OAuth 2.0 authorization server issuer identification: RFC 9207 explained
When your B2B app integrates with multiple partner APIs, your app receives OAuth tokens after users authenticate with partner authorization servers. But how can your app reliably confirm which authorization server actually issued a given token?
OAuth 2.0 is widely used for securing APIs and managing access control. However, a known vulnerability called the "mix-up attack" threatens applications that use multiple authorization servers. RFC 9207 addresses this by explicitly identifying the authorization server that issued tokens, thereby providing multi-environment support.
Understanding the issuer identification problem
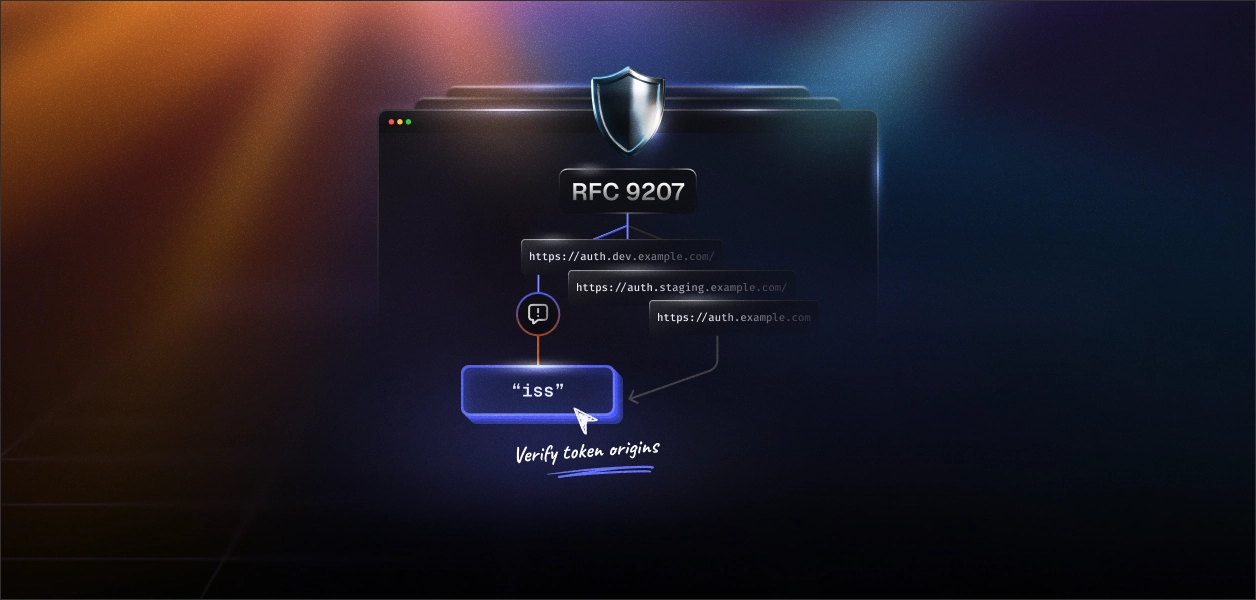
OAuth clients commonly interact with multiple authorization servers across different environments such as development, staging, and production. However, standard OAuth responses don't include explicit issuer identifiers, making it challenging for clients to verify who issued the response. This ambiguity can lead to mix-up attacks, where attackers trick clients into sending credentials to the wrong authorization server.
RFC 9207 solves this by introducing an iss (issuer) parameter in OAuth authorization responses. This parameter explicitly identifies the authorization server, allowing clients to verify responses accurately.
What is a mix-up attack?
A mix-up attack occurs when an attacker tricks your OAuth client into sending sensitive information (like authorization codes) to the attacker's authorization server instead of the legitimate one. This typically happens when your app integrates multiple authorization servers, and the client gets confused about the issuer's identity.
RFC 9207 effectively mitigates these attacks by providing explicit issuer identification.
Practical applications of RFC 9207
Here’s why issuer identification is valuable:
1. Multi-environment deployments (Dev, Staging, Prod)
When your application connects to different authorization servers for each environment, the iss parameter helps confirm you're receiving tokens from the correct environment.
Example:
Let’s look at how the iss parameter will look like for different environments.
- Dev: https://auth.dev.example.com
- Staging: https://auth.staging.example.com
- Prod: https://auth.example.com
2. Preventing mix-up attacks
Applications using multiple external identity providers (Google, Facebook, Okta, custom OAuth servers) must ensure they send authorization codes only to the intended authorization server.
3. Debugging and traceability
Explicit issuer identification simplifies debugging by clearly showing which server issued each OAuth response.
How RFC 9207 issuer identification works (Step-by-step example)
Imagine you're building a photo-sharing app (photoshare) that authenticates via multiple OAuth providers, including your own production and staging environments.
Step 1: Authorization request (Client to auth server)
Your client initiates an OAuth request to the authorization server:
Step 2: Authorization response with iss parameter
The authorization server responds, explicitly including the issuer identifier (iss):
Step 3: Client validation of iss
Your client application MUST verify that the returned iss matches the expected issuer. If the issuer mismatches, the client rejects the authorization response.
Example error response (with iss):
Even in error cases, the client verifies the iss value to ensure authenticity.
How authorization servers advertise support for iss
Authorization servers explicitly declare support for the iss parameter in their metadata:
Clients can rely on this metadata to expect and enforce issuer validation.
Security considerations and best practices
- Strict issuer validation: Clients must strictly validate issuer identifiers to prevent token confusion and potential attacks.
- Unique issuer per server: Every authorization server in your environment must have a unique issuer identifier (URL).
- HTTPS enforcement: The iss value must always use HTTPS URLs to avoid tampering and spoofing.
- Fallback considerations: Decide carefully if your client should accept authorization responses without the iss parameter based on your security policies.
For a deep-dive into the best practices specification, head to this blog.
How does RFC 9207 help AI agents?
AI agents acting as OAuth clients often interact with multiple authorization servers, especially in multi-service or multi-environment scenarios. RFC 9207 helps agents:
- Explicitly verify tokens originated from the intended authorization server.
- Prevent token mix-up scenarios when integrating multiple external services.
- Debug OAuth issues by clearly identifying the issuer of each response.
However, for high-frequency agent-to-agent communications where performance is critical, ensure you weigh the overhead of explicit validation against the benefits.
Common developer mistakes (and how to avoid them)
Mistake: Ignoring issuer validation entirely.
Correct: Always validate the iss parameter explicitly:
Mistake: Sharing the same issuer URL between different environments.
Correct: Assign distinct issuer identifiers to each authorization server environment.
Edge cases to consider
- Ensure metadata from authorization servers accurately declares support for iss.
- Clearly handle scenarios where issuer values mismatch (logging and alerting).
Conclusion: Clarity and security for multi-environment OAuth
RFC 9207 provides explicit issuer identification, protecting OAuth 2.0 clients from mix-up attacks and confusion across multiple environments. By clearly defining and verifying issuer identifiers, your OAuth integrations become safer, easier to debug, and more robust—especially important when integrating multiple OAuth providers or supporting development, staging, and production environments.
Implementing RFC 9207 helps your applications and your AI agents answer a crucial question clearly: "Can I trust that this OAuth response is from the right authorization server?"
FAQs
What does RFC 9207 solve for B2B OAuth architectures?
RFC 9207 introduces the iss parameter to OAuth authorization responses. In complex B2B environments where applications integrate with multiple identity providers or manage distinct development, staging, and production servers, this parameter explicitly identifies the issuing authorization server. By providing a clear issuer identifier, the specification allows clients to verify that the response originated from the intended source. This architectural upgrade ensures that sensitive authorization codes are never inadvertently sent to the wrong server, providing a critical layer of defense for modern distributed applications and cross service integrations.
How does a mix up attack compromise OAuth security?
A mix up attack occurs when an attacker tricks an OAuth client into sending sensitive credentials, like authorization codes, to a malicious server instead of the legitimate one. This typically happens in environments where a client supports multiple authorization servers. Without explicit issuer identification, the client cannot distinguish between a response from a trusted server and one from an attacker. By incorporating RFC 9207, the client can validate the issuer before proceeding with the token exchange. This simple verification step effectively neutralizes the threat by ensuring the client maintains context throughout the entire authentication flow.
Why is issuer identification critical for multi environment deployments?
Modern engineering teams often run parallel environments for development, staging, and production, each with its own authorization server. Without RFC 9207, a client might accidentally accept a token issued by a staging server in a production context, leading to security gaps or data corruption. Explicit issuer identification via the iss parameter ensures that every response is verified against the environment specific URL. This granularity provides better observability and prevents cross environment configuration errors, which is essential for maintaining robust security posture in sophisticated B2B platforms and microservices architectures.
How does RFC 9207 benefit AI agent authentication flows?
AI agents and MCP servers often operate as autonomous OAuth clients interacting with various external services and internal APIs. Since these agents frequently switch between multiple authorization servers, they are highly susceptible to token mix up scenarios. Implementing RFC 9207 allows AI agents to programmatically verify that an authorization response came from the intended provider before attempting any agent to agent communication. This reduces the risk of credential leakage in automated workflows. While it adds a small validation step, the security benefits for high stakes AI driven environments far outweigh the minor processing overhead involved.
How do servers communicate support for issuer identification?
Authorization servers declare support for RFC 9207 through their metadata discovery endpoints. They include a specific boolean flag named authorization response iss parameter supported set to true alongside their unique issuer URL. When a client fetches this metadata, it knows it can expect and must enforce the presence of the iss parameter in all authorization responses. For engineering managers and architects, ensuring that identity providers support this metadata discovery is a key step in future proofing auth infrastructure and automating client configuration across diverse B2B integration landscapes.
What are the best practices for validating issuer parameters?
Developers must implement strict validation logic that compares the returned iss parameter against the pre configured issuer URL for that specific request. It is vital to use HTTPS for all issuer identifiers to prevent interception or tampering. Furthermore, each environment must have a globally unique issuer URL to avoid collision. CISOs should enforce policies where clients reject any response missing the iss parameter if the server is known to support it. This defensive programming approach ensures that even if an attacker attempts a downgrade attack, the client remains protected and secure.
Can issuer identification simplify OAuth debugging and traceability?
Yes, explicit issuer identification significantly enhances system observability. When developers troubleshoot failed authentication flows in multi tenant or multi provider setups, the presence of the iss parameter in the logs provides immediate clarity on which server initiated the response. This eliminates guesswork and helps identify misconfigured redirect URIs or environment mismatches quickly. By providing a clear trail of the authorization source, RFC 9207 reduces the mean time to resolution for auth related incidents. For technical architects, this traceability is a valuable byproduct of improving the overall security architecture of the platform.
Does RFC 9207 apply to machine to machine authentication?
While RFC 9207 primarily focuses on the authorization code flow, its principles are highly relevant for machine to machine and agent to agent communications involving redirects or delegated access. As AI agents increasingly participate in complex ecosystems with multiple issuers, maintaining a strict mapping between requests and their corresponding issuers is paramount. Even in these scenarios, validating the source of an authorization grant prevents attackers from injecting tokens from lower security environments into high value service flows. Architects should view issuer identification as a foundational requirement for any B2B system that relies on dynamic or multi provider authorization.
How does issuer identification impact dynamic client registration?
In scenarios involving dynamic client registration, a client might interact with many unknown authorization servers on the fly. RFC 9207 provides a standardized way for these dynamically registered clients to verify the identity of the server they just registered with. By validating the issuer parameter in the first authorization response, the client confirms that it is indeed communicating with the legitimate server and not a proxy or an attacker. This synergy between registration and issuer identification creates a more secure and scalable onboarding process for B2B applications that need to support automated partner integrations.













