grants), required use of HTTPS, and clearer security defaults. It essentially makes OAuth simpler, more secure, and easier to implement correctly by default.




