Cross-app access: Identity provider directed access for agentic auth flows

TL;DR
- Cross-App Access (XAA) replaces static API keys and service accounts with short-lived, scoped tokens issued through your enterprise IdP, cutting secret sprawl and blast radius.
- Built on the Identity Assertion Authorization Grant (ID-JAG) and the OAuth 2.0 JWT Bearer flow, XAA lets one app use an IdP-issued identity assertion to obtain a target-specific access token.
- The IdP becomes the control plane for app-to-app trust, providing central policy, unified audit logs, easy revocation, and consistent enforcement of least privilege.
- Privacy, security, and compliance improve by default (scoped tokens, short lifetimes, audit-ready logs), while developers ship faster with fewer brittle secrets and a single integration pattern.
- Adoption is incremental: Start with SaaS that supports modern OAuth, wrap legacy with gateways, phase out static secrets, and prepare for broader vendor support as ID-JAG matures.
Why today’s app-to-app workflows rely on fragile credentials
Picture a modern enterprise where applications constantly call each other’s APIs to complete everyday workflows. An AI assistant might need to pull sales data from Salesforce, update a project plan in Asana, and then send a notification to Slack, all without human intervention. A finance app might push payroll updates into Workday, while a customer success tool logs usage metrics into Zendesk.
These flows keep business moving, but behind the scenes, they’re usually stitched together with brittle credentials. A background service may store a Salesforce API key that never expires. A reporting tool might rely on a service account in Workday with full admin rights. API keys are often copied into environment variables and forgotten until a breach forces their rotation.
The result is hidden risk: oversized tokens, long-lived secrets, and a lack of central visibility. When something goes wrong, neither developers nor IT admins can quickly answer, “Which app just accessed which resource, and under whose authority?”
This is where Cross-App Access (XAA) changes the model. Built on the emerging Identity Assertion Authorization Grant (ID-JAG) standard, XAA replaces ad-hoc secrets with short-lived, scoped tokens issued by the enterprise identity provider (IdP). Instead of every app negotiating its own trust with every other app, the IdP becomes the broker that mediates and governs those connections centrally.
Returning to the earlier AI assistant example: instead of storing static Salesforce and Slack credentials, the assistant would request a short-lived, scoped token from the IdP each time it needs to act. The IdP might issue a token that only allows “read contacts” in HubSpot or “post messages” in Slack, valid for just a few minutes. Once the task is complete, the token expires, leaving nothing behind to be stolen or misused.
In this article, we’ll explore what XAA is, how it strengthens app-to-app security, how IdPs enforce governance, and what this means for developers building integrations. We’ll also cover privacy, compliance, adoption challenges, and where the standard may be heading next.
What is Cross-App Access (XAA)?
Cross-App Access (XAA) is a new identity protocol that enables secure agent-to-app and app-to-app connections mediated by an enterprise identity provider (IdP). Instead of applications trusting each other directly through static API keys or unmanaged service accounts, they rely on the IdP to issue short-lived, scoped tokens that can be centrally governed, monitored, and revoked.
Imagine an AI agent that needs to pull sales data from Salesforce, update tasks in Asana, and post a summary in Slack. Traditionally, this requires storing long-lived API keys or service accounts in each system, with the agent having to handle each service’s brittle, one-off authentication mechanism. With XAA, the agent instead presents a single identity assertion to the IdP. The IdP then issues a time-bound access token scoped only for the operation (e.g., “read quarterly revenue from Salesforce”).
XAA builds on the Identity Assertion Authorization Grant (ID-JAG), an OAuth 2.0 extension currently being standardized by the IETF (draft link). The grant allows an app to present an identity assertion, a signed statement from the IdP about its identity and intent, to a target application’s authorization server. In return, it receives a token scoped only for the resource it needs.
Put simply:
- Today: Apps hold static credentials, tokens live too long, and admins lack visibility.
- With XAA: Apps exchange assertions for short-lived tokens, the IdP enforces enterprise-wide policy, and admins see exactly which app accessed which resource, and when.
For developers, this eliminates brittle secrets scattered across pipelines and configs. For IT administrators, it establishes a central control plane for managing and auditing all cross-app connections.
How Cross-App Access replaces static secrets in integrations
Cross-app interactions aren’t just about developer pipelines; they power the everyday workflows users and enterprises depend on. Think about:
- A fitness app pulling heart-rate data from a smartwatch.
- A note-taking app syncing with your calendar to attach meeting notes automatically.
- A payment app integrating with a shopping cart for checkout.
- A Slack integration updates a Trello board whenever tasks are discussed in a channel.
Today, most of these integrations rely on long-lived API keys or static OAuth tokens. These tokens often reside inside app configurations or cloud variables, are rarely rotated, and are almost always over-scoped. If leaked, they can grant far more access than intended.
Cross-App Access (XAA) changes that model. Instead of apps storing secrets, each app presents an identity assertion to the enterprise IdP. The IdP validates it and returns an Identity Assertion Authorization Grant (ID-JAG). The requesting app then exchanges the ID-JAG for a short-lived, scoped token at the target app’s authorization server.
Example: Slack updating Trello
Response:
Here, Slack receives a token valid for just 10 minutes, scoped only to update a Trello board. No static secrets reside in Slack’s configuration, and Trello can revoke access instantly if policy changes.
This pattern, repeated across CI/CD systems, productivity apps, and even consumer services, makes app-to-app trust predictable, revocable, and auditable.
Learn more: Tool calling workflows
The Cross-App Access flow, step by step
The diagram below illustrates the sequence of events:
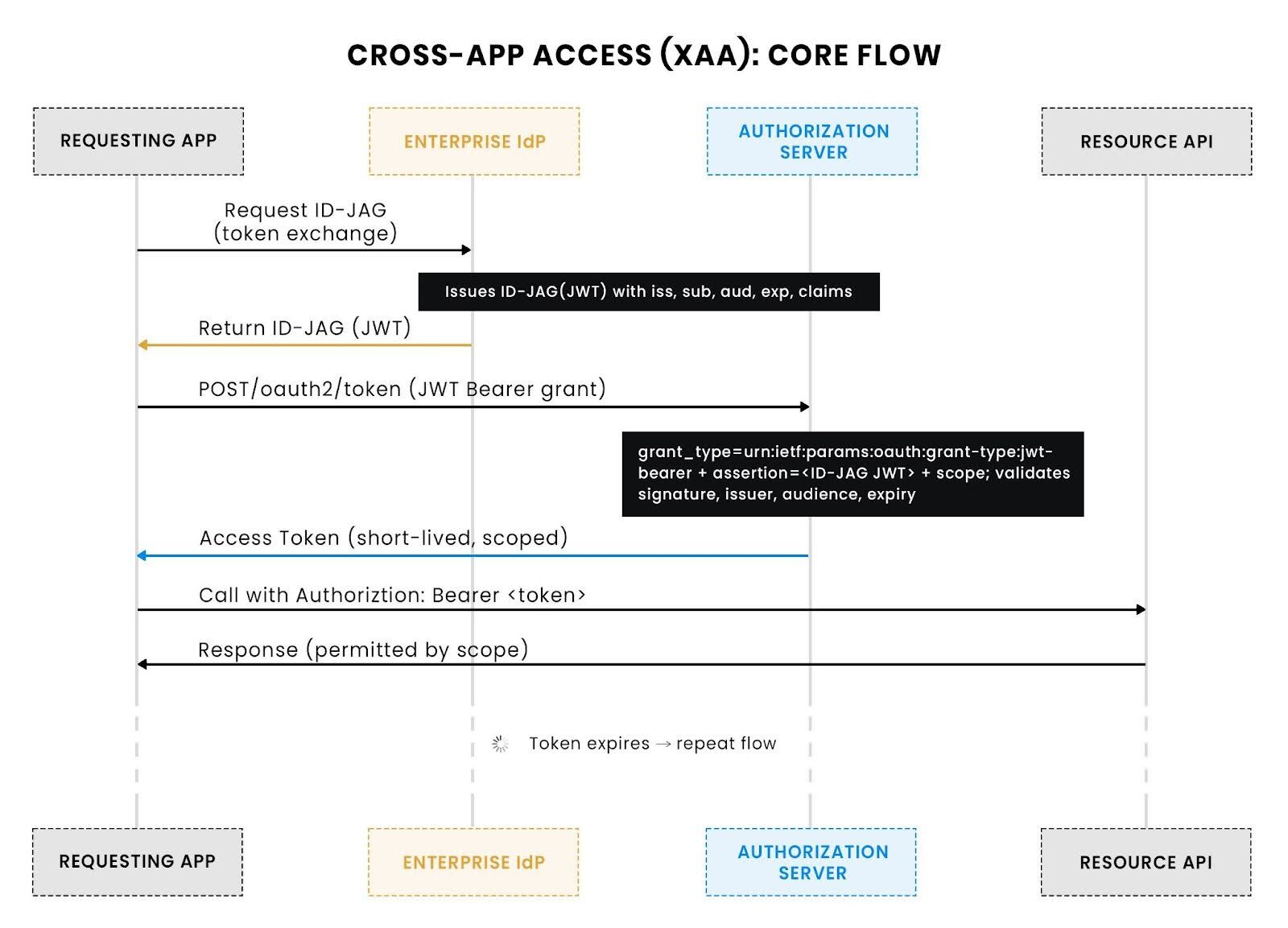
1. Request ID-JAG from the IdP: Slack (the requesting app) requests an identity assertion from the enterprise IdP. The IdP issues a signed JWT (ID-JAG) with standard claims such as iss, sub, aud, and exp.
2. Receive ID-JAG (JWT): Slack now holds a signed statement of identity and intent. This is not an access token yet.
3. Exchange ID-JAG for an access token: Slack sends the ID-JAG to Trello’s Authorization Server using the JWT Bearer grant (grant_type=urn:ietf:params:oauth:grant-type:jwt-bearer). The Authorization Server validates the JWT’s signature, issuer trust, audience, and expiry, then enforces enterprise policies and scopes.
4. Obtain a short-lived access token: On success, Trello’s Authorization Server issues a scoped access token with a short lifetime (for example, scope=board:write).
5. Call the resource API: Slack calls Trello’s API (for example, updating a board or card) with Authorization: Bearer <token>. Trello validates the token and applies resource-level checks.
6. Repeat after expiry: When the token expires, Slack repeats the cycle: obtain a new ID-JAG → exchange it → call the API. By design, this flow makes app-to-app trust predictable, revocable, and auditable.
Note: this is an illustrative XAA pattern; vendors will need to support ID-JAG for this exact exchange to work in production.
Why the enterprise identity provider is the control plane for Cross-App Access
In most enterprises, internal and third-party apps each come with their own login or service account logic. A calendar system keeps credentials for the HR app. A ticketing tool like Jira communicates with Slack using a static token. A custom reporting app uses its own API key to call Salesforce. Each connection is its own island of trust.
That model creates friction for developers and blind spots for IT. Secrets are duplicated, sessions live too long, and no single team can answer: which app accessed which resource, and under what authority?
Cross-App Access (XAA) changes that by centralizing trust in the enterprise identity provider (IdP). Instead of Slack managing a Trello secret directly, Slack presents an assertion to the IdP. The IdP validates the assertion, enforces policy, issues a short-lived token, and logs the event. Trello only needs to trust tokens from the IdP, not Slack itself.
For developers, this means a single integration point: connect your service once to the IdP, and every subsequent cross-app call follows the same pattern. For IT, the IdP becomes the control plane:
- Consistent policies: The same rules that protect user logins (MFA, conditional access, risk scoring) can apply to machine-to-machine traffic.
- Central revocation: If an integration is compromised, IT cuts it off at the IdP instead of chasing buried tokens in every app.
- Unified audit logs: Every token request and app-to-app call is recorded centrally, creating a single source of truth for compliance and incident response.
Example: In the Slack ↔ Trello flow, Slack never stores a Trello secret. It only knows how to request a token from the IdP. The IdP decides whether Slack is authorized, issues a scoped token, and logs the event. IT can later review exactly when Slack updated Trello, under which policy, without having to comb through multiple systems.
By making the IdP the control plane, XAA eliminates scattered secrets and turns app-to-app communication into something visible, governable, and revocable.
The advantages of managing app-to-app connections at the IdP
When every application maintains its own service accounts and API keys, IT teams lose visibility and developers inherit fragile integrations. Cross-App Access (XAA) shifts that responsibility to the enterprise identity provider (IdP), creating a single point of management and governance for app-to-app connections.
For IT administrators, the IdP becomes a central dashboard for machine-to-machine trust:
- Lifecycle management: When an app is retired or an environment decommissioned, its connections can be revoked in one place.
- Incident response: If a secret leaks or suspicious activity occurs, access can be cut off instantly at the IdP.
- Least privilege by default: Scoped, short-lived tokens enforce least privilege without relying on manual reviews.
- Audit visibility: Every token request and API call is logged centrally for compliance and troubleshooting.
For developers, this shift reduces friction in everyday work:
- No more manual secret rotation: Services automatically request fresh tokens from the IdP, eliminating the burden of secret sprawl.
- Consistent integration model: Whether connecting to Slack, Trello, or an internal API, the token exchange flow is always the same.
- Simpler debugging: Centralized logs mean no more guessing which webhook or token failed; the IdP shows the full story.
- Fewer brittle configs: With short-lived tokens issued on demand, integrations don’t silently break because a long-lived credential has expired.
Example: Today, Jira sends updates into Slack using a webhook secured with a static token. That token typically sits in Jira’s configuration for months (or longer) and may grant broader permissions than just posting a message. If it leaks or isn’t rotated, it becomes a hidden vulnerability.
With Cross-App Access, the same integration would shift to on-demand, IdP-governed tokens. Each time Jira needs to send a notification, it obtains a short-lived, scoped credential from the enterprise IdP and then uses it to call Slack. It could revoke that access centrally without affecting Jira or Slack configurations, and every token request would be logged for visibility and audit purposes.
By moving even webhook-style trust into the IdP, XAA turns brittle, static connections into secure, revocable, and auditable exchanges.
How Cross-App Access protects sensitive data flowing between applications
The biggest enterprise risk in app-to-app integrations is over-scoped, long-lived credentials. A reporting service might hold read/write database credentials even though it only needs read access. A monitoring tool might have a full-access API key for a cloud provider when it only needs to pull usage metrics. Once those secrets are exposed, through logs, config files, or ex-employees, they become powerful entry points for attackers.
Cross-App Access narrows that risk by enforcing least privilege and short-lived credentials at the infrastructure level:
- Scoped tokens grant access only to the required API operation, without granting any additional access
- Short lifetimes mean tokens can’t linger in configs or logs and be reused later.
- Central revocation gives IT the ability to cut off compromised connections instantly.
- Policy checks let sensitive apps enforce conditions like geo-fencing or time-of-day rules, even for machine calls.
Example: a scoped token payload
This JWT gives the reporting service just enough permission to read employee summary data, nothing more. It expires quickly and is traceable back to the IdP.
Compared to static credentials that often carry broad database or API rights, XAA creates a safer, auditable, and enforceable boundary around sensitive enterprise data flows. For developers, this reduces the mental load of secret management. For IT, it provides confidence that integrations won’t quietly expand their privileges over time.
How Cross-App Access supports compliance with industry regulations
Regulations like GDPR, HIPAA, and SOX require enterprises to prove that access to data is limited, controlled, and auditable. App-to-app connections have long been the weak spot:
- API keys don’t leave usable logs.
- Service accounts are not tied to real identities.
- Over-scoped permissions make it impossible to show least privilege.
Cross-App Access brings those connections into the same governance model as human access. Because every token comes from the IdP, compliance controls are built in rather than bolted on afterward.
How XAA aligns with compliance requirements:
- Audit-ready logs: Every token issuance and API call can be traced back through the IdP.
- Least-privilege enforcement: Scoped tokens ensure that integrations only access what they need.
- Centralized revocation: Access can be shut off immediately if an integration violates policy.
- Policy-based controls, such as geo-fencing, risk scoring, or time restrictions, can apply even to non-human traffic.
Example: compliance-friendly log entry
For auditors, this is a verifiable chain of evidence showing which service accessed which system, when, and under what scope.
For developers, it means integrations don’t need custom logging wrappers or compliance add-ons; the IdP provides compliance-grade visibility automatically.
For IT, compliance becomes a natural outcome of how access is issued, not a separate project.
Cross-App Access turns compliance from a manual burden into a byproduct of secure architecture.
Barriers to adoption: What enterprises need to prepare for with XAA
The security and governance benefits of XAA are clear, but adoption in real-world enterprises is rarely straightforward. Most organizations run a patchwork of SaaS tools, on-prem systems, and homegrown apps, each with its own authentication model. Moving them all to a single pattern takes time, and for developers, it often means living in a hybrid world for a while.
Key challenges in practice:
- Uneven vendor support: Not every SaaS provider supports the Identity Assertion Authorization Grant yet. Teams often run XAA for modern apps while keeping static tokens for legacy ones.
- Legacy infrastructure lag: Older apps may not support OAuth 2.0 at all, requiring custom adapters or API gateways to bridge the gap.
- Migration overhead: Every existing service account or API key must be cataloged and replaced with XAA-based flows. For large orgs, this is a long but necessary cleanup.
- Performance considerations: Token exchanges add latency compared to static credentials. High-throughput systems may need caching or an IdP that scales efficiently.
Hybrid integration reality
In many early deployments, a single pipeline shows both worlds:
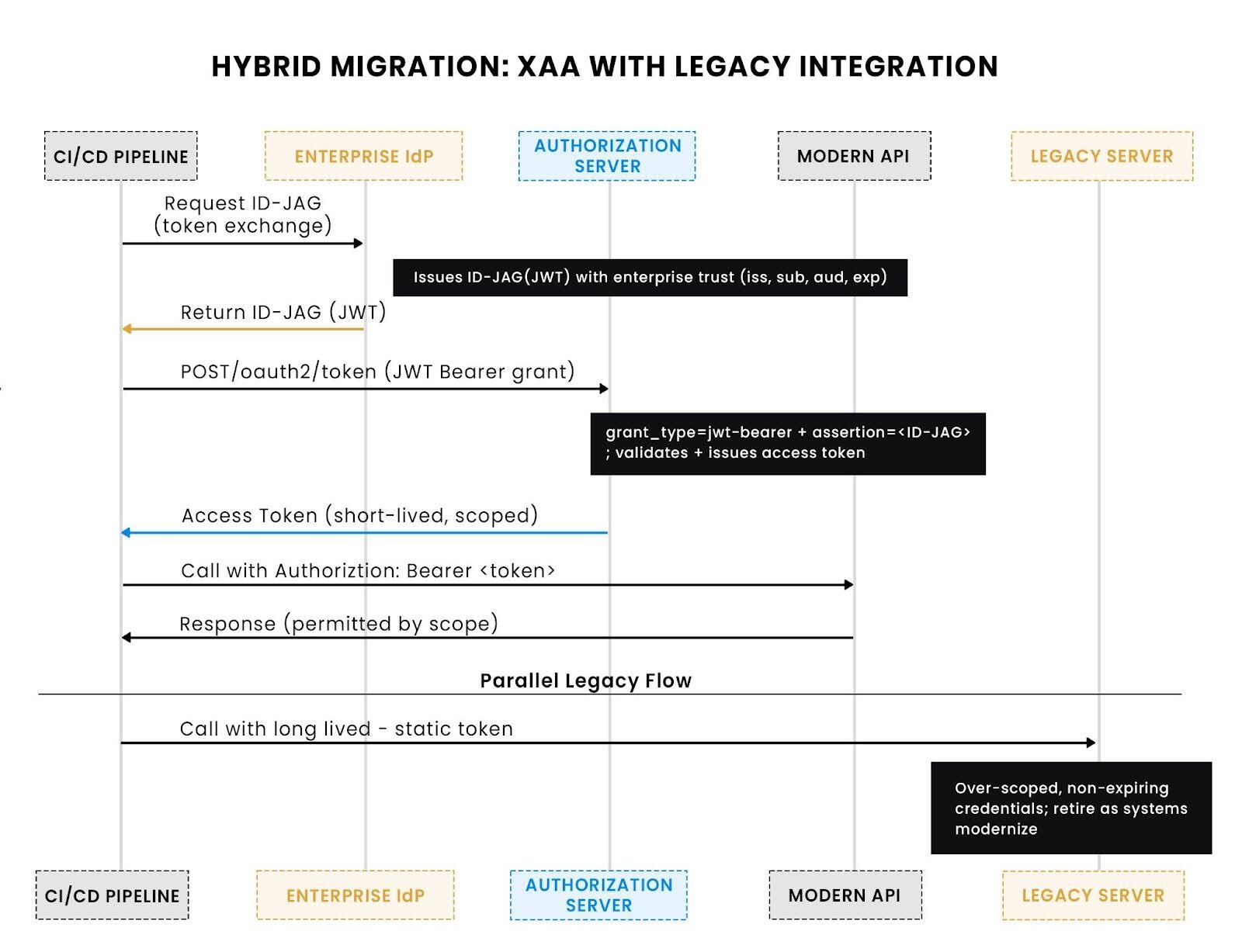
Here, Jenkins uses XAA for GitHub but still holds a static credential for the legacy build server. Developers must handle both patterns until the legacy system is modernized or wrapped with a gateway.
A migration playbook
Enterprises typically succeed with XAA adoption by taking a staged approach:
- Inventory: Identify where static tokens and service accounts are still in use.
- Prioritize SaaS apps: Start with platforms that already support OAuth 2.0 extensions (GitHub, Slack, Atlassian).
- Wrap legacy apps: Use gateways or proxies to enforce XAA-like flows until the system can be modernized.
- Phase out static secrets: Replace long-lived credentials pipeline by pipeline.
- Scale and automate: Add caching and monitoring once XAA becomes the default pattern.
Cross-App Access adoption is less about flipping a switch and more about progressively reducing secret sprawl. The hybrid state may last years, but every token replaced with an IDP-governed flow lowers enterprise risk.
The future of Cross-App Access and how it may evolve
Cross-App Access is still young. The Identity Assertion Authorization Grant (ID-JAG) was only recently adopted as a working draft by the IETF OAuth Working Group, and vendor adoption will take time. But the direction is clear: enterprises are moving toward centrally governed, short-lived, scoped tokens for app-to-app trust.
What to expect as the standard matures:
- Broader SaaS adoption: Major platforms like GitHub, Slack, and Atlassian are likely to implement ID-JAG, making XAA the default way enterprises connect apps.
- Deeper policy enforcement: Identity providers will extend beyond scopes and expiry, layering in contextual risk checks, anomaly detection, and workload binding.
- Developer tooling and SDKs: Just as OAuth 2.0 spawned libraries in every language, XAA will benefit from standardized client SDKs that hide the token exchange complexity.
- Event-driven responses: Suspicious cross-app activity may trigger automatic revocations or security workflows directly from the IdP.
- Convergence with workload identity: As cloud-native platforms (AWS IAM Roles, GCP Workload Identity Federation, Kubernetes service accounts) mature, XAA may unify those workload identities under enterprise IdPs for seamless multi-cloud trust.
For developers, this future means fewer brittle secrets and one consistent integration pattern across the enterprise stack. Instead of every tool inventing its own auth model, XAA offers a shared language: assertions, tokens, scopes, and a central policy.
Think back to the Jenkins: GitHub example we started with. Today, it’s a single build pipeline exchanging a short-lived token. Tomorrow, the same pattern could govern Kubernetes clusters talking to monitoring systems, Salesforce syncing with analytics pipelines, or internal microservices exchanging sensitive data securely.
Cross-App Access isn’t just a standards update. It’s the foundation for managing enterprise trust between applications going forward.
Conclusion: Where Cross-App Access fits into the enterprise security journey
Enterprises today rely on a dense mesh of machine-to-machine (MCP) and app-to-app (A2A) connections. Internal apps query external SaaS APIs, automation services trigger downstream workflows, and machine agents exchange data across environments. These interactions keep businesses running, but too often they are stitched together with static tokens and unmanaged service accounts, brittle credentials that create hidden risk.
Cross-App Access (XAA), built on the emerging Identity Assertion Authorization Grant (ID-JAG), replaces that fragile trust with short-lived, scoped tokens issued through the enterprise IdP.
In this article, we explored:
- What Cross-App Access is and how it works.
- How it strengthens MCP and A2A connections with stronger security.
- Why the IdP becomes the control plane for enterprise integrations.
- The practical benefits for IT admins and developers alike.
- How scoped, auditable tokens protect sensitive data and support compliance.
- The challenges of adopting XAA in hybrid environments.
- Where the standard may evolve as vendors begin to adopt it.
For developers, the takeaway is clear: start mapping which MCP/A2A integrations still rely on static keys or oversized service accounts. Identify the ones that already support OAuth extensions; those are your best candidates to pilot XAA when your IdP enables it.
For IT administrators, begin centralizing visibility. Even if not every system supports XAA today, cataloging MCP and A2A trust relationships is the first step toward enterprise-wide governance.
Where to explore further
- Read the IETF draft for ID-JAG to understand the formal standard.
- Explore workload identity systems like AWS IAM Roles, GCP Workload Identity Federation, and Kubernetes service accounts, which will increasingly converge with XAA.
- Follow enterprise IdP roadmaps (Okta, Azure AD, Ping), since they will be the first to support XAA flows.
- Investigate policy-driven models like OPA, ABAC, and RBAC, which can complement XAA for fine-grained governance.
Cross-App Access is not just another OAuth extension. It’s the foundation for secure, auditable app-to-app trust in modern enterprises. Developers and IT teams who start exploring it now will be ahead of the curve as vendors bring ID-JAG support into production.
FAQ
How is Cross-App Access (XAA) different from traditional OAuth 2.0 client credentials?
Traditional client credentials flows rely on long-lived secrets tied directly to a client app. Cross-App Access (via ID-JAG) replaces those with identity assertions issued by the enterprise IdP, exchanged for short-lived, scoped tokens. This reduces secret sprawl, enforces least privilege, and makes app-to-app trust auditable.
What role does the enterprise identity provider play in Cross-App Access?
The IdP acts as the central trust anchor. Instead of each app managing direct credentials with every other app, all trust flows through the IdP, which validates assertions, enforces policy, issues tokens, and logs activity. This provides both developers and IT administrators with a single integration model and full visibility.
Can Cross-App Access (XAA) work with legacy applications that don’t support OAuth 2.0?
Not directly. Legacy systems without OAuth 2.0 support will need adapters, API gateways, or proxies to participate in XAA. In hybrid environments, enterprises often run XAA for modern SaaS apps while still using static secrets for legacy apps until they can be modernized.
How does XAA improve compliance with regulations like GDPR or HIPAA?
Every token issued under XAA is scoped, short-lived, and logged centrally by the IdP. This produces an audit-ready trail of app-to-app access, enforces least-privilege principles, and allows for instant revocation, all of which align directly with compliance requirements for data protection and access control.
What’s the relationship between Cross-App Access and workload identities (AWS IAM Roles, GCP Workload Identity Federation, Kubernetes service accounts)?
Workload identities handle trust within a single platform or cloud provider. Cross-App Access extends that concept across multiple applications and SaaS systems by standardizing how enterprise IdPs issue and govern short-lived tokens. Over time, these models are expected to converge, enabling seamless multi-cloud and cross-app trust.
Want to enable secure, autonomous tool calls by your AI agents? Sign up for a Free account with Scalekit and get scoped tokens, credential vaulting, and audit logging built in. Need help mapping tool schemas or integrating agent workflows? Book time with our auth experts.




.png)









