Scalekit now supports secure, standards-based auth for AI toolchains
AI agents are getting smarter, faster, and more deeply embedded into real systems. But without proper access control, they become a security risk. That’s why Scalekit now offers drop-in authorization for MCP (Model Context Protocol) servers using OAuth 2.1.
If you're building or exposing an MCP server, Scalekit lets you add secure, scoped access control in minutes—no custom auth server, no spec deep-dives.
Why it matters
MCP defines how AI models connect to tools, APIs, and data. As those tools become more powerful, proper authorization is critical. Scalekit handles that for you with a production-ready OAuth 2.1 flow tailored for MCP:
- Enforces PKCE and strict redirect validation
- Issues short-lived, scoped tokens
- Supports both human and M2M flows
- Works with any host implementing the MCP standard
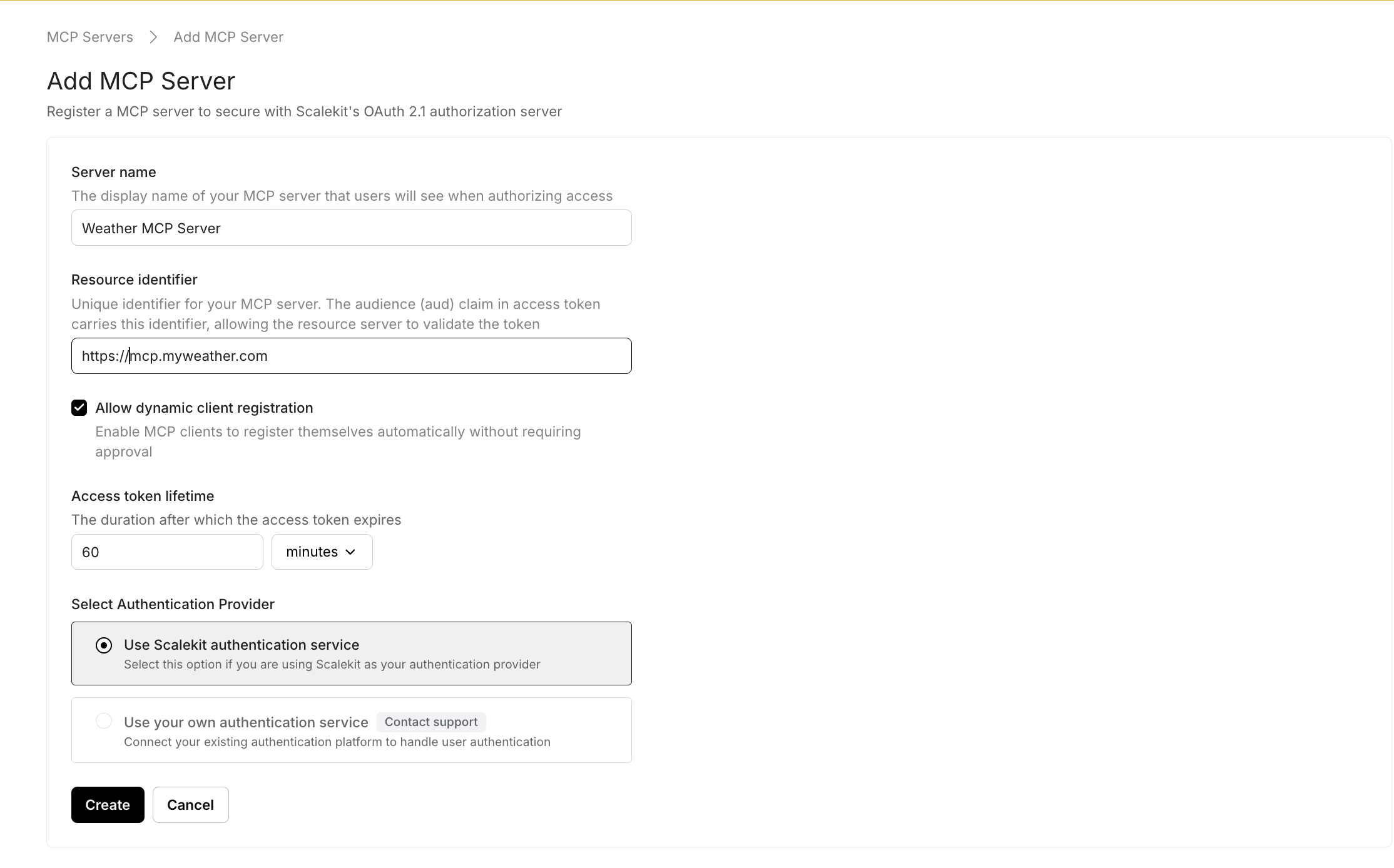
What’s included
OAuth 2.1 Authorization Server
Scalekit provides the full flow: discovery endpoints, token issuance, client registration, and scope enforcement.
Dynamic Client Registration
Agents can onboard automatically without manual client ID provisioning.
Granular Scopes for Tools and Data
Control access to individual tools or datasets using scoped tokens like mcp:tools:weather or mcp:resources:db:read.
Audit Logging
All access is logged for compliance and traceability.
Works with any MCP Server
You don’t need to build an auth stack from scratch or adopt a full identity provider. Drop Scalekit into your existing MCP-compatible server, define scopes, and start verifying tokens. All endpoints follow OAuth 2.1 standards.
Get Started
Use Scalekit’s hosted OAuth server or embed it alongside your MCP server.
You’ll find:
- Quickstart examples for OAuth code and client credentials flows
- Drop-in support for PKCE and token validation
- Preconfigured scopes and token lifetimes
Get started for free. Learn more with MCP docs.





