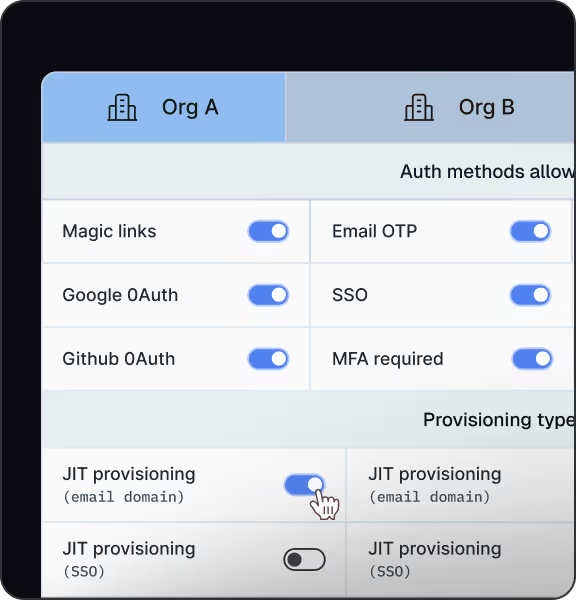
Organizations are first-class, with memberships and roles built in. Multi-tenant enforcement is the default
No native organization object. Multi-tenancy is modeled manually using pools, groups, or custom attributes
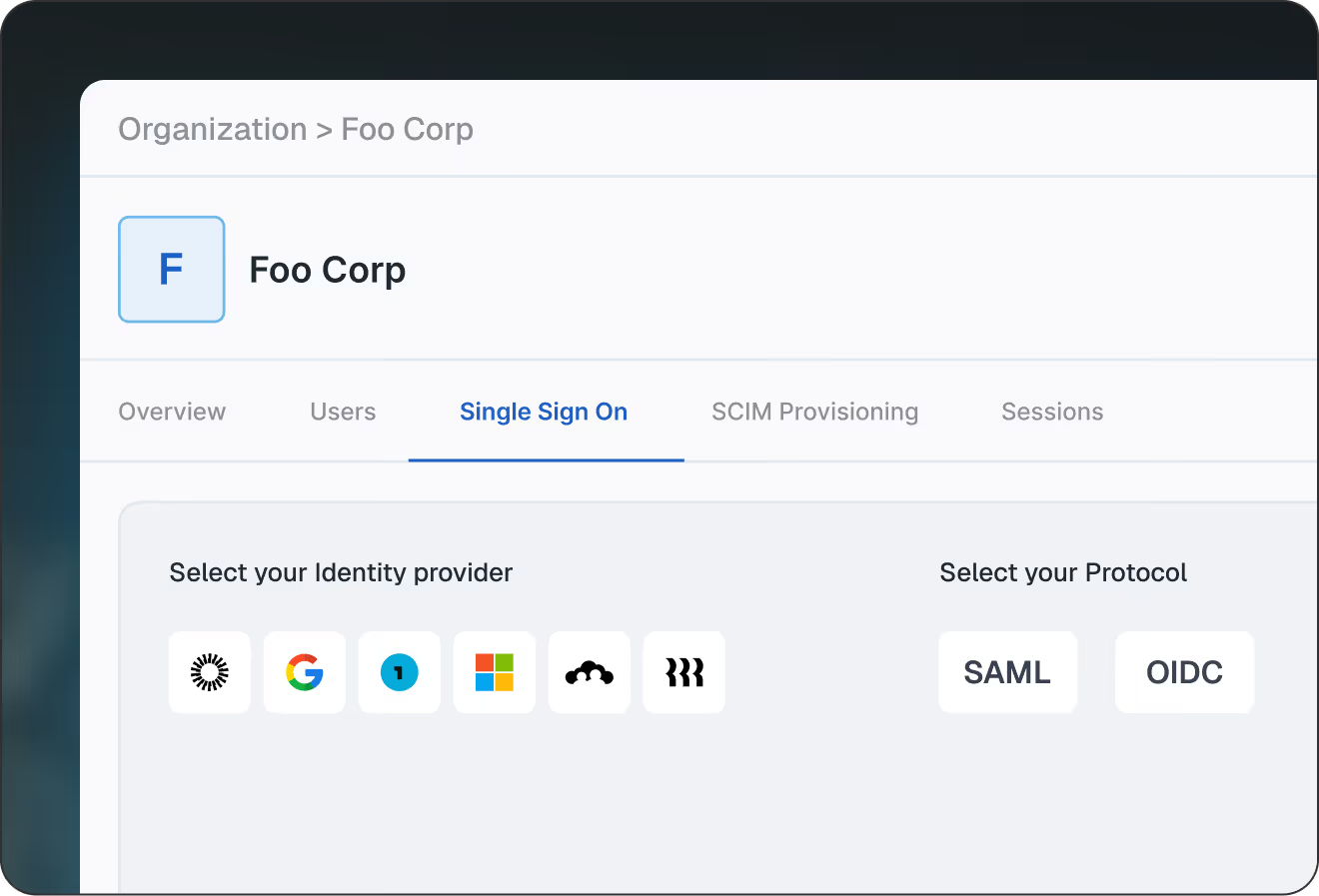
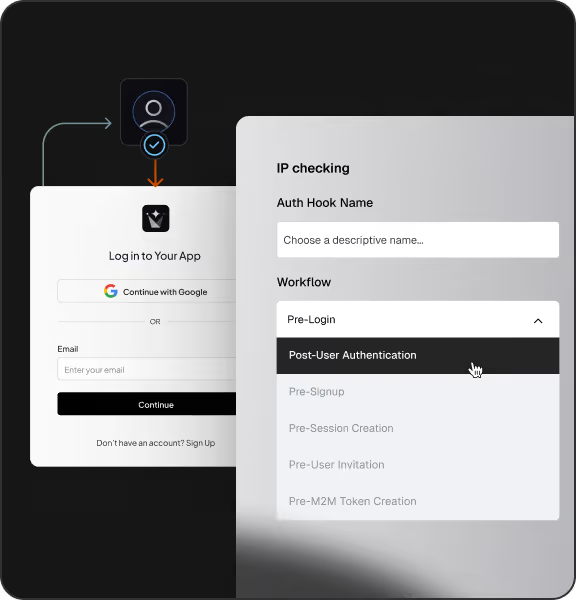
Native org-level discovery via domain, hints, or org ID. Login methods and SSO can vary per tenant
No org discovery. Users see the same login experience across the pool unless you build routing yourself
Customer-facing admin portal included, plus hosted widgets for profiles, sessions
Admin happens in the AWS Console. Customer-facing setup flows and profile management must be built separately
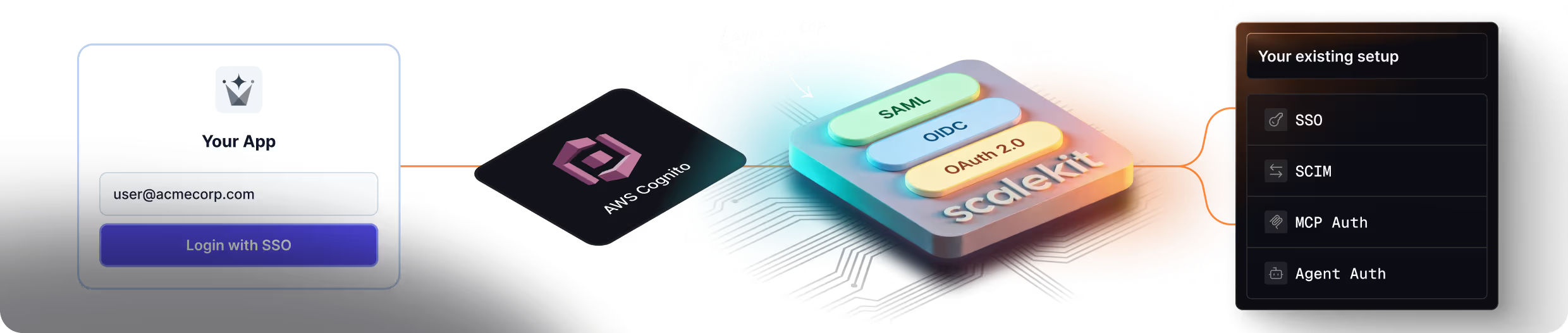
SSO is org-scoped by design, with built-in SCIM provisioning and deprovisioning workflows
SAML/OIDC supported, but configuration is pool-scoped. SCIM provisioning requires custom implementation
Tokens and sessions include org + role context automatically, simplifying tenant-aware authorization
Sessions are user-pool wide. Org and role context must be injected manually if needed
Passkeys, email OTP, and magic links supported as first-class methods, including in custom UI
Passkeys supported only through managed UI. Passwordless is limited to OTP-style flows
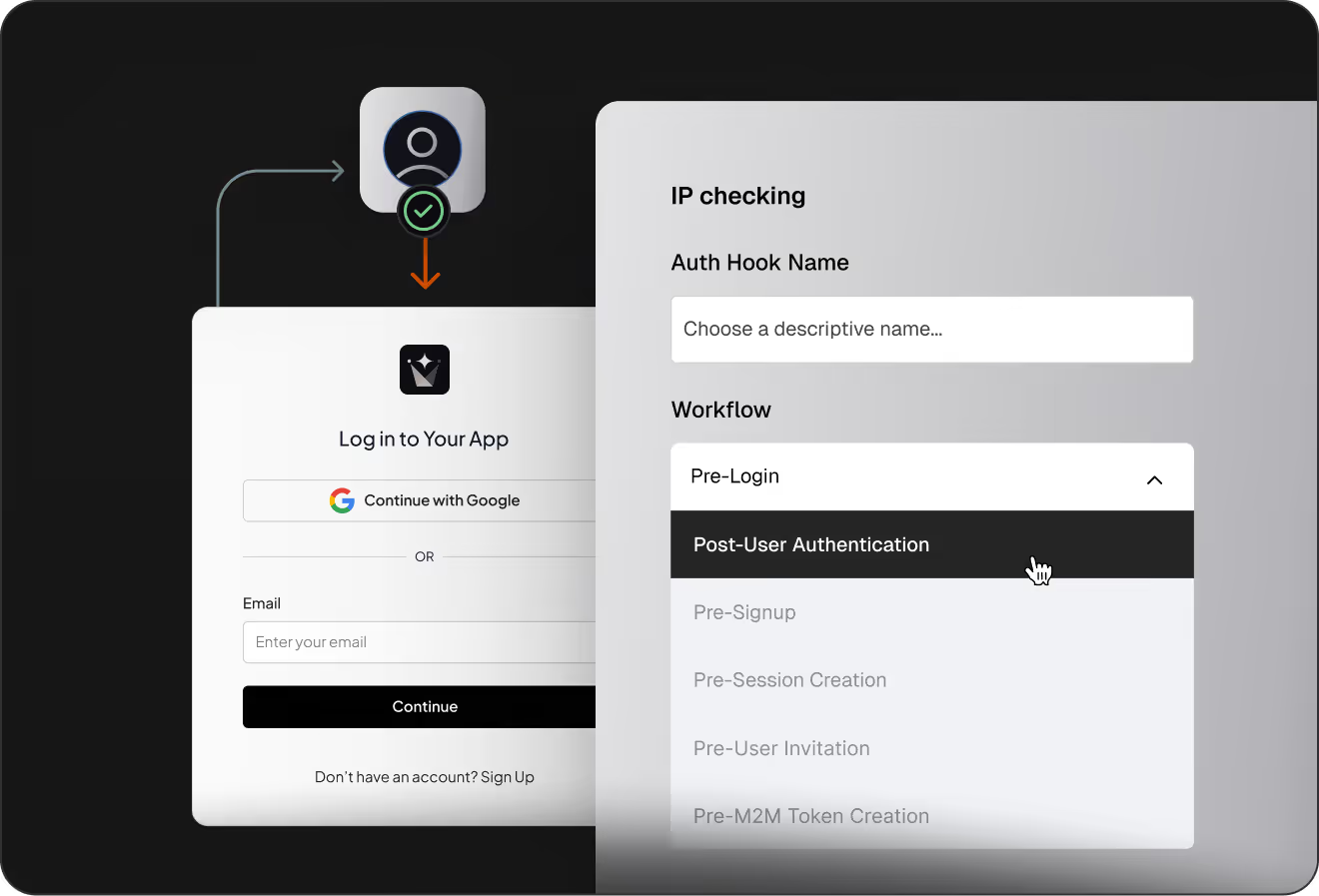
Org-aware authentication logs with user, tenant, and device context built in
Logs are infrastructure-level via CloudWatch/CloudTrail, without tenant context by default
High-level org-native SDKs, APIs, and webhooks for auth + lifecycle events out of the box
AWS-centric APIs and primitives. Webhooks and lifecycle events require additional plumbing
Designed for modern workloads: delegated agent auth and MCP-native authentication supported
Built for traditional human login. No native support for agent or MCP authentication patterns