Beyond the password: a B2B SaaS guide to passkeys
.webp)
Every SaaS product eventually meets two types of customers.
The first is Acme Corp, a 5,000-person enterprise. They arrive with an IT department, an identity provider, and a polished onboarding checklist. When they integrate with your app, they bring single sign-on (SSO) through the likes of Okta or Entra ID. Their authentication is already in place.
The second is Data Designs, a 20-person design agency. Their admin, Sarah, is locked out again, and “reset password” is your top support request. Her developer, Dave, reuses his GitHub password because remembering one more is too much work. Both are frustrated, and your team ends up spending hours on the kind of ticket no one wants to handle.
This is the hidden tax of building for B2B. Authentication feels solved at the enterprise end—SSO, SAML, SCIM—but it frays everywhere else. Smaller teams, contractors, and self-serve users live in a password loop that’s slow, insecure, and expensive to maintain. Research estimates that password resets make up 30–40% of support volume in SaaS companies.
The question is no longer whether passwords are outdated; it’s how quickly we can build something better for the long tail of users who still depend on them.
What passkeys are (and what they replace)
Passkeys are an evolution of web authentication built on open standards, WebAuthn and FIDO2, that replace passwords with public–private key pairs. They offer a way to prove who you are without ever sharing a secret.
When a user signs up, their device creates two keys. The private key lives securely on the device or in a managed account like Apple ID, Google, or Windows Hello. The public key goes to your server. During login, your server sends a one-time challenge, and the device signs it using the private key. The server verifies the signature with the public key, confirming the user’s identity without exchanging any password.

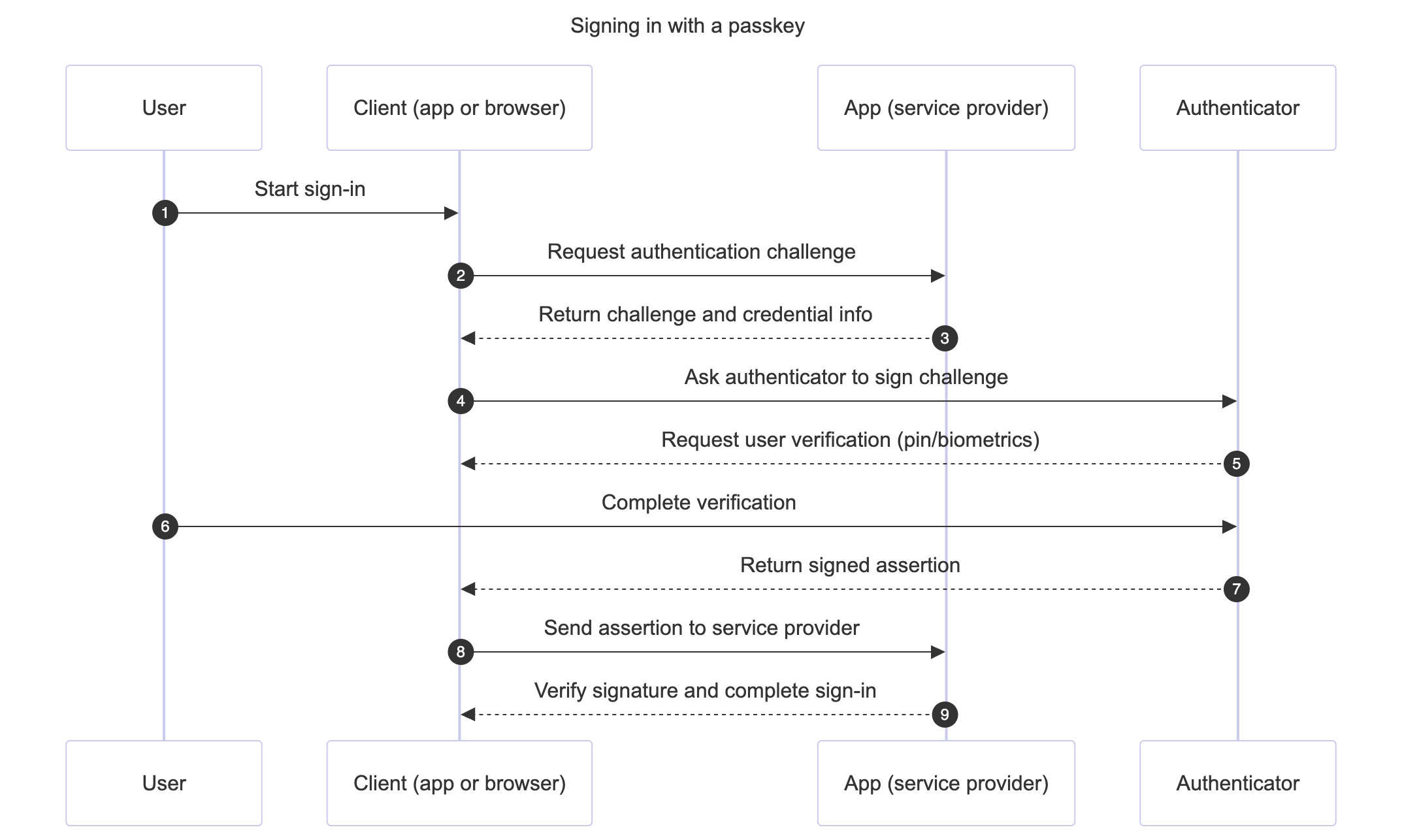
This simple exchange changes several fundamentals:
- You never store or transmit a password, so your database no longer carries credential risk
- The login can’t be phished, because a passkey only works on the domain it was created for
- Users sign in using the hardware they already trust—a fingerprint sensor, Face ID, or a system prompt
For SaaS builders used to juggling password hashes, reset flows, and breach monitoring, it’s a profound simplification. The system becomes safer by design, not by adding layers of complexity.
Why passkeys matter for B2B SaaS
B2B authentication is rarely about novelty. It’s about reliability, security, and efficiency at scale. Passkeys contribute to all three.
User experience: Passwords are the most common point of friction in onboarding. Each failed login is a drop-off. Google’s internal data shows that passkey-based logins are roughly twice as fast and four times more successful than passwords. Those are not small margins—they translate directly into smoother activation and fewer abandoned sessions.
Security posture: Traditional MFA still depends on shared secrets—codes, SMS messages, recovery keys. Passkeys replace these with cryptographic validation, closing the most common phishing pathways. GitHub’s rollout of passkeys as a two-factor method led to 95% user opt-in, not because users were forced, but because the experience was simpler.
Operational efficiency: Password resets, MFA resets, and credential audits consume an outsized share of support hours. Eliminating those workflows means fewer interruptions for your team and a smaller compliance footprint. The outcome is both a tighter system and less time spent maintaining it.
Where passkeys fit in a B2B stack
Few SaaS products can (or should) go passwordless overnight. Passkeys make the most sense when applied to specific friction points where they bring immediate value.
Passwordless login for smaller teams
Most B2B products have a long tail of non-SSO users: small teams, individual freelancers, trial accounts. This group generates most password resets and account takeovers. Offering passkeys here first provides quick, visible relief. Users sign in using the biometric systems they already trust, and your support queue gets lighter overnight.
Step-up authentication for sensitive actions
For actions that matter—deleting a workspace, changing billing data, generating new API keys—platforms often ask for a password recheck. That’s where friction spikes. Replacing that prompt with a passkey challenge offers strong assurance with minimal disruption.

MFA upgrade for administrators
Many teams still use time-based one-time passwords for MFA. Those can be intercepted through phishing. Requiring a passkey as the second factor upgrades MFA to a non-phishable standard without introducing hardware keys or complicated provisioning.
Hybrid enterprise onboarding
Large organizations don’t always have their SSO configured from day one. Passkeys fill that interim gap. They let customers invite external partners or early users securely before the corporate IdP is connected, keeping projects moving without lowering the bar for security.
Privileged and compliance roles
Compliance frameworks like SOC 2 and ISO 27001 are increasingly explicit about strong authentication for privileged users. Enforcing passkey-only login for owner or super-admin roles makes those controls simpler to audit and harder to bypass.
Across these scenarios, passkeys don’t compete with SSO—they extend it. They give product teams more flexibility to design authentication flows around context rather than one-size-fits-all credentials.
The B2B reality: what passkeys don’t solve (yet)
As promising as passkeys are, they’re not a wholesale replacement for enterprise identity systems. For now, they live alongside them.
Integration across identity providers (IdPs) is still maturing. Okta, Entra ID, and Google are introducing FIDO2 support, but consistent policy control and recovery processes are still in progress. Cross-device portability, too, remains gated by ecosystem boundaries. Moving a passkey from an iPhone to a Windows laptop is easier than before but not frictionless.
Recovery is the other missing piece. Passkeys are user-managed. If someone loses both their phone and laptop, the admin can’t just “reset” their credential the way they could with a password. Recovery depends on the user regaining access to their platform account.
And finally, revocation. Enterprise SSO and SCIM provide mature hooks for access removal. Passkey revocation across multiple services is still less standardized.
In other words, passkeys reduce several categories of risk while leaving a few operational gaps open. For most B2B teams, they’re a complement to SSO—not its successor.
The tooling landscape
Teams exploring passkeys face three main paths, each with its own balance of control and effort.
Some choose to build directly on WebAuthn libraries such as SimpleWebAuthn, WebAuthn4J, or py_webauthn. This gives full control over UX, policies, and data flow but requires careful handling of attestation formats, key lifecycles, and browser compatibility.
Others prefer developer platforms that abstract the complexity and offer ready-to-use SDKs. These platforms handle the cryptographic handshake, user verification, and SSO coexistence. They’re faster to deploy, though less customizable.
A third option is front-end overlays—tools that drop into existing login forms to provide passkey support without deep backend changes. They’re lightweight but best suited to simpler use cases rather than multi-tenant B2B apps.
Whatever the route, the choice comes down to priorities: control, time-to-market, and the degree of B2B readiness needed.
Rolling out passkeys: a practical path
Introducing passkeys isn’t a switch—it’s a phased transition that benefits from clear goals and metrics.
Phase 1: Pilot
Start where impact is easiest to measure: self-serve or non-SSO users. These are usually smaller accounts with higher churn sensitivity and lower authentication complexity. Observe how many opt into passkeys and how login success rates change.
Phase 2: Step-up
Next, add passkeys for sensitive actions—billing updates, access to secrets, or role changes. This strengthens assurance where risk is highest without touching the main login path.
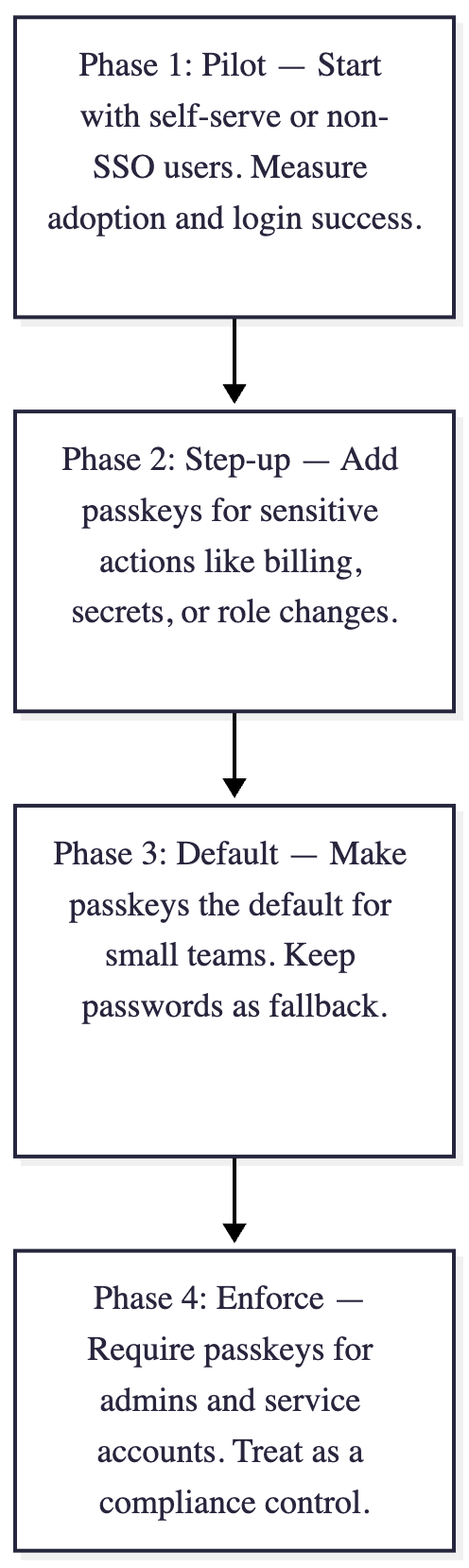
Phase 3: Default
Once adoption stabilizes, make passkeys the default authentication method for small teams and individuals. Continue supporting passwords as fallback until you’re confident the majority of users have transitioned.
Phase 4: Enforce
Finally, apply stricter rules for privileged roles—admins, owners, and service accounts. Treat passkeys as a compliance control, not just a UX feature.
Throughout these stages, measure success using clear indicators:
- Enrollment rate: what percentage of eligible users adopt passkeys.
- Login success rate: how authentication reliability improves.
- Support load: how password-reset tickets decline.
- Audit coverage: how your MFA and authentication controls map to compliance frameworks.
The goal isn’t to chase a headline metric like “passwordless,” but to build confidence step by step—until the password quietly fades from daily operations.
Architecture patterns emerging in B2B
As more companies deploy passkeys, three practical identity models have emerged.
SSO-first, passkey fallback
The most common pattern today. Enterprise users authenticate through their SAML or OIDC IdP, while individuals and small teams use passkeys. Products like Slack and Figma follow this model to keep both enterprise IT and casual users happy.
Passkey MFA within SSO
Some organizations configure their IdP to enforce a passkey challenge as part of the SSO process itself. Okta FastPass and Entra ID’s FIDO2 enforcement exemplify this hybrid setup, where passkeys raise the baseline security of enterprise logins without altering downstream apps.
Passkey-first, IdP optional
A newer generation of SaaS platforms—often product-led and self-serve—designs around passkeys as the primary factor. These apps keep SSO optional, not required, while still meeting enterprise-grade standards of authentication.
These architectures show that the passkey future isn’t about replacing federation—it’s about distributing trust closer to the user, with less dependency on passwords as shared secrets.
The road ahead
The authentication world is evolving toward a simpler shape. Passkeys are part of that shift—a movement from stored secrets to verified presence. The standards are open, the ecosystem is expanding, and support across browsers and devices has reached a point where adoption is realistic, not experimental.
The Credential Manager API is bringing cross-device portability under one umbrella. Identity providers are aligning their roadmaps to include native FIDO2 support. And as software begins to include non-human users—AI agents, automation scripts, machine-to-machine credentials—the principles behind passkeys will extend to new kinds of identity altogether.
For now, passkeys represent a pragmatic step forward for any B2B SaaS team that wants faster logins, fewer breaches, and less time spent untangling password resets.
At Scalekit, we help teams adopt this future without rebuilding their identity stack. Our platform adds passkeys and other phishing-resistant authentication methods that work across both SSO and non-SSO users—secure by design, ready for production.











