OAuth Tokens Explained: for M2M Authentication

Think payment gateways syncing data with accounting platforms, CI/CD pipelines triggering deployments to cloud environments, or microservices fetching configurations from central stores. All these are examples of machine-to-machine (M2M) interactions, often involving multiple services or two backend services communicating securely within a larger system. Securing these service-to-service communications is critical, especially to ensure secure authentication and protect sensitive data during M2M exchanges, and that’s where OAuth 2.0 steps in. Not in its traditional, user-centric form, but in a streamlined, service-first variant: the Client Credentials Flow. With this method, only the authorization tokens are exchanged between backend services over an authorized communication channel, ensuring secure and verified access.
This writeup is a deep dive into how OAuth tokens power secure, scoped, and efficient authentication methods for M2M scenarios. We’ll walk through the technical foundation of OAuth in the context of backend-to-backend systems, decode how the Client Credentials flow works, break down the anatomy of access tokens (especially JWTs), and explore real-world integration examples using tools like Postman, Node.js, and cloud-native gateways. Whether you're implementing internal service auth or building out secure APIs for external B2B clients, this guide will help you architect OAuth flows with clarity and confidence.
What is OAuth and why do tokens matter in M2M scenarios?
OAuth is best described as a delegated authorization protocol. It enables one system to access another system’s protected resources, without needing to share credentials, by issuing short-lived access tokens. These tokens define what a client can access, for how long, and under what conditions. In M2M scenarios, the authentication process is streamlined to allow secure, automated connections between services, enhancing operational efficiency and simplifying integration steps.
While OAuth is commonly associated with user authorization (like allowing a third-party app to read your Google Calendar), its principles, including considerations like OAuth token lifetime, extend to non-interactive systems too. This is where M2M, machine-to-machine, authentication comes in. In M2M contexts, two backend systems interact with each other directly. Each service uses its own client credentials, such as a Client ID and Secret, for authentication. There’s no user to log in, approve, or provide consent. It’s a completely automated exchange, like a backend service pushing data to another API, or a cloud automation tool provisioning resources.
OAuth tokens, in this context, act as the security wrapper that governs what services can do, helps enforce zero-trust boundaries, and ensures that backend systems don’t overstep their roles. They’re lightweight, time-bound, and traceable, making them ideal for securing autonomous system interactions in distributed architectures.
Authorization server: The gatekeeper in OAuth
In the OAuth 2.0 ecosystem, the authorization server is the central authority that controls access to protected resources. For machine-to-machine (M2M) authentication, it acts as the gatekeeper, ensuring that only trusted machines—with valid client credentials—can obtain an access token. When a client (such as a backend service) wants to access a resource server, it presents its client ID and client secret to the authorization server.
The authorization server verifies these credentials, and if everything checks out, issues an OAuth access token. This access token is then used by the client to access protected resources on the resource server, enabling secure machine-to-machine communication. By strictly validating client credentials and issuing time-bound access tokens, the authorization server enforces access control and helps prevent unauthorized access in M2M authentication scenarios.
Client Credentials Flow: A quick primer
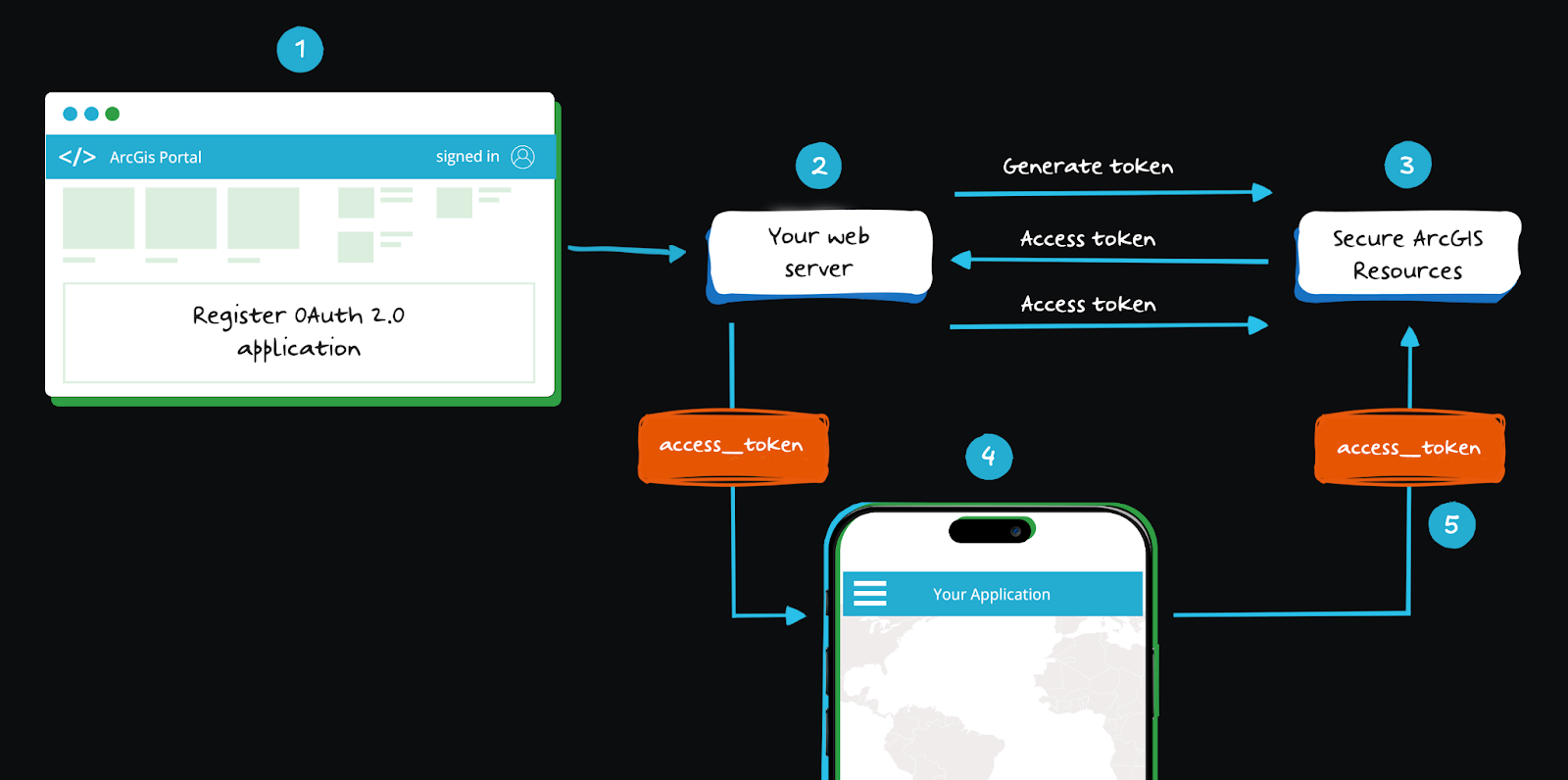
At a high level, the flow is straightforward, but what makes it powerful is how it encapsulates trust, scopes, and lifecycle control into a single access token. Unlike using an API key for authentication (Which acts as a static unique identifier and can pose security risks if leaked or left with a long lifespan), the client credentials flow provides more robust lifecycle management and secure authentication. This makes it ideal for automating secure service-to-service communication in cloud-native environments, microservice architectures, or third-party integrations in B2B apps.
At a high level, the flow is straightforward, but what makes it powerful is how it encapsulates trust, scopes, and lifecycle control into a single authorization token. This makes it ideal for automating secure service-to-service communication in cloud-native environments, microservice architectures, or third-party integrations in B2B apps.
Let’s walk through how this flow works, step by step:
- The client authenticates itself to the authorization server.
The client (e.g., a backend service or daemon) sends a request to the authorization server’s /token endpoint. It includes its client_id and client_secret, usually in the HTTP basic auth header or request body, to prove its identity. - The authorization server validates the credentials and returns an access token.
If the client’s credentials are correct and the request is authorized, the server responds with an access token (often a JWT). This token includes claims like the scope, issuer, expiration time, and other metadata that govern how the token can be used. - The client uses the token to access a protected resource.
The client now includes the token in the Authorization: Bearer <token> header when calling the target service’s API. The target service verifies the token before granting access to the requested resources.
Each token is issued for a specific scope, limiting what the client is allowed to do, which enhances security and ensures services only perform actions they're explicitly allowed to.
A real-world analogy
Imagine two services: Service A wants to call Service B's API to fetch transaction data. Service B doesn’t trust Service A by default, so it requires authentication.
- Service A first goes to a security gate (authorization server) and shows its identity badge (client_id and client_secret). In automation workflows, this is similar to when a service principal signs in to obtain an access token for unattended processes.
- If the badge checks out, the gate issues a key (access token) that’s valid for accessing only certain doors (APIs or endpoints) inside Service B
- Service A presents this key when it arrives at Service B’s door
- Service B checks if the key is real, hasn’t expired, and grants access if all is good
Token anatomy: What's inside an OAuth access token
Once a token is issued in the client credentials flow, it becomes the only credential your client needs to call a protected API. But what’s actually inside this token? And how do you interpret or trust it?
First, let’s distinguish between the common token types:
- Access token: This is what your service sends in API calls. It authorizes access to a protected resource and is the main focus in M2M use cases.
- Refresh token: Mostly used in user-based flows to get new access tokens. Refresh tokens play a key role in maintaining secure and efficient access control by allowing short-lived access tokens and enabling token renewal without requiring user re-authentication. Rarely used in M2M, services usually just re-authenticate, but in some M2M scenarios, implementing a token refresh mechanism is important to automate token renewal and ensure seamless access without manual intervention.
- ID token: Part of OpenID Connect, used to authenticate users. It has no place in the client credentials flow since there is no user involved.
Token formats: JWT vs. Opaque
- JWT (JSON Web Token): Self-contained token with all claims inside. You can decode it and verify the signature locally.
- Opaque token: A random string that means nothing unless validated against the authorization server.
M2M flows often use JWTs because they support stateless validation and performance at scale.
Learn more about how API keys compare to JWTs for M2M auth
JWT Structure
A JWT has three parts, separated by dots:
xxxxx.yyyyy.zzzzz
- Header: Specifies the algorithm and token type.
- Payload: Contains the claims.
- Signature: Ensures the token wasn't tampered with.
Sample decoded JWT payload
What the claims mean:
- iss: Issuer – who issued this token
- aud: Audience – who the token is meant for
- exp: Expiration – UNIX timestamp of when the token expires
- scope: Allowed actions for this token
- client_id: The client that requested the token
How OAuth tokens are issued in Client Credentials Flow
Before your service can get a token, you need to set up an identity provider (IdP) to trust it. This setup varies by provider, but the core steps are generally the same.
Step 1: Register a Client
In your IdP (Auth0, Okta, Keycloak, etc.), create a new application or client:
- Assign it a uniqueclient_id and client_secret
- Mark it as a machine-to-machine application
- Define scopes and assign API permissions (e.g. read:users, write:data)
Step 2: Request the Token
Use curl, Postman, or code to request a token:
Sample Response
What each field means:
- access_token: The token your service will use in API calls
- token_type: Typically “Bearer”, meaning it’s passed in the authorization header
- expires_in: Token lifespan in seconds (here, 1 hour)
Optional security configs
- Token lifetime: Most IdPs let you configure how long tokens last (expires_in).
- Secret rotation: You can periodically rotate client_secret to improve security
- Scope enforcement: Configure APIs to validate incoming tokens against required scopes. This restricts what a token can do
Validating access tokens in your API
After a token is issued and received by a client, the next critical step is validation, verifying that the token is legitimate, unaltered, and within its allowed scope. Where and how you do this can vary depending on your architecture and the type of token used.
Where should you validate?
You typically have two options:
- At the API gateway: Centralized token validation, often used in service meshes or when using tools like Kong, Istio, or AWS API Gateway
- Inside each microservice: Each service is responsible for validating incoming tokens, ensuring full control and auditability
Token introspection (for opaque tokens)
If your tokens are opaque (unreadable to the services), you’ll need to validate them using the IdP’s introspection endpoint.
This returns metadata about the token, like its validity, scopes, and expiry.
Validating JWTs
JWTs can be validated locally without making a network call on every request, once the required public key is fetched and cached.
To validate a JWT:
- Verify the signature using the appropriate method:
- RS256: Use the public key provided by your IdP (often available via a JWKS endpoint).
- HS256: Use the shared secret.
- Fetch and rotate public keys:
- If using RS256, fetch the signing keys from the IdP’s JWKS URI and cache them.
- Periodically refresh the keys to handle key rotation securely.
- Check standard claims:
- exp: Has the token expired?
- iss: Was it issued by your expected issuer?
- aud: Is it intended for your API?
Node.js Example: JWT validation with jsonwebtoken
Java Example (Spring Boot w/ Spring Security)
Spring Security with spring-boot-starter-oauth2-resource-server handles this out of the box:
And just add the dependency:
Spring will automatically decode, validate, and expose claims on the security context.
Practical example: Securing a service-to-service API with OAuth
Let’s bring it all together with a concrete scenario.
Microservice A (Payments) needs to securely call Microservice B (Billing). Both are registered clients in your identity provider. You want to ensure only authorized services can talk to each other using scoped tokens.
Step-by-step
Step 1: Register Clients in the Identity Provider
- Register Payments and Billing services in your IdP.
- For the Payments client, allow client_credentials flow.
- Assign the scope billing.write to the Payments client, allowing it to write data to Billing.
Step 2: Get Access Token (from Payments Service)
Step 3: Use Token to Call Billing API
Optional: Verify Token in Billing Service
In Billing’s backend, validate the token as shown earlier using jsonwebtoken or Spring Security, depending on your stack.
Benefits of OAuth 2.0 for M2M authentication
OAuth 2.0 brings a host of advantages to machine-to-machine (M2M) authentication, making it the go-to standard for secure backend integrations:
- Secure access: By leveraging client credentials and access tokens, OAuth 2.0 ensures that only authorized machines can access protected resources, minimizing the risk of unauthorized entry.
- Standardization: As a widely adopted protocol, OAuth 2.0 makes it easier to integrate with a variety of external services, APIs, and platforms, streamlining interoperability.
- Flexibility: With support for multiple grant types—including the client credentials grant flow—OAuth 2.0 adapts to different M2M authentication needs, from simple service-to-service calls to complex automation.
- Scalability: Designed to handle high volumes of authentication requests, OAuth 2.0 is well-suited for large-scale deployments where many machines need to access protected resources simultaneously.
These benefits make OAuth 2.0 a robust foundation for granting access and maintaining secure communication between backend services.
Best practices for M2M authentication
To maximize the security and reliability of your machine-to-machine (M2M) authentication setup, consider these best practices:
- Use secure communication protocols: Always use TLS/SSL to encrypt data exchanged between clients and the authorization server, ensuring secure communication and protecting sensitive credentials.
- Rotate client secrets regularly: Periodically update client secrets to reduce the risk of credential compromise and maintain strong access control.
- Issue short-lived access tokens: Configure your authorization server to generate short-lived OAuth access tokens, limiting the window of opportunity for misuse if a token is leaked.
- Validate tokens on every request: Ensure that your backend services validate OAuth access tokens on each API call, checking for token integrity, expiration, and proper scope.
- Monitor and log authentication events: Keep detailed logs of authentication attempts and token usage to quickly detect anomalies and respond to potential security incidents.
By following these practices, you can strengthen your M2M authentication and maintain secure, reliable access to protected resources.
Troubleshooting M2M authentication
Even with a solid OAuth 2.0 setup, machine-to-machine (M2M) authentication can encounter issues. Here are some common problems and how to address them:
- Invalid client credentials: Double-check that the client ID and client secret are correct, up-to-date, and properly configured in both your client and authorization server.
- Token expiration: Monitor the lifetime of your access tokens and ensure your client has a mechanism to request new tokens before the current ones expire, preventing authentication failures.
- Authorization server errors: Review the authorization server’s logs for error messages or exceptions that could indicate misconfiguration or operational issues.
- Network connectivity issues: Verify that your client can reliably reach the authorization server, and that there are no firewall or DNS issues blocking communication.
- Invalid token issuer: Make sure your OAuth access token is issued by a trusted authorization server. If you encounter an invalid token error, check the token’s issuer claim and validate it against your expected authorization server.
By systematically addressing these areas, you can quickly resolve most M2M authentication issues and maintain secure, uninterrupted access between your backend services.
Conclusion
Machine-to-machine (M2M) authentication, often relying on machine authentication tokens, has become a foundational requirement in modern backend ecosystems, whether it’s microservices talking internally, third-party service integrations, or automation pipelines invoking APIs. The OAuth 2.0 client credentials flow was built precisely for these scenarios: secure, no user involvement, and designed for service identity.
Now that you’ve got a solid grasp on OAuth tokens in M2M scenarios, it’s time to put it into action. Start by implementing the client credentials flow in one of your internal services—preferably where two backend systems already exchange data without user involvement. Need inspiration? Secure your CI/CD pipeline APIs or inter-microservice calls.
If you're hungry for more, check out these follow-up reads:
- Guide to Understanding JSON Web Tokens (JWT) for Developers – This guide will walk you through everything you need to know about JWT authentication, from key concepts to best practices, helping you implement it effectively in your applications.
- API Authentication in B2B SaaS: Methods and Best Practices – Explore various methods and best practices for securing API authentication in B2B SaaS applications.
FAQs
1. How do OAuth tokens work?
OAuth tokens are proof of authorization. When a client is authenticated using the correct credentials (in M2M, this is typically client_id + client_secret), the Identity Provider issues an access token. This token is then included in API requests to prove the client has permission to access a specific resource or perform a specific action.
2. How to generate an OAuth token?
To generate a token using the client credentials flow:
- Register your client in the Identity Provider.
- Make a POST request to the token endpoint with:
- grant_type=client_credentials
- Your client_id and client_secret
- The desired scope(s)
- You’ll receive a JSON response with an access token.
Example with curl:
3. How do APIs pass in auth tokens?
The access token is passed in the HTTP Authorization header of each request:
Authorization: Bearer eyJhbGciOi...
APIs should extract the token from this header and validate it before allowing access to protected endpoints.
4. What is token exchange in OAuth?
Token exchange is an advanced OAuth feature (RFC 8693) that allows a client to trade one token for another, usually with different scopes, audiences, or identity contexts. It’s useful in complex, chained service calls where a system needs to act on behalf of a different identity or role downstream.
For example: Service A receives a token, exchanges it for a limited-scope token, and passes that to Service B for a more restricted operation.
Building secure machine‑to‑machine (M2M) APIs? Sign up for a free Scalekit account to generate and validate OAuth 2.0 tokens via the client‑credentials flow and lock down your internal and external services . Need help architecting zero‑trust API security? Book time with our auth experts for tailored guidance.














