Why Auth0 starts to feel constraining for AI-native B2B apps?
Auth0 didn’t become the default identity platform by chance. For years, it gave SaaS teams a way to stop worrying about authentication. OAuth was usable, SAML was manageable, and identity could be bought instead of built.
That value hasn’t gone away.
What has changed is the role identity plays inside modern B2B apps. In 2026, most B2B apps are no longer looking to solve for just login. It is defined by access, end points and how work executes across systems. Identity is part of the runtime that governs who or what can do anything at all.
Teams who start questioning Auth0 and look for auth0 alternatives today are rarely frustrated by authentication itself. They’re reacting to what identity becomes once their product ships MCPs, APIs, workflows, integrations, and AI agents.
Identity has Become Part of the Runtime
Modern B2B applications no longer have a single, user-driven entry point. Access now comes from a mix of interactive and non-interactive actors:
- Human users in dashboards and admin consoles
- APIs and SDKs used by customers
- Background workers and scheduled jobs
- AI agents executing tasks asynchronously
- MCP servers acting as tool execution endpoints
- External systems accessed on a user’s behalf
In this environment, identity determines not just who can access the system, but what can execute, under which organization, and with what scope, often long after a user has logged in.
This is where identity stops behaving like edge infrastructure and starts behaving like product infrastructure.
Auth0’s Model Still Optimizes for Users
Auth0 has evolved meaningfully. Organizations, RBAC, enterprise SSO, and extensibility via Actions give teams a lot of flexibility.
Structurally, however, Auth0 remains centered on a user-and-application model. That model works well when access is primarily interactive and human-driven. It becomes harder to reason about when execution itself becomes a first-class concern.
As AI-native features enter the product, teams often respond by composing identity behavior across multiple layers:
- Org context inferred from token claims
- Authorization logic split between Auth0 configuration and app code
- Agents modeled indirectly as applications or M2M clients
Each of these choices is reasonable in isolation. Over time, they add up. Identity semantics become emergent rather than explicit, and teams find themselves maintaining identity behavior instead of relying on it.
Where AI-native Products Begin to Push Back
The first pressure point is usually organizational identity. Fundamentally B2B apps think in companies, boundaries, and policies, not individual users. As apps mature, identity needs to reflect that reality: users belong to organizations, roles only make sense within a tenant, and the same user may belong to multiple orgs.
Auth0 supports these concepts, but they are layered on. Org context is often reconstructed downstream, which means every service needs to interpret identity correctly. This works early, but becomes brittle as systems grow.
The second pressure point is authorization. AI systems introduce variability that traditional SaaS rarely faced. Whether an action should be allowed may depend on runtime context: which tool is invoked, whether the actor is a user or an agent, what delegation occurred earlier, or which environment the execution is happening in.
In many Auth0-based systems, these decisions end up in application code because the identity layer doesn’t own the full execution context. That’s when identity starts to affect release velocity and correctness.
The third pressure point is agents. Agents don’t behave like users. They execute asynchronously, often without sessions, and need scoped, revocable access. Auth0 can issue tokens for them, but they are typically modeled indirectly. As agent usage grows, teams often maintain parallel identity paths for humans and automation. Complexity doesn’t arrive all at once. It accumulates.
A Structural Contrast: User-centric vs Execution-aware Identity
This difference isn’t about feature count. It’s about where identity logic lives as products evolve.
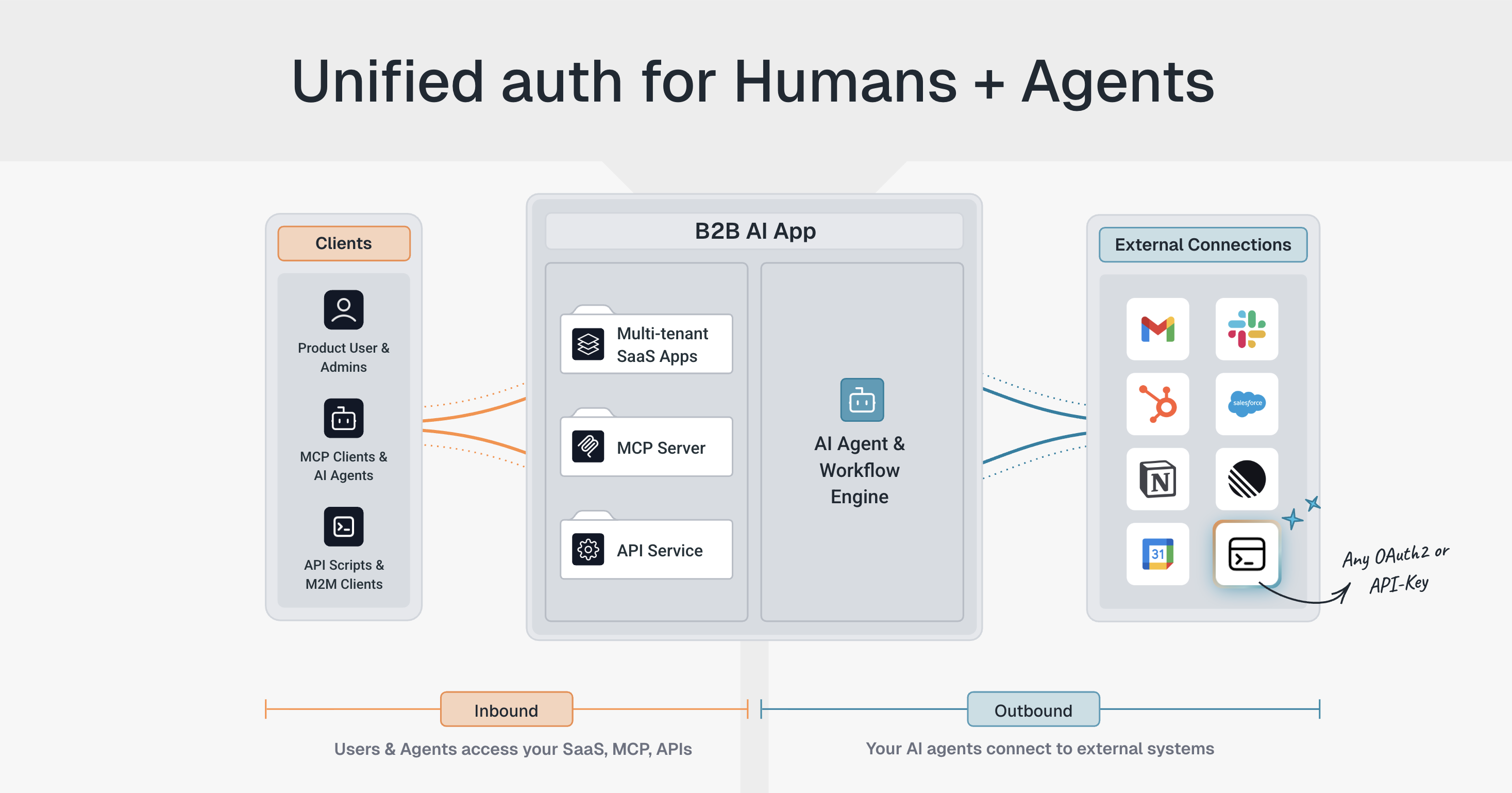
Scalekit Starts from the End State
Scalekit is built on the assumption that execution is not an edge case, but the steady state.
Instead of treating identity as configuration attached to each application, Scalekit treats identity as shared infrastructure that sits in front of the product and governs access across every surface.
A few consequences of that approach matter in practice:
- Organizations are not metadata layered onto users. They are the root identity boundary.
- Identity resolution happens upstream, during authentication and token issuance, not reconstructed inside services.
- Enterprise workflows such as SSO, SCIM, and domain discovery are part of the same system, not stitched together.
- APIs, background jobs, MCP servers, and AI agents are modeled explicitly, not retrofitted through scopes or app clients.
- Policy enforcement and auditability remain centralized and tenant-aware by default, along with simplified UI development.
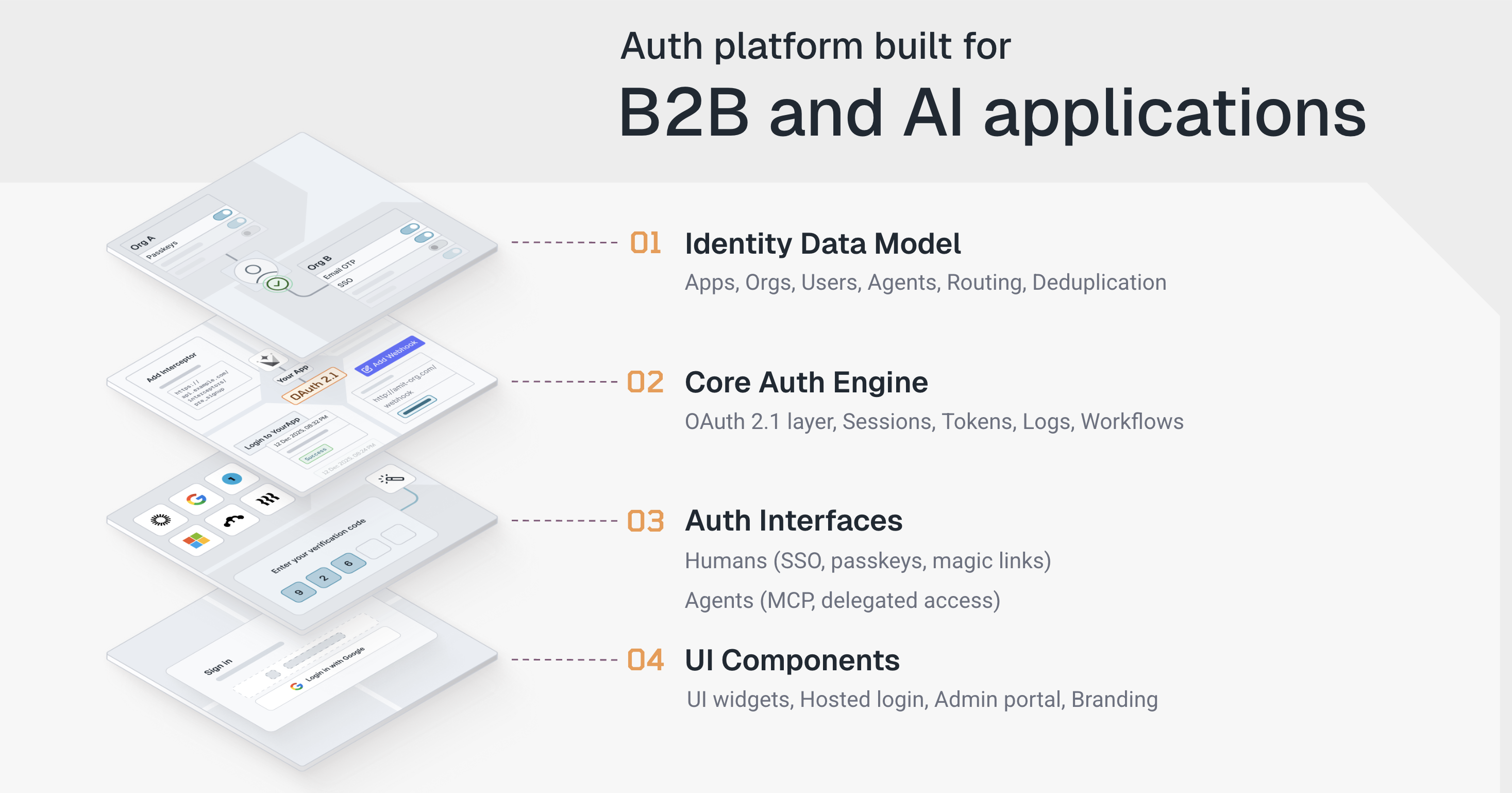
The result isn’t a heavier identity system. It’s a quieter one, because less identity logic leaks into application code over time.
Why this Matters More for AI Apps than Traditional SaaS
AI systems amplify the cost of identity ambiguity. When actions are asynchronous, delegated, and cross-system, teams need to reliably answer:
- Who initiated this action
- Under which organization
- With what scope
- Why it was allowed
User-first identity systems can support these answers, but often rely on conventions enforced across services. Scalekit moves those guarantees into the identity layer itself.
That difference becomes visible as products move from interfaces into systems of execution.
Migration does not Mean Rewriting Your Identity Stack
One of the biggest misconceptions teams have when evaluating Auth0 alternatives is that switching identity systems requires a full rip-and-replace.
That’s rarely how Scalekit is adopted.
Scalekit is designed to sit alongside existing auth, not force a migration before you’re ready. Teams typically introduce it where Auth0 starts to strain — enterprise auth components like SSO, or simplified MCP auth, Agent Auth while leaving user login untouched.
In practice, this looks like:
- Auth0 continues to handle primary user authentication
- Enterprise SSO and SCIM move to Scalekit without reconfiguring customer IdPs
- APIs, services, agents, and MCP servers authenticate against Scalekit-issued tokens
This means, teams don’t have to remodel your data to fit it. Existing Auth0 users map naturally into organizational memberships, and identity context starts flowing consistently across services without refactoring login flows.
Recommended Reading: Add enterprise SSO on top of your Auth0 setup.
Why Teams Migrate Incrementally
Most migrations stall not because of technical blockers, but because identity is deeply coupled to production systems.
Scalekit avoids that trap by letting teams:
- Migrate capability by capability (first SSO migration without customer reconfiguration, then SCIM, then agents)
- Avoid breaking existing sessions or tokens
- Introduce org-scoped identity without changing frontend auth
- Validate behavior in parallel before deprecating older flows
The result is not a dramatic migration project, but a gradual re-centering of identity around how the product actually operates.
Final Take
Auth0 remains a capable authentication platform.
But AI-native B2B apps are no longer defined by login flows. They are defined by how execution is governed across humans and machines.
When identity has to coordinate users, agents, APIs, and workflows under the same organizational boundary, a user-first model starts to strain.
Scalekit is designed for that reality.
The question in 2026 isn’t who can authenticate users. It’s which identity system stays coherent once your product becomes a system of execution, not just interaction.
FAQs
Is Auth0 unsuitable for AI-native applications?
No. Auth0 is reliable and flexible. The challenge is architectural: as execution paths multiply, more identity logic tends to move into application code.
Can Auth0 support organizations and enterprise SSO?
Yes. Auth0 supports both. In practice, org context and policy enforcement are often composed across Auth0 configuration and application logic rather than enforced centrally.
What does “execution-aware” identity mean?
It means identity models and enforces access not just for users, but for services, agents, and workflows, with tenant and delegation context preserved end to end.
Do teams need to replace Auth0 to adopt Scalekit?
No. Many teams run Auth0 for user login and introduce Scalekit alongside it for org-scoped identity, enterprise workflows, and agent access.
Why is this more relevant now than a few years ago?
Because AI dramatically increases the number of non-human actors and asynchronous execution paths. Identity patterns that were acceptable in UI-driven SaaS become operational risks at scale.




.png)
.webp)




