Scalekit December roundup

As the year winds down, we’ve been focused on shipping improvements that make authentication workflows easier to implement and more predictable at scale. December brought major updates across both our MCP Auth module and Fullstack Auth platform, along with new infrastructure capabilities for global teams. This roundup walks through what changed, why it matters, and how you can start using it.
Enhancements to MCP auth module
This month, we shipped full support for the three dominant authentication patterns used in production MCP environments. All three are built on OAuth 2.1, with flows designed around clear trust boundaries and predictable token handling.
1. Human → MCP host → MCP server
When a user interacts with an MCP client like ChatGPT, Claude, or Windsurf, the client acts as the OAuth client and initiates the authorization flow. Users authenticate using any method enabled in your Scalekit environment (passwordless, passkeys, social login, enterprise SSO). After approving requested scopes, Scalekit issues a scoped access token that your MCP server validates before executing any tools.
This model ensures the server only runs actions on behalf of an authenticated, consented user.
2. Agent / Machine → MCP server
Autonomous agents authenticate using the OAuth Client Credentials flow. You create an M2M client in Scalekit, store the client_id and client_secret, and the agent can request access tokens programmatically.
This allows background processes, scripts, or automated agents to authenticate without user involvement while still respecting scope boundaries.
3. MCPserver → APIs or other MCPs
When your MCP server needs to make downstream calls, the correct authentication model depends on the trust boundary:
- API keys for external or legacy endpoints
- Client Credentials for service-to-service communication between MCPs or internal services
- Passing through the original user token when all services share a trusted domain and can validate Scalekit-issued tokens
This gives you predictable, standards-aligned ways to propagate identity, depending on your architecture.
MCP quickstart: Authenticated server running in minutes
To help teams adopt MCP quickly, we introduced a guided Quickstart that walks through spinning up an authenticated MCP server in under 10 minutes. The examples use FastMCP to demonstrate the full OAuth handshake end-to-end, including token validation on the server side.
If you’re experimenting with MCP or setting up your first authenticated server, this is the fastest path.
👉 MCP Quickstart guide in Scalekit
Enhancements to Full stack auth platform
Beyond MCP, we shipped a set of enhancements to improve identity consistency, auditability, and governance across multi-tenant applications.
Webhooks: Real-time workflow automations

You can now build responsive workflows triggered by user, organization, or session events. Developers no longer need to poll for state changes—Scalekit emits structured webhooks so your systems can react immediately to authentication or membership updates.
User profile sync
For applications that use multiple identity providers (enterprise SSO, social login), user attributes can drift over time. Profile Sync ensures attributes from external IdPs are kept aligned automatically, reducing mismatches and simplifying downstream data handling.
External identities
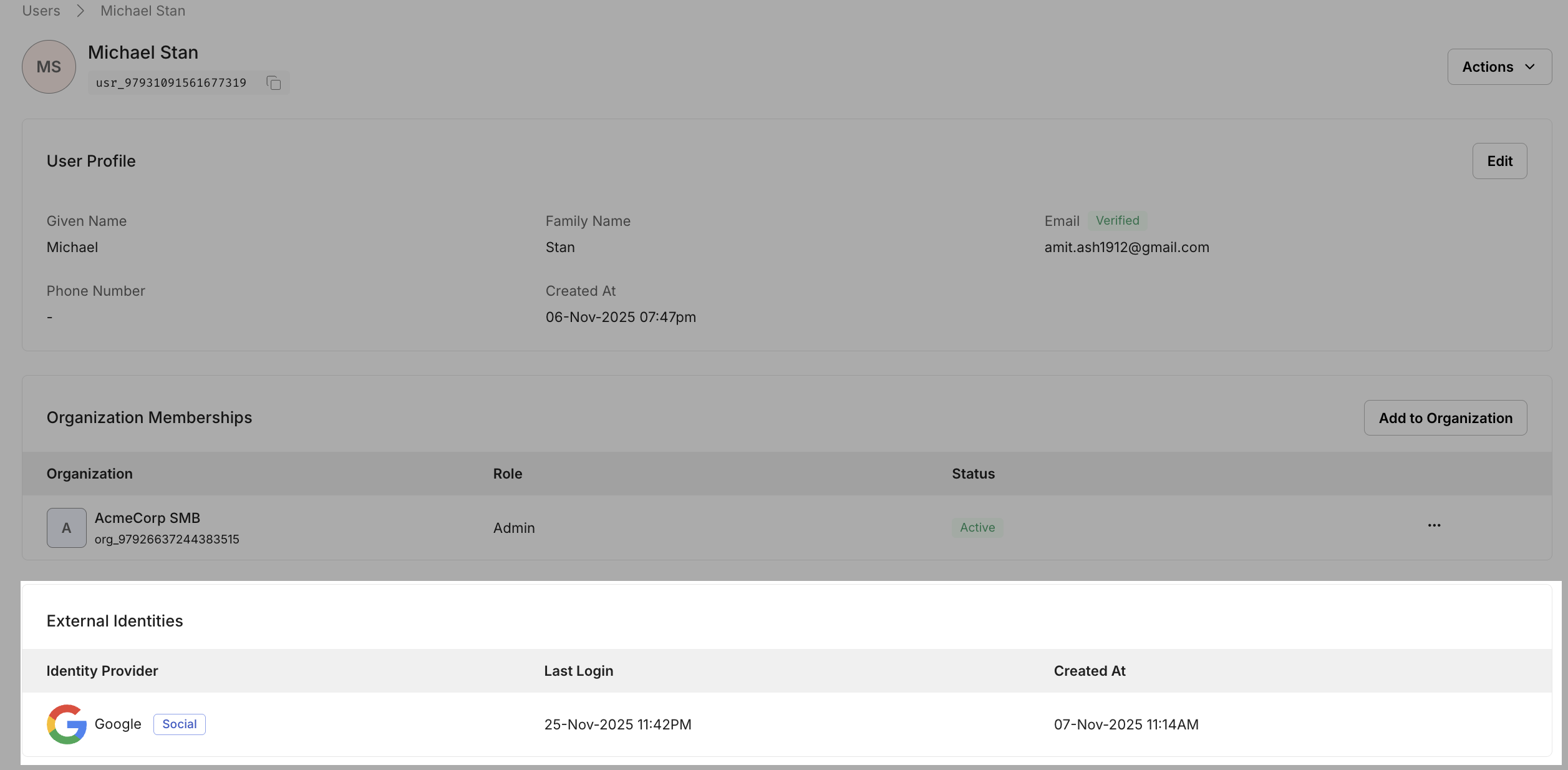
Developers can now see all external identities linked to a single user—SSO connections, social accounts, passwordless identities—within one profile. This helps diagnose login issues, avoid duplicate accounts, and maintain a clean identity graph.
Default org role
.webp)
Each organization can now define a default role for new members. This ensures users start with predictable permissions, reduces onboarding friction, and removes the need to manually assign roles for every invite.
👉 Default Org Role Configuration
Org user limits
.webp)
Seat caps can now be enforced at the organization level. This is useful when organizations map to departments, or when your plans have per-org seat limits. It gives product teams predictable control over usage and supports tiered pricing models cleanly.
Remote session management
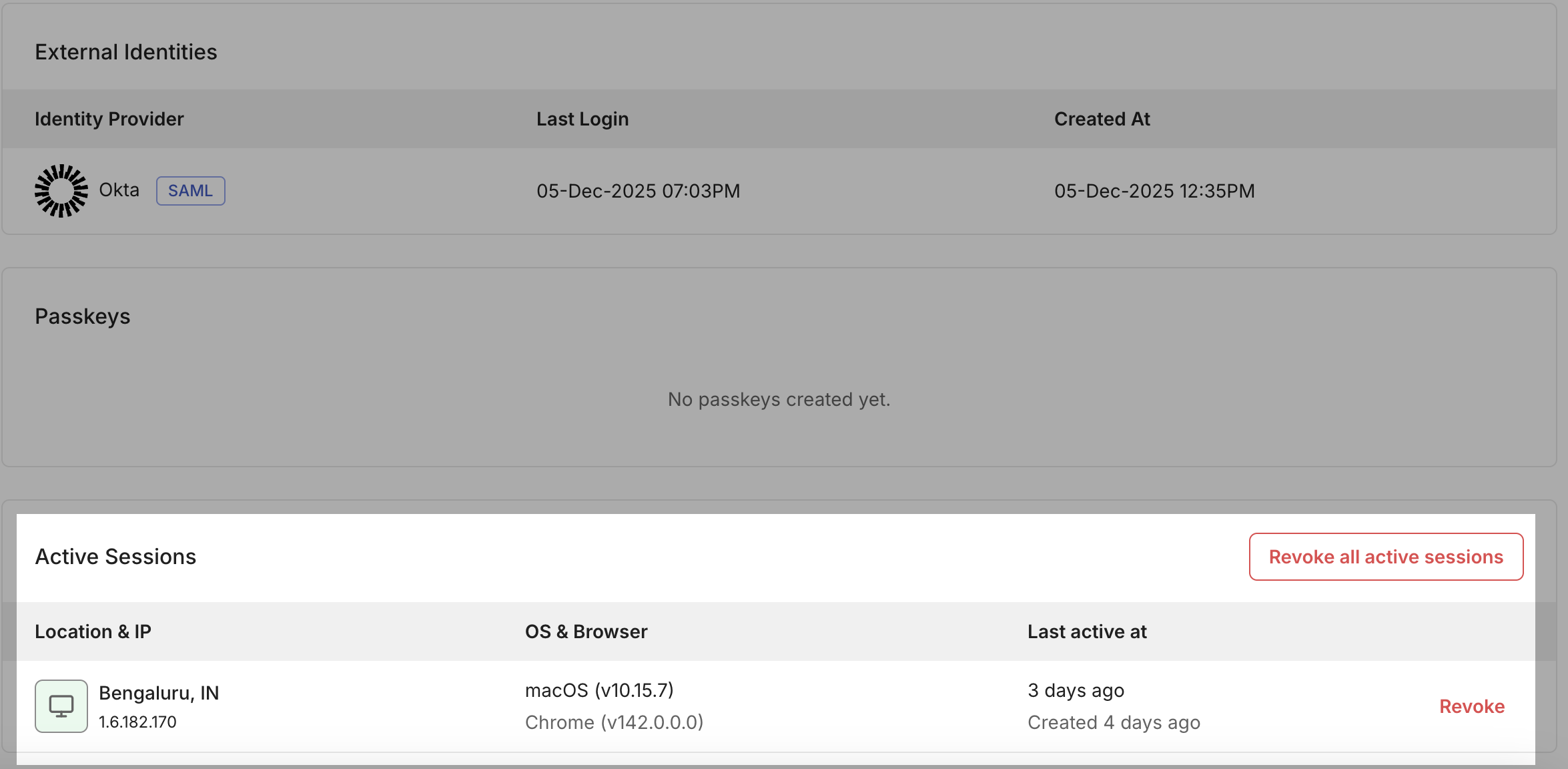
A new, embeddable session management UI lets users view and revoke active sessions directly inside your product. They can review device details, IP regions, and immediately terminate sessions—all without support involvement or custom code handling server-side session introspection.
👉 Session Management API reference
Multi-region deployment: EU data center (Frankfurt) now available
Scalekit now supports a fully isolated EU environment with data residency in Frankfurt. Authentication data for EU environments remains entirely within the region, helping teams meet GDPR and internal compliance requirements while improving latency for European users.
Teams evaluating multi-region setups or residency controls can now deploy authentication workloads where they need them.
Write to us for multi-region deployment
Wrapping up
December’s updates strengthen both dimensions of Scalekit: modular authentication for emerging agent ecosystems, and full-stack identity for SaaS platforms that need consistent governance and predictability.
If you’re using any of these features or planning to adopt them, we’d be interested in hearing your experience and what else you’d like to see in early 2026.



.webp)