AWS Cognito Alternatives for B2B SaaS and Agentic AI Auth

If you’re evaluating alternatives to AWS Cognito, you’re likely already past the basics.
The friction usually shows up when:
- Enterprise customers ask for SSO
- Multi-tenant access rules stop being simple
- AI agents start operating inside customer environments
But just as importantly, it shows up inside your engineering org.
What begins as a small amount of authentication glue code gradually expands into org-user mapping logic, per-customer SSO handling, and authorization checks spread across services. Over time, Cognito doesn’t just accumulate technical debt, it creates organizational debt. Platform engineers get pulled into maintaining identity plumbing, product teams slow down because access-related changes become risky, and foundational auth decisions start competing with core product work for roadmap attention.
At that point, teams realize that Cognito’s user-centric model doesn’t scale cleanly into B2B or AI-native architectures. This article looks at the paths teams take next — and how different enterprise authentication platforms approach the problem.
When do teams start looking for Cognito alternatives
Teams don’t replace Cognito because of one missing feature. They replace it because multiple pressures stack up.
1. SSO and multi-tenancy expose the lack of an org-first model
SSO and multi-tenancy usually arrive together and they surface the same underlying issue.
In Cognito:
- Users are the primary object
- Organizations are implicit or external
- SSO configuration is tightly coupled to user pools
As a result, teams end up:
- Mapping users to orgs in application tables
- Encoding tenant context into tokens and claims manually
- Maintaining per-customer SSO logic in code
SSO friction isn’t the real problem.
It’s the signal that organizations were never a first-class primitive.
2. Enterprise workflows become product requirements
As B2B usage grows, identity stops being invisible infrastructure.
Customers expect:
- Self-serve SSO setup
- Admin-level user and role management
- Predictable access behavior across environments
Security and IT teams expect:
- Clear tenant boundaries
- Auditable access decisions
- Minimal custom auth logic
Cognito was designed to authenticate users not to operate as a product-facing identity layer.
3. AI introduces non-human actors with real authority
AI-native products introduce a different class of identity problem.
Now you have:
- Agents acting on behalf of users
- Background automation with side effects
- Integrations operating inside customer orgs
These actors require:
- Org-scoped identity
- Delegated, revocable access
- Clear authorization lineage
Cognito supports machine tokens, but not agent semantics.
This is often the final trigger for re-evaluation.
How to think about Cognito alternatives
Most teams don’t just switch tools – they switch authentication models.
In practice, Cognito alternatives fall into three broad categories:
- B2B-focused authentication platforms
Designed around organizations, tenants, and enterprise workflows.
- AI-first authentication platforms
Built for agents, delegation, and non-human actors as first-class citizens.
- General-purpose authentication platforms
Improve developer experience but retain user-centric foundations.
Understanding these categories matters more than comparing feature lists.
I. B2B-focused authentication platforms
B2B-focused authentication platforms start from a different assumption: organizations, not users, are the core unit of identity.
They aim to:
- Make multi-tenancy explicit
- Reduce auth logic in application code
- Support enterprise workflows as first-class concepts
1. Scalekit
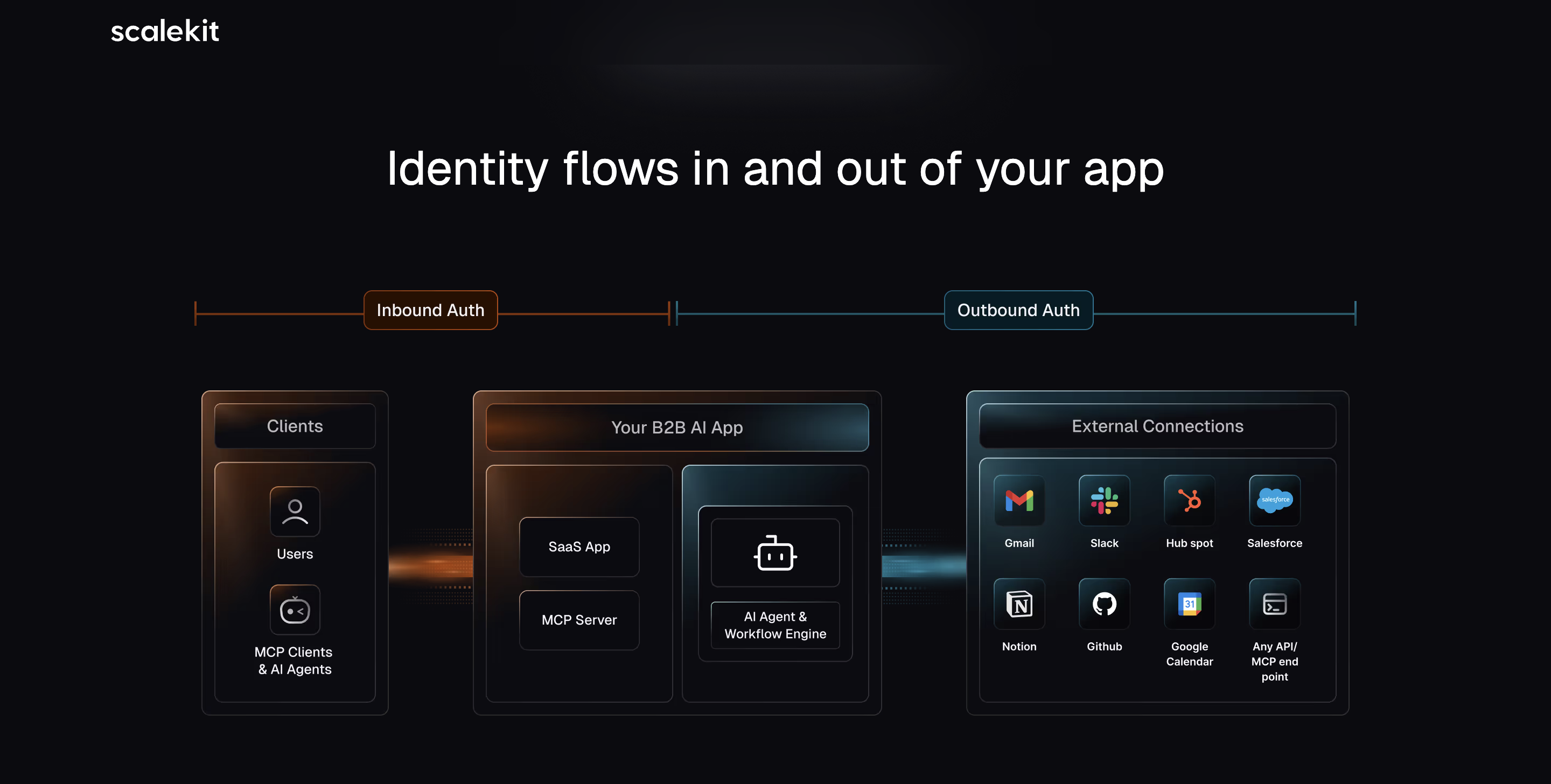
Scalekit is built on a core architectural assumption that differs sharply from Cognito and most general-purpose auth systems: B2B authentication must sit outside your application logic, not be embedded inside it.
Scalekit acts as an org-native authentication layer that intercepts identity and access decisions before they reach your product. Organizations, users, machines, and access policies are resolved as part of a shared control plane, rather than being reconstructed inside application code.
Core capabilities
Org-native identity foundations
Organizations are the root object. Users, machine identities, roles, and permissions are all scoped explicitly to an org- not inferred through claims or metadata.
Tenant-scoped authorization via interceptors
Scalekit uses interceptors that sit in front of your APIs to resolve:
- Who is making the request
- Which organization they belong to
- What scopes or roles apply
Before the request reaches business logic. Authorization is enforced once, centrally, rather than duplicated across services.
Enterprise SSO as a managed lifecycle
Scalekit's SSO is designed around real enterprise workflows:
- Admin-initiated setup
- Self-serve configuration
- Predictable org and role mapping
No per-customer SSO code paths.
Clean separation of auth infrastructure and product logic
Authentication and authorization happen upstream. Product services receive requests with resolved org context and permissions, simplifying reasoning, auditing, and evolution.
Machine and service identities tied to organizations
Non-human identities are first-class citizens, enabling integrations, background jobs, and a clean path to agent-based systems.
What this changes vs Cognito
Instead of retrofitting B2B semantics, Scalekit assumes them by default - which is what makes it viable as a long-term foundation for B2B SaaS authentication and authorization.
2. Frontegg
Frontegg is built for B2B SaaS teams that want authentication, tenant management, and admin experiences bundled together. It emphasizes account management and enterprise-facing workflows rather than low-level auth primitives.
Strengths
- Built-in B2B abstractions
- Strong admin UX
- Faster enterprise readiness
What to keep in mind
- Primarily human-centric
- Agent and machine identity often handled separately
3. WorkOS

WorkOS is designed as an enterprise-readiness layer for SaaS products. It focuses on helping teams support enterprise identity requirements such as SSO and directory integrations - without building those capabilities from scratch. WorkOS is often adopted alongside an existing authentication system rather than replacing it entirely.
Strengths
- Clean abstraction over enterprise IdPs
- Strong directory sync
- IT-friendly workflows
What to keep in mind
- Often paired with another auth system
- Limited depth in org-level authorization or agents
4. Stytch (B2B)
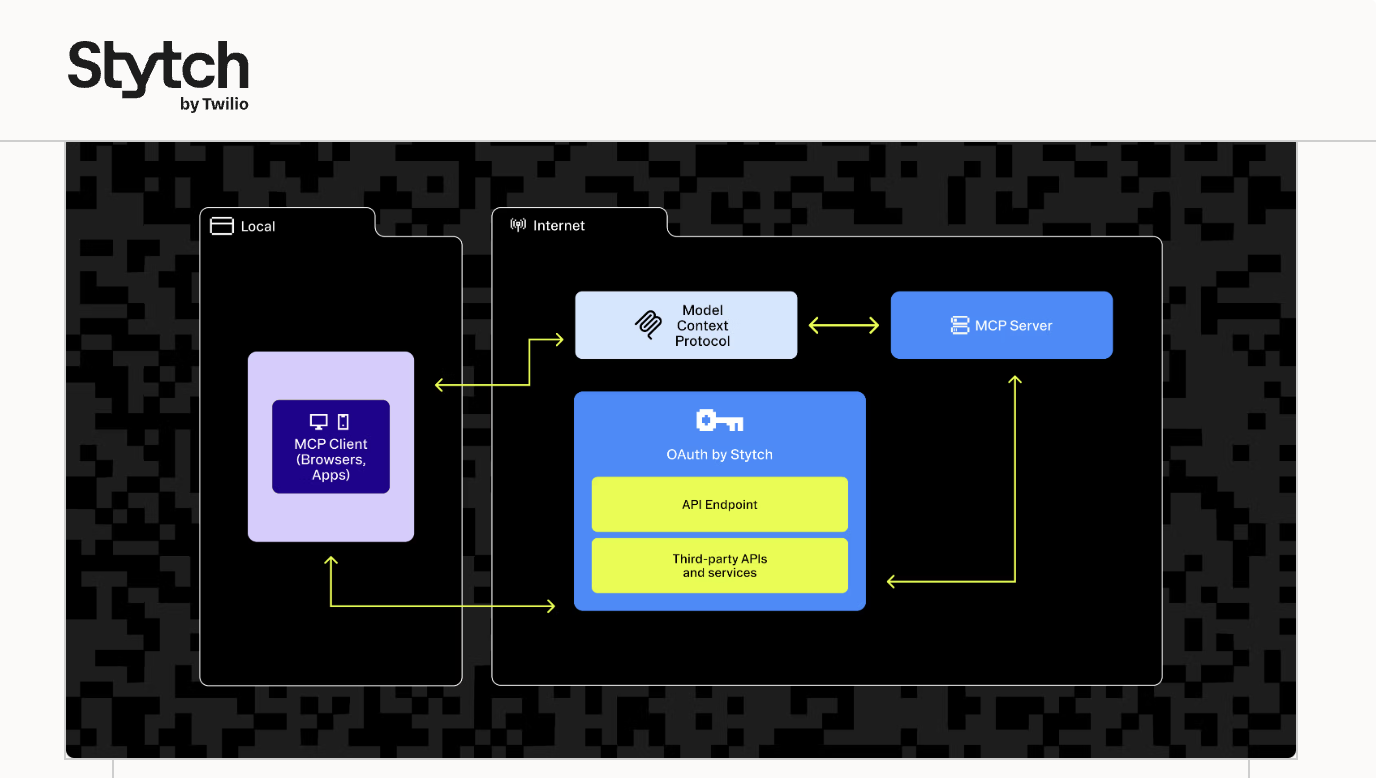
Stytch offers B2B authentication capabilities with enterprise support. Its roadmap has evolved following its acquisition by Twilio.
Strengths
- Managed B2B auth flows
- Reduced infrastructure overhead
What to keep in mind
- Long-term direction tied to Twilio’s platform strategy
- Agent and delegated access models still emerging
5. Descope

Descope approaches authentication as a set of configurable workflows rather than fixed flows. Its core strength lies in abstracting authentication logic out of application code, allowing teams to iterate on login and access flows without deep rewrites.
Strengths
- Workflow-driven auth
- Faster iteration on auth flows
What to keep in mind
- Optimized for human authentication
- Advanced org and agent semantics require careful design
II. AI-first authentication platforms
AI-first authentication systems start from a different question:
Who (or what) is acting, and on whose behalf?
They’re designed for agents, connectors, and delegated access - not just users.
1. Scalekit (AI-first capabilities)
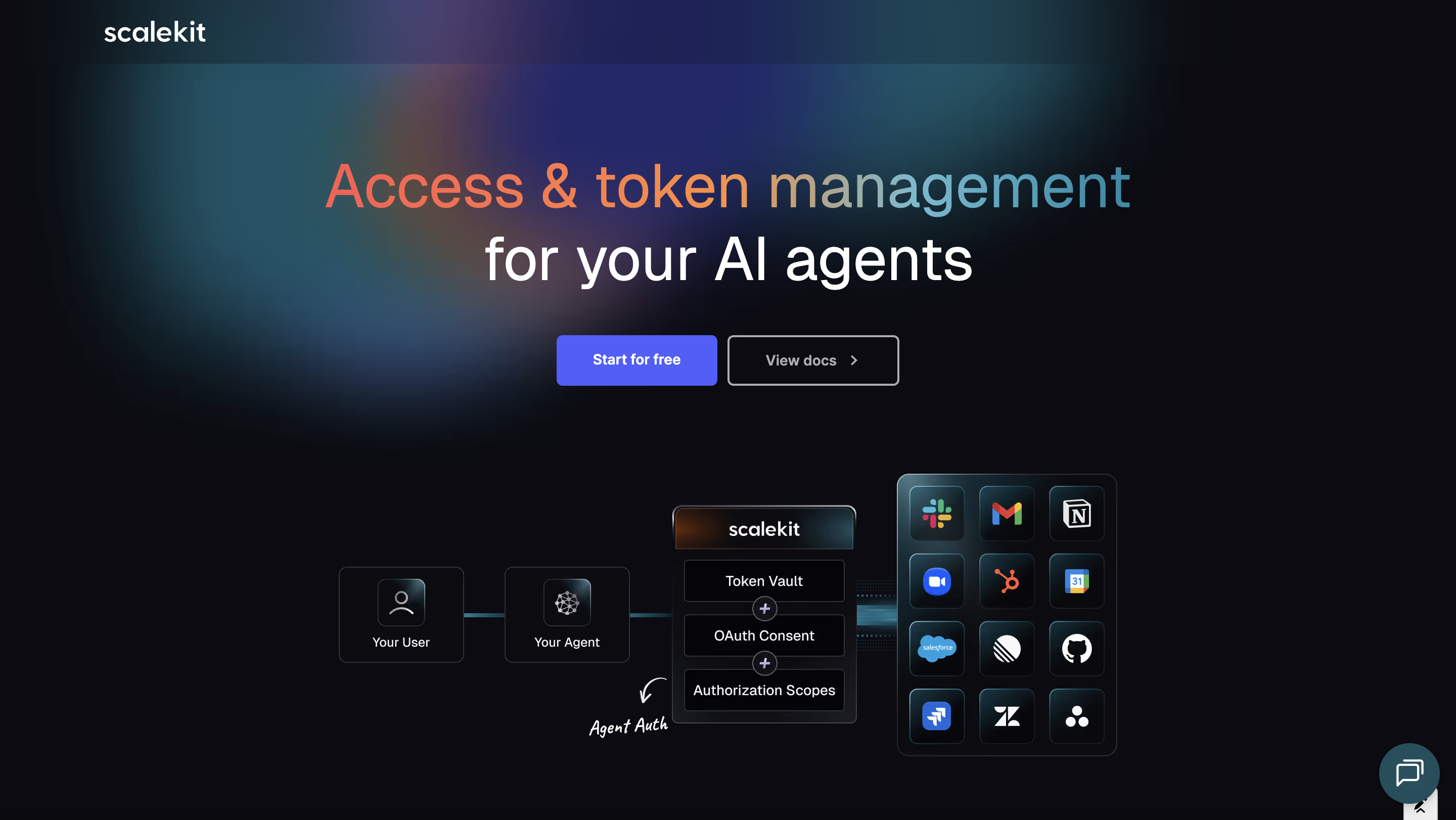
Scalekit extends its org-first model to treat agents as first-class actors, without creating a parallel identity system. Humans and agents share the same foundational primitives, which is critical as AI systems operate inside customer environments.
Core capabilities
Shared foundations for humans and agents
Agents inherit org context, access boundaries, and policy models rather than being modeled as special-case users or standalone services.
Authentication for incoming agents (MCP Auth)
Scalekit supports authentication for incoming agents accessing your B2B product, including remote MCP servers, with org context preserved end-to-end.
Recommended: Enterprise MCP: How Identity, SSO, and Scoped Auth Actually Work
Delegated access for agents using external tools
Agents can be granted scoped, user-backed access to third-party systems, enabling safe “act on behalf of” workflows.
Centralized OAuth consent and token vault
OAuth tokens and consents are managed centrally, simplifying rotation, revocation, and policy enforcement.
Auditability for agent activity
Every agent action can be traced back to:
- The user
- The organization
- The granted scope
This creates clear authorization lineage for enterprise trust and compliance.
2. Keycard.sh
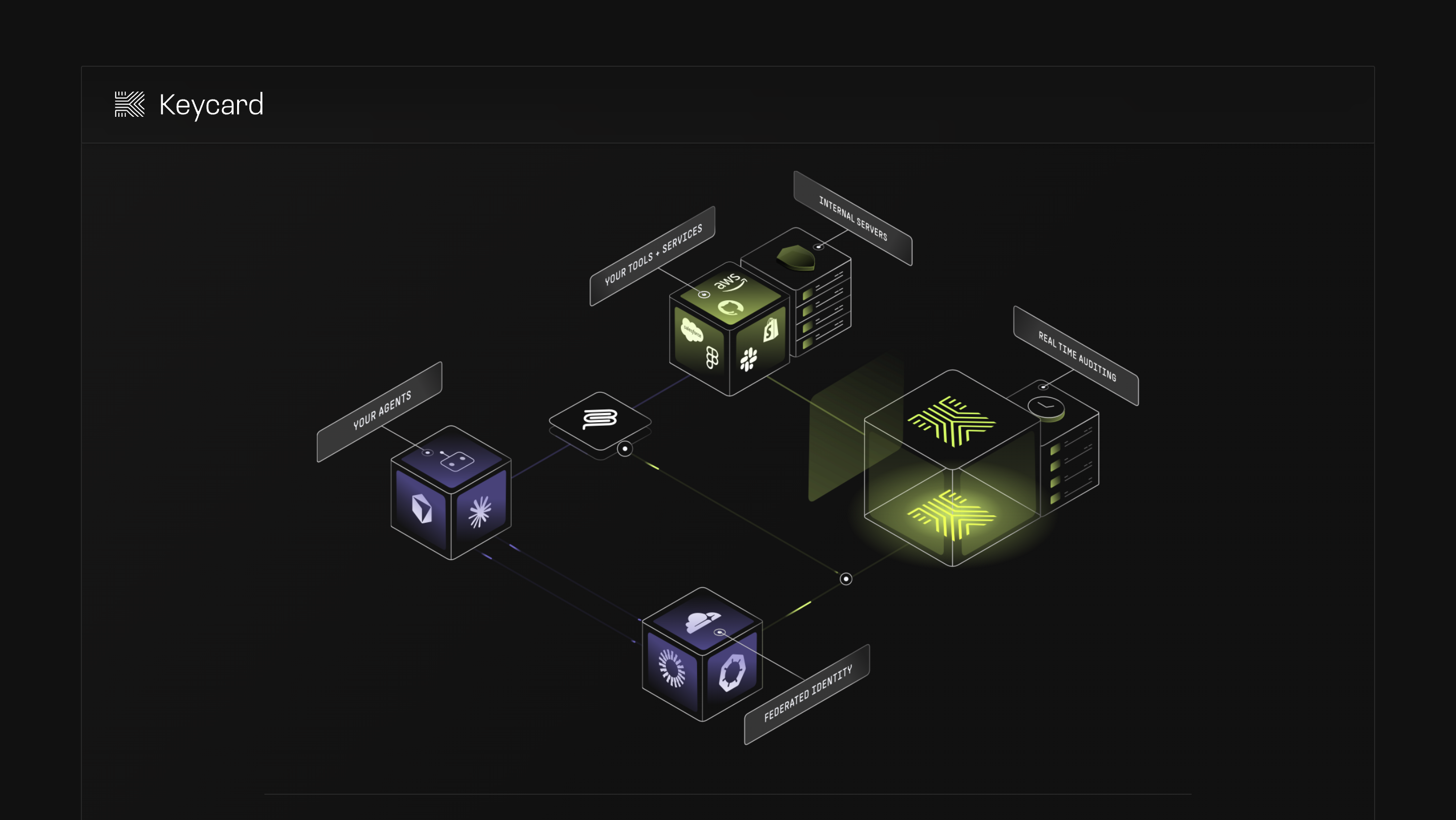
Keycard.sh is an emerging authentication system focused specifically on AI agents and connectors.
Where it shows promise
- Agent-centric design
- Clean outbound access patterns
What to keep in mind
- Very early stage
- Real-world production traction remains limited
- Best viewed as complementary to a broader B2B auth platform
3. Auth0 for Agents
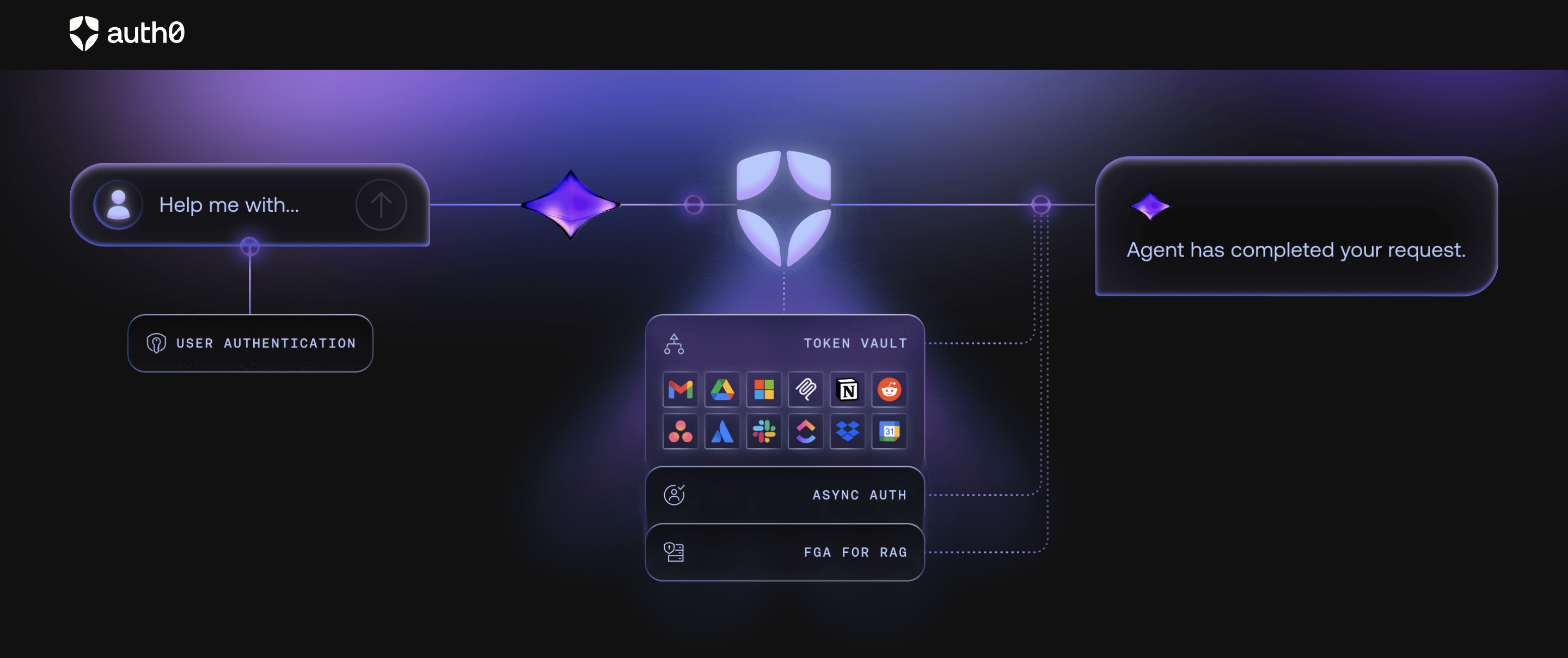
Auth0’s agent initiatives support standalone agents and RAG-based systems.
Strengths
- Familiar ecosystem
- Easier agent experimentation
What to keep in mind
- Not org-first
- Limited support for inbound agents acting within customer tenants
Recommended: Auth0 alternatives for B2B SaaS Auth
III. General-purpose authentication platforms
These platforms are often the first stop after Cognito. They offer better DX and flexibility, but they don’t fundamentally change the auth model.
At their core:
- Users remain the primary identity
- Organizations are layered abstractions
- B2B semantics live in application code
They work best when:
- B2B requirements are light
- Platform teams are comfortable owning identity design
- AI agents are peripheral, not central
1. Auth0
Auth0 is a general-purpose authentication platform optimized for flexibility and extensibility across a wide range of application types. It provides mature SDKs, a large integration ecosystem, and configurable authentication flows, making it a common choice for teams that want control over how identity is wired into their product. While it offers B2B features like Organizations and enterprise SSO, these sit on top of a foundation that is fundamentally user-centric.
Where it improves on Cognito
- Stronger extensibility and DX
- More mature SSO integrations
- Less AWS lock-in
What to keep in mind for B2B + AI
- Org modeling is not foundational
- Tenant-scoped authorization remains app-owned
- Agent auth exists, but is not designed around inbound agents acting inside customer orgs
Auth0 is often chosen when teams want control — but it doesn’t remove the need to design B2B identity semantics yourself.
2. FusionAuth
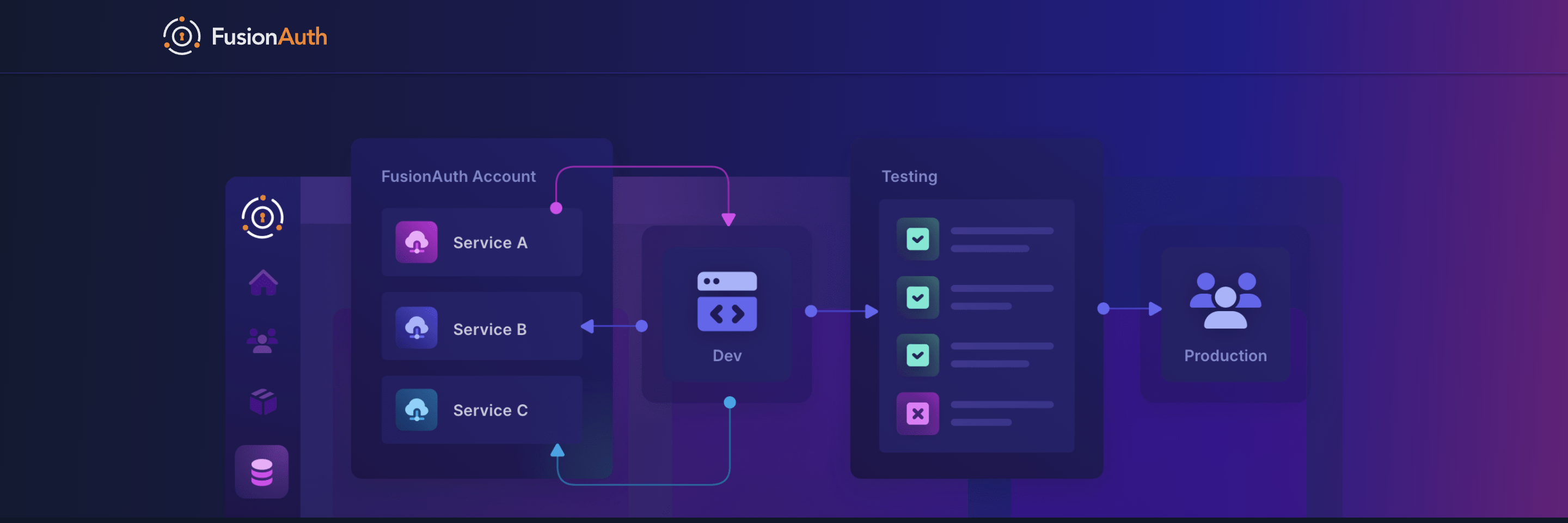
FusionAuth emphasizes flexibility and ownership, offering both managed and self-hosted deployment models. It provides strong primitives but avoids opinionated abstractions.
Where it improves on Cognito
- Deployment flexibility
- Predictable control over identity behavior
- Reduced platform lock-in
What to keep in mind
- Organizations and tenants are DIY
- Enterprise workflows require orchestration
- No native agent or delegation model
FusionAuth appeals to teams willing to own identity complexity as part of their platform.
3. Clerk
Clerk prioritizes developer experience and fast setup, especially for modern web stacks. It has gained significant popularity in the JavaScript ecosystem, with strong adoption among React, Next.js, and frontend-heavy teams due to its polished SDKs and out-of-the-box UI components. While Clerk has been expanding into B2B use cases with organization and role support, its foundation remains consumer-first, optimized for rapid user onboarding rather than deeply org-native identity models.
Where it improves on Cognito
- Faster integration
- Cleaner developer workflows
- Better defaults for modern apps
What to keep in mind
- B2B features are additive, not foundational
- Limited enterprise admin depth
- Not designed for agent or delegated access models
4. Firebase Auth / Supabase Auth
These are frequently chosen because of their proximity to application data and rapid iteration loops.
Where they improve on Cognito
- Lower setup friction
- Strong local development experience
What to keep in mind
- Strongly user-centric
- Limited org and enterprise abstractions
- Similar outgrowing curve as Cognito for B2B SaaS
Closing thoughts
Teams don’t outgrow Cognito because of missing features.
They outgrow it because their product outgrows a user-centric identity model.
Choosing the right alternative is about selecting an authentication foundation that aligns with:
- B2B scale
- Enterprise expectations
- And increasingly, AI-native workflows
That decision compounds, for better or worse.
Recommended: Launch enterprise SSO, SCIM without dev overhead
FAQs
1. Is AWS Cognito suitable as a long-term identity foundation for B2B SaaS products?
AWS Cognito can work as an initial identity layer for B2B SaaS products, but it rarely holds up as a long-term foundation once enterprise requirements become core to the product. Cognito is fundamentally user-centric, meaning organizations, tenants, and account-level semantics must be inferred or reconstructed through custom tables, token claims, and application logic. As B2B complexity grows - SSO per customer, role hierarchies, environment isolation, auditability, and delegated access - the amount of glue code required expands non-linearly. This creates architectural coupling between identity and business logic, increases blast radius for access-related changes, and turns authentication into a platform responsibility rather than an invisible layer. Many teams eventually realize that Cognito is not failing at authentication; it is simply not designed to operate as an org-native identity control plane for multi-tenant SaaS.
2. Why does multi-tenancy feel hard to model correctly in AWS Cognito?
Multi-tenancy is difficult in Cognito because tenants are not a first-class primitive in the system. Cognito provides users, groups, and user pools, but it does not natively model organizations with explicit boundaries, lifecycle management, or scoped authorization. As a result, teams encode tenant context into JWT claims, maintain user-to-org mappings in application databases, and rely on conventions rather than enforced constraints to separate access. This approach works until it doesn’t, especially when users belong to multiple organizations, when services consume tokens independently, or when authorization decisions need to be consistent across microservices. The burden of correctness shifts entirely to application code, increasing the risk of subtle access bugs that are difficult to audit or reason about at scale.
3. How does enterprise SSO change the viability of AWS Cognito for B2B SaaS?
Enterprise SSO is often the inflection point where Cognito’s limitations become visible, not because SSO itself is hard, but because it exposes missing organizational semantics. In Cognito, SSO configuration is tightly coupled to user pools and authentication flows, which forces teams to implement per-customer logic for IdP configuration, role mapping, and environment-specific behavior. Over time, this results in fragmented SSO paths, brittle onboarding processes, and manual intervention for enterprise customers. More importantly, SSO turns identity into a product surface - customers expect self-serve setup, predictable role enforcement, and clean separation between organizations. Cognito can support SSO technically, but it does not provide the structural abstractions needed to operate SSO as a scalable, productized B2B capability.
4. What challenges arise when using AWS Cognito for machine identities and automation?
Cognito supports non-human access through mechanisms like client credentials and service tokens, but it does not provide a coherent model for machine identities operating within customer organizations. Engineering teams must decide how machines relate to users, how they inherit or restrict permissions, and how their actions are audited across tenants. This becomes especially problematic as background jobs, integrations, and internal services perform actions with real side effects inside customer environments. Without org-scoped machine identity and clear delegation semantics, authorization logic becomes fragmented and difficult to secure. Cognito’s primitives are flexible, but they leave critical questions: scope, lineage, revocation, and auditability - entirely to application design.
5. When do teams typically decide to replace AWS Cognito, and why?
Teams rarely replace Cognito because of a single missing feature; they replace it when identity complexity begins to compete with core product development. The tipping point usually occurs when platform engineers spend disproportionate time maintaining auth-related logic, product teams hesitate to ship access changes due to risk, and enterprise customers drive requirements like SSO, SCIM, fine-grained roles, and auditability. At that stage, Cognito is no longer just an authentication service; it has become an implicit identity framework embedded across the codebase. Replacing it is not about finding better login APIs, but about adopting an identity model that aligns with how B2B SaaS products actually operate: org-first, policy-driven, and increasingly compatible with automation and AI-driven workflows.







.png)




